EasyEmailSuite is a browser extension made by MyWay that may come bundled with other free software that you download off of the Internet. When installed EasyEmailSuite will set the homepage and search engine for your web browser to http://search.myway.com.
EasyEmailSuite is an application that allows users to access their emails. Initially, this app may seem legitimate and useful, however, EasyEmailSuite is categorized as a browser hijacker.
This extension changes your home page and searches engine to MyWay. It monitors your search activity and collects data, that is later sold/forwarded to display additional unwanted ads in your browser. Several anti-virus scanners have classified EasyEmailSuite as a Browser Hijacker / PUP and are therefore not recommended to keep on your computer.
About Browser Hijackers
Browser hijacking is a common type of internet fraud where your web browser settings are altered to allow it to carry out things you don’t intend. They are designed to disrupt browser functions for several reasons. Usually, it will drive users to particular sites which are trying to increase their advertisement earnings. While it might seem harmless, these tools are made by malicious individuals who always attempt to take full advantage of you, so that they could earn money from your naivety and distraction. They not only screw up your internet browsers, but browser hijackers could also modify the system registry to make your computer vulnerable to other malicious programs.
Symptoms of browser hijacker infection
There are plenty of symptoms that indicate your internet browser has been highjacked:
1. the home page of your web browser is changed unexpectedly
2. bookmark and the new tab are likewise changed
3. the default web browser settings are modified and/or your default web engine is altered
4. you see unsolicited new toolbars added
5. you may notice never-ending pop-up adverts on your screen
6. websites load very slowly and often incomplete
7. you are blocked to access the websites of security solution providers.
Exactly how they get into your computer
Browser hijackers infect computer systems via malicious e-mail attachments, downloaded infected computer files, or by visiting infected sites. They can also come from any BHO, extension, add-on, toolbar, or plug-in with malicious objectives. Other times you might have mistakenly accepted a browser hijacker as part of a software program bundle (generally freeware or shareware). Some of the most popular hijackers are EasyEmailSuite, Babylon Toolbar, Conduit Search, Sweet Page, OneWebSearch, and CoolWebSearch.
Browser hijackers will interrupt the user’s browsing experience significantly, keep track of the websites frequented by users and steal private information, cause difficulty in connecting to the web, and then finally create stability issues, causing software programs and computers to freeze.
Browser hijacker removal methods
Some hijackers could be removed by uninstalling the freeware they were included with or by removing any add-ons you have recently added to your PC. However, many hijacking codes are not very easy to get rid of manually, since they go deeper into the operating system. You should think about undertaking manual fixes only if you happen to be a tech-savvy person, as risks are associated with tinkering with the system registry and HOSTS file.
Experts always recommend users remove any malware including browser hijacker with an automatic malware removal tool, which is easier, safer, and quicker than the manual removal procedure. Safebytes Anti-Malware discovers all kinds of hijackers – such as EasyEmailSuite – and eliminates every trace efficiently and quickly. Along with anti-malware, a PC optimizer tool can help you resolve Windows registry errors, eliminate unwanted toolbars, secure online privacy, and stabilize programs installed on the computer.
Help! Malware Blocking Antivirus Installation And Access To The Web
Malware could cause several different types of damage to PCs, networks, and data. Some malware sits in between your computer and the internet connection and blocks a few or all internet sites which you want to visit. It will also prevent you from adding anything to your PC, especially anti-virus software. If you are reading this article, odds are you’re stuck with a virus infection that is preventing you to download or install the Safebytes Anti-Malware program on your PC. There are some options you can try to get around with this obstacle.
Install the anti-malware in Safe Mode
If the virus is set to load automatically when Windows starts, getting into Safe Mode could block this attempt. Since only the minimal programs and services start-up in “Safe Mode”, there are hardly any reasons for issues to take place. To start your Windows XP, Vista, or 7 computers in Safe Mode with Networking, do as instructed below.
1) Tap the F8 key continuously as soon as your computer boots, but before the big Windows logo shows up. This would conjure up the “Advanced Boot Options” menu.
2) Select Safe Mode with Networking with arrow keys and press Enter.
3) When this mode loads, you will have the internet. Now, make use of your browser to download and install an anti-malware application.
4) Immediately after installation, do a full scan and let the software remove the threats it detects.
Utilize an alternate internet browser to download the anti-malware application
Some malware only targets certain web browsers. If this sounds like your case, utilize another web browser as it may circumvent the virus. The best solution to avoid this issue is to opt for an internet browser that is well known for its security measures. Firefox contains built-in Phishing and Malware Protection to keep you secure online.
Install antivirus on a flash drive
Here’s yet another solution which is using a portable USB anti-malware software package that can check your system for viruses without the need for installation. To run anti-virus using a USB flash drive, follow these simple steps:
1) Download the anti-malware on a virus-free PC.
2) Put the USB drive into the uninfected computer.
3) Double click on the downloaded file to open the installation wizard.
4) Select flash drive as the place when the wizard asks you exactly where you wish to install the application. Follow the directions to finish the installation process.
5) Transfer the thumb drive from the clean PC to the infected PC.
6) Double-click the EXE file to open the Safebytes software right from the thumb drive.
7) Click on “Scan Now” to run a complete scan on the infected computer for malware.
If no other method of downloading and installing antivirus software works, then you’ve got no other choice than to hit the last resort: a complete Windows reinstallation, the only solution proven to have a 100% rate of success at virus removal. If you’re not sure which method to employ, simply call our toll-free number 1-844-377-4107 to speak to our technical support team. Our experts can take you step-by-step through the virus removal process on the phone and also fix your personal computer remotely.
A Look at the Best AntiMalware Program
These days, an anti-malware program can protect your PC from various types of online threats. But exactly how to choose the best one amongst plenty of malware protection software that is available out there? You may be aware, there are many anti-malware companies and products for you to consider. Some are good ones, some are ok types, while some are merely bogus anti-malware programs that can harm your computer themselves! When searching for antivirus software, choose one which provides dependable, efficient, and complete protection against all known computer viruses and malware. When considering commercial anti-malware software options, the majority of people opt for well-known brands, like SafeBytes, and they are very happy with it.
SafeBytes anti-malware is a very effective and user-friendly protection tool that is made for end-users of all levels of computer literacy. Once you have installed this application, SafeByte's sophisticated protection system will ensure that no viruses or malicious software can seep through your computer.
SafeBytes anti-malware takes PC protection to a totally new level with its advanced features. The following are some typical features found in this program:
Most effective AntiMalware Protection: Safebytes is based on the very best virus engine within the industry. These engines can find and get rid of threats even during the early phases of a malware outbreak.
Real-time Threat Response: SafeBytes provides round-the-clock protection for your PC restricting malware attacks instantly. It’ll constantly monitor your laptop or computer for hacker activity and also gives end-users superior firewall protection.
High-Speed Malware Scanning Engine: SafeBytes Anti-Malware has a multi-thread scan algorithm that works up to 5x faster than any other protection software.
Web Filtering: SafeBytes provides an instant safety rating to the web pages you’re about to check out, automatically blocking dangerous sites and ensuring that you’re certain of your safety while browsing the net.
Light-weight: SafeBytes is a lightweight and simple to use antivirus and antimalware solution. Since it utilizes minimum computer resources, this tool leaves the computer’s power exactly where it belongs to: with you actually.
24/7 Live Expert Support: You can get high levels of support around the clock if you are using their paid version.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove EasyEmailSuite without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by EasyEmailSuite

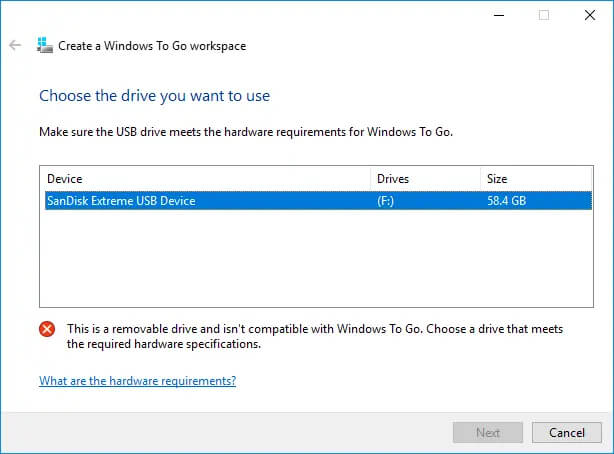 Many Linux users if not all of them can run their distros from a USB drive but did you know you can run Windows 10 from a USB drive as well?
Microsoft has introduced all the way back to Windows 8 one feature called Windows To Go and it kept it in Windows 8.1 and in Windows 10 as well.
This feature is intended as a convenient way for workers to carry their corporate environments with them, but having your own copy of Windows on a thumb drive could be handy for backup purposes, too, or if you frequently use public machines that lack your preferences/applications or that have a restricted OS.
Many Linux users if not all of them can run their distros from a USB drive but did you know you can run Windows 10 from a USB drive as well?
Microsoft has introduced all the way back to Windows 8 one feature called Windows To Go and it kept it in Windows 8.1 and in Windows 10 as well.
This feature is intended as a convenient way for workers to carry their corporate environments with them, but having your own copy of Windows on a thumb drive could be handy for backup purposes, too, or if you frequently use public machines that lack your preferences/applications or that have a restricted OS.


