When we purchase a computer, usually it is meant to be used by one person. Sometimes we would like to share our computer with other people, with friends and family members but we would also like to keep some privacy for ourselves in the process. Lucky for us Windows 10 will let us create multiple user accounts which then can be used by other persons with their own settings, documents, etc. The only requirement is to already have one user account which is automatically created when Windows is installed.
This guide will lead you step by step in the creation of a new user account within Windows 10, so grab your favorite drink, and let's begin.
First thing is to click on the windows icon on the bottom left and open start menu, from start menu click once on settings.
![]() When the settings window opens, choose ACCOUNTS on it.
When the settings window opens, choose ACCOUNTS on it.
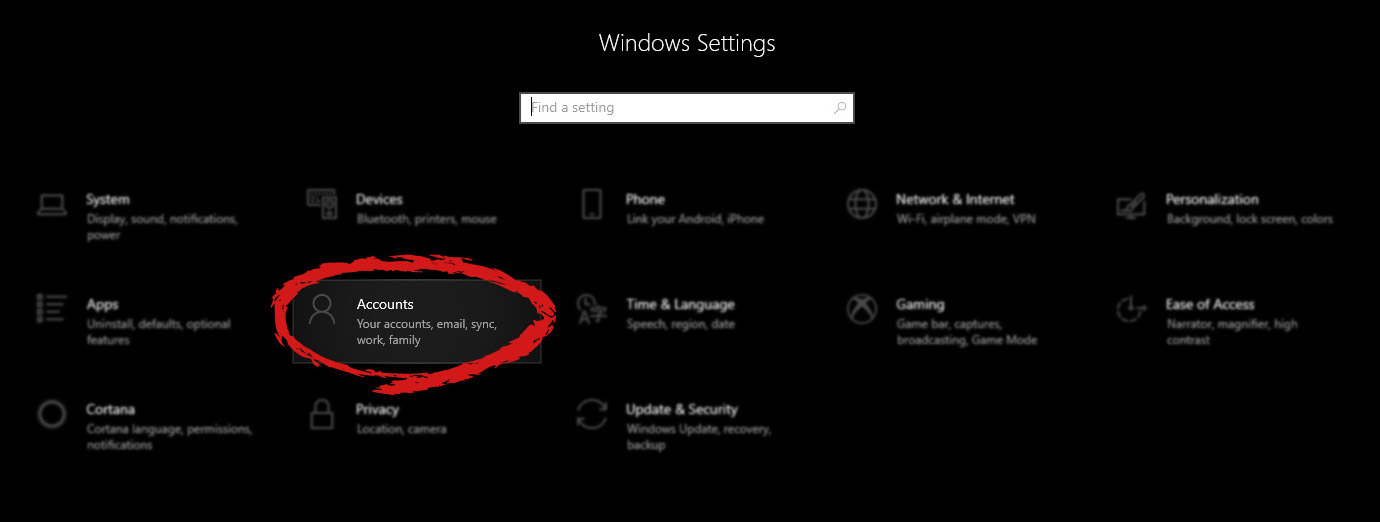 Windows will then go to the accounts settings page. Within that page, click on the Family & other users to open the setting for the chosen section on right. On the right settings, screen navigate to the lower section and click once with the left button on add someone else to this PC
Windows will then go to the accounts settings page. Within that page, click on the Family & other users to open the setting for the chosen section on right. On the right settings, screen navigate to the lower section and click once with the left button on add someone else to this PC
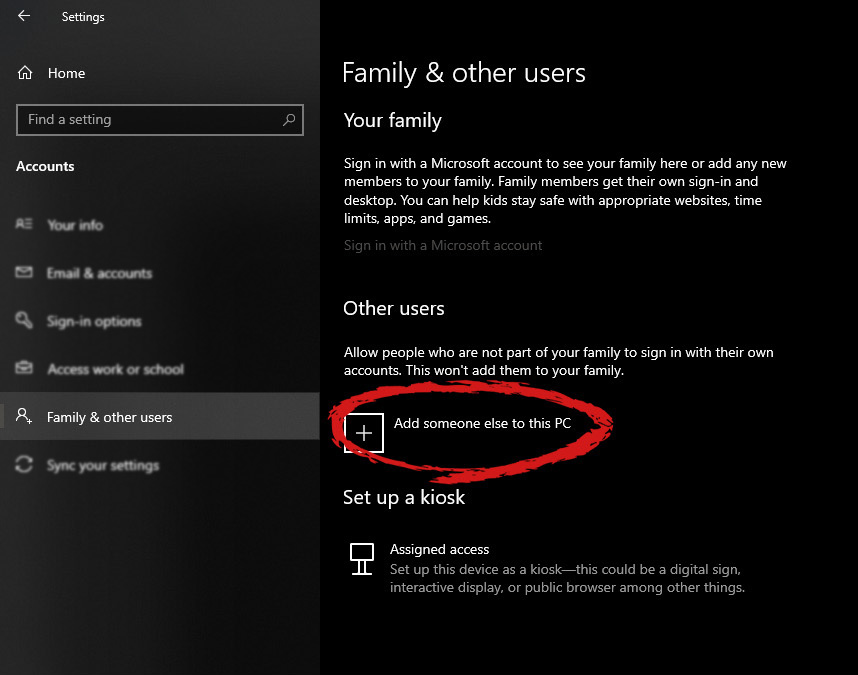 When add someone else to this PC is clicked, pop up window will appear which will ask you to provide the persons email address and later on the password of his/her Microsoft account, after the required information is provided you are done, a new user has been added and he can use his Microsoft credentials on the login screen to use this computer.
When add someone else to this PC is clicked, pop up window will appear which will ask you to provide the persons email address and later on the password of his/her Microsoft account, after the required information is provided you are done, a new user has been added and he can use his Microsoft credentials on the login screen to use this computer.
However, if you do not wish to add a new user via his Microsoft login credentials or the person does not have them, on the pop-up window click on I don't have this person's sign-in information.
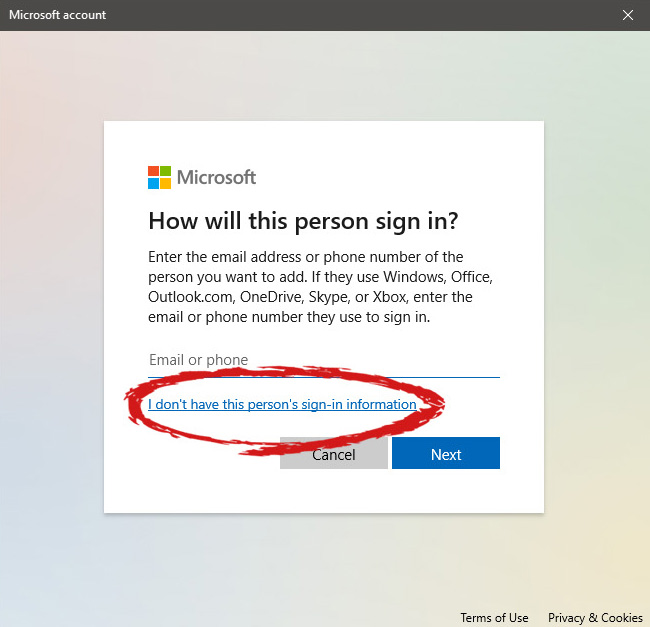 This will open yet another pop-up giving you the option to create a Microsoft account for this person, to use a phone number instead of a Microsoft account, or to create a new email address for the user. Any of these options will create a new user for this computer with provided credentials but there is the last option at bottom of the pop-up which will allow you to create a local user only without a Microsoft account. This user will be able to use this computer, will not be able to transfer his document through various devices like he/she would if using a valid Microsoft account but it could use the computer and personalize it fully to his/her liking.
This will open yet another pop-up giving you the option to create a Microsoft account for this person, to use a phone number instead of a Microsoft account, or to create a new email address for the user. Any of these options will create a new user for this computer with provided credentials but there is the last option at bottom of the pop-up which will allow you to create a local user only without a Microsoft account. This user will be able to use this computer, will not be able to transfer his document through various devices like he/she would if using a valid Microsoft account but it could use the computer and personalize it fully to his/her liking.
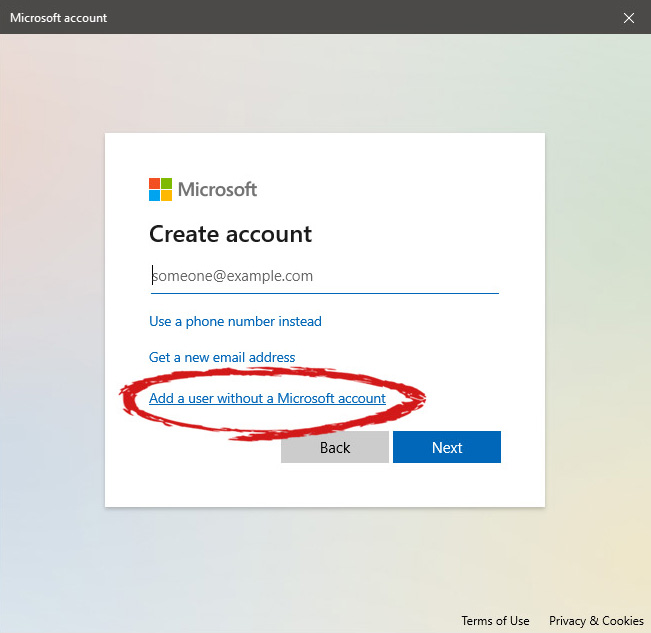 Once the link is clicked, you will be presented with a floating window requiring you to input needed information in order for the account to be created. You will need to provide username, password, and answers to 3 security questions.
Once the link is clicked, you will be presented with a floating window requiring you to input needed information in order for the account to be created. You will need to provide username, password, and answers to 3 security questions.
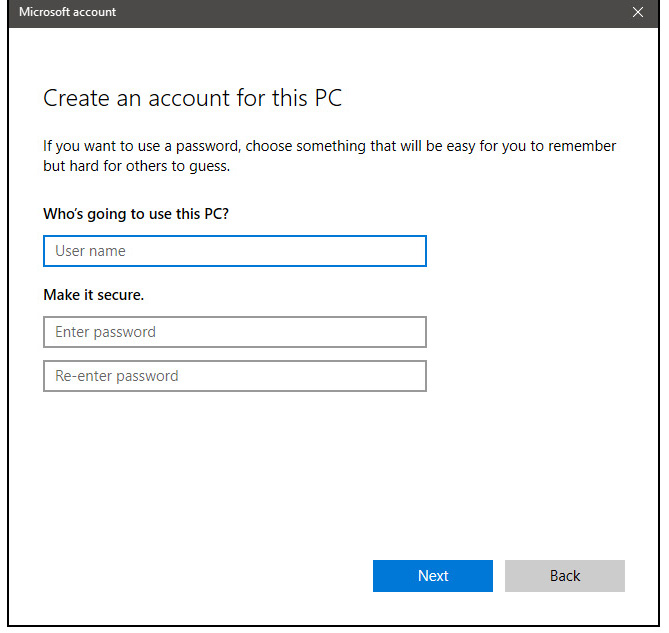 Once all information has been provided, click on next and your new non-Microsoft local user has been created. Now when you click on Family & other users you will see that Windows has added a new user with the provided name to this computer. If you wish, you can add another user in the same manner, following the previous steps. Microsoft Windows does not have a limit for how many users can be on one computer so feel free to create as many as you like.
Once all information has been provided, click on next and your new non-Microsoft local user has been created. Now when you click on Family & other users you will see that Windows has added a new user with the provided name to this computer. If you wish, you can add another user in the same manner, following the previous steps. Microsoft Windows does not have a limit for how many users can be on one computer so feel free to create as many as you like.
Now, clicking on the existing created user will open user options. From there you will have options to remove the user, therefore removing him/her from this computer, note that removing the local user will remove permanently his/her settings and they would not be able to be restored, or you can change the user account type.
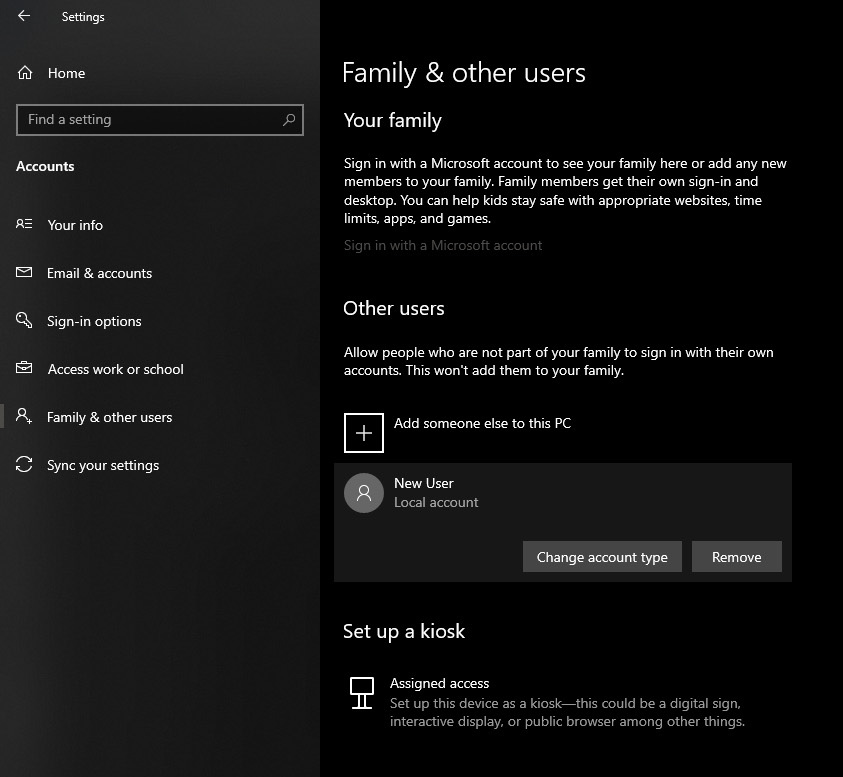 Click on Change account type.
Click on Change account type.
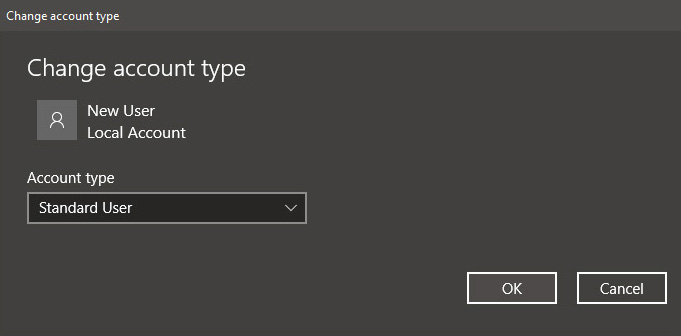 Under account type, you will have the option to promote this user to an administrator if you wish or you can leave it as a standard user.
Under account type, you will have the option to promote this user to an administrator if you wish or you can leave it as a standard user.

FindGoFind is a browser extension for Google Chrome.Developers present findgofind.com as an improved Internet search engine that supposedly enhances the Internet browsing experience by generating better search results. These claims often trick users into believing that findgofind.com is legitimate and useful. In fact, developers promote this site using deceptive software download/installation set-ups that hijack web browsers and modify various options without permission. Furthermore, findgofind.co continually records various data relating to users’ Internet browsing activity.
While this extension is installed, users will see additional unwanted ads throughout their browsing sessions. Furthermore, this extension changed the default search engine to FindGoFind to easier display Sponsored content.
Your version of Windows 10 would reach the end of service soon, Click to download a newer version of Windows 10 to stay supported. or An unsupported version of Windows will no longer receive software updates from Windows Update. These updates include security updates that can help protect your PC from harmful viruses, spyware, and other malicious software which can steal your personal information. Windows Update also installs the latest software updates to improve the reliability of Windows—such as new drivers for your hardware.and you are unable to perform updates then this guide is for you. There are several things you can do to fix this issue presented here, it is advisable to follow them in a way how they are presented for best performance and system safety.
Loving Windows 11 so far? We sure are. Microsoft has clearly decided to take its OS to the next level and keeps showing it through every update. It makes you wonder what’s next - and today, you’ll find out!
Tons of new features have been leaked, and we can probably expect them with the 23H2 update. Here’s everything you need to know so far.

There are plenty of new features already confirmed for Windows 11. The only issue is we don’t know for sure if they’re coming with the 23H2 update or separately, at a different time. Whatever the case, a lot of them are pretty exciting.
Here’s an overview of what we might be getting this fall.
Another is AI-generated keywords, designed to improve the discoverability of apps you’re searching for. Moreover, the AI-generated review summary is designed to give us a simpler experience looking at reviews. Huge numbers of reviews will be compiled into a summary that’s easy to scan and lets us discover new content faster.
We’ve got some interesting stuff to look forward to with the next major Windows 11 update. And these are just the things the Internet’s actually heard of, so who knows what else Microsoft might be planning? It remains to be seen, hopefully just a few months from now. 23H2 has been released on October 31st.