RelevantKnowledge is a potentially unwanted program. It is typically bundled by 3rd-party installers and download managers that include other potentially unwanted programs (PUPs). In most cases, the installer will present the user with an RK survey at the end of the setup in order to relate the user’s future behavior to various questions.
From the published: RelevantKnowledge is an online market research community consisting of over 2 million members worldwide, which provides insight into how its members interact with the Internet. In exchange for an agreement to have their Internet behavior monitored, computer users who join RelevantKnowledge are offered various value propositions, including the ability to download screensavers or other software offerings, entry into sweepstakes, and a host of other benefits.
Multiple anti-virus scanners have detected possible malware in RelevantKnowledge.
About Browser Hijackers
If you’ve ever downloaded software via the internet (shareware, freeware, etc,), it’s quite possible you’ve unintentionally installed unwanted programs on your PC. Potentially Unwanted Programs (PUP), also referred to as Potentially Unwanted Applications (PUA), are applications that you never wanted in the first place and often come bundled with freeware. Once installed, the majority of these applications can be tough to get rid of and become much more of an annoyance rather than a necessity.
It is clear by its name – unwanted applications – but did not really constitute “malware” in the traditional sense. This is because, the majority of PUPs get into a computer not because they slip through the security holes, for instance, but because the users have got installed them themselves – 100 % unknowingly needless to say. A PUP might not be regarded as malicious or dangerous but nevertheless, it is a common reason for clunky OSs; some PUPs are a lot more aggressive by deliberately slowing down your PC.
The harm unwanted programs could do
PUPs come in various forms. Typically, they could be seen in adware bundlers that are known to use aggressive and misleading advertising. The majority of bundlers install many adware programs from a number of vendors, each of which features its own EULA policy. Safebytes Anti-Malware totally eradicates this threat and safeguards your computer against PUP or adware infection. Additionally, the majority of free programs nowadays come with a few unwanted add-ons; in most cases a web browser toolbar or browser modification such as a homepage hijacker. They can modify browser settings, change the default search engine, replace the default home page with their own websites, slow down internet speed, and also will damage your system as well.
PUPs carry a dangerous bite if left unchecked. The most detrimental part of installing a PUP is the spyware, adware, and keystroke loggers that might hide inside. These are programs that don’t really do anything good for you; in addition to taking up space on your hard disk drive, they also slow down your PC, often modify settings without your authorization, the list of frustrating features goes on and on.
Tips on how to avoid getting a PUP
• When installing anything on your personal computer, always study the fine print, including the license agreement. Do not accept terms of use that are for bundled programs.
• Use ONLY custom or manual install method – and never thoughtlessly click Next, Next, Next.
• Use good antimalware software, such as Safebytes Anti-Malware which offers real-time protection against PUPs.
• Think carefully before you download any kind of shareware or freeware. Turn off or get rid of toolbars and browser extensions you don’t actually need.
• Always download applications from the original website. The majority of PUPs find their way onto your laptop or computer is via download portals, so steer clear of it entirely.
What To Do If You Cannot Install Safebytes Anti-Malware?
Viruses may cause a lot of damage to your personal computer. Some malware is meant to interfere with or block things that you want to do on your computer system. It may well not allow you to download anything from the net or stop you from accessing some or all websites, particularly the anti-malware sites. If you are reading this article now, you’ve probably realized that virus infection is the real cause of your blocked internet connectivity. So how to proceed if you need to download and install an anti-malware program like Safebytes? Although this kind of problem can be harder to get around, there are a few actions you can take.
Download the application in Safe Mode with Networking
In Safe Mode, you may change Windows settings, un-install or install some applications, and remove hard-to-delete viruses. If the malware is set to load automatically when the computer starts, shifting to this mode can prevent it from doing so. To start the computer into Safe Mode, press the “F8” key on your keyboard just before the Windows boot screen appears; Or right after normal Windows boot up, run MSCONFIG, look over “Safe Boot” under Boot tab, and then click Apply. As soon as you reboot into Safe Mode with Networking, you can download, install, and update anti-malware software from there. Right after installation, run the malware scanner to eliminate standard infections.
Use an alternate web browser to download antivirus software
Web-based viruses could be environment-specific, aiming for a specific internet browser or attacking specific versions of the browser. The most effective solution to overcome this problem is to go with a browser that is well known for its security measures. Firefox has built-in Phishing and Malware Protection to keep you secure online.
Install anti-malware on a USB drive
Another option is to save and operate an antivirus software tool entirely from a Flash drive. Do these simple actions to clean up your infected PC using a portable antivirus.
1) On a virus-free computer, download and install Safebytes Anti-Malware.
2) Insert the USB drive into the clean PC.
3) Double click on the downloaded file to open the installation wizard.
4) Select the drive letter of the flash drive as the location when the wizard asks you exactly where you would like to install the antivirus. Follow the directions to complete the installation process.
5) Transfer the thumb drive from the uninfected computer to the infected PC.
6) Double-click the Safebytes Anti-malware icon on the pen drive to run the application.
7) Simply click “Scan Now” to run a complete scan on the affected computer for malware.
Protect Your Computer & Privacy With SafeBytes Anti-Malware
Want to download the best anti-malware software program for your laptop? There are lots of applications on the market that comes in free and paid versions for Windows systems. A few are really worth your money, but many aren’t. You need to pick a tool that has got a good reputation and detects not only computer viruses but other types of malware also. Among few good applications, SafeBytes Anti-Malware is the highly recommended program for the security-conscious individual.
SafeBytes antimalware is a highly effective and user-friendly protection tool that is suitable for end-users of all levels of IT literacy. After you have installed this application, SafeByte's sophisticated protection system will make sure that no viruses or malware can seep through your PC.
SafeBytes has excellent features when compared to other anti-malware programs. Here are some popular features present in this tool:
World-class AntiMalware Protection: Safebytes is made on the best virus engine within the industry. These engines will detect and remove threats even during the early stages of a malware outbreak.
Real-time Active Protection: SafeBytes delivers complete and real-time security for your laptop or computer. They’re highly efficient in screening and getting rid of numerous threats because they’re constantly revised with the latest updates and safety measures.
Internet Security: Through its unique safety score, SafeBytes informs you whether a site is safe or not to visit it. This will ensure that you’re always certain of your safety when browsing the net.
Very Low CPU and Memory Usage: This program is not “heavy” on the computer’s resources, so you will not notice any overall performance difficulties when SafeBytes is operating in the background.
24/7 Online Technical Support: SafeBytes provides 24/7 technical support, automatic maintenance, and upgrades for the best user experience.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove RelevantKnowledge without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by RelevantKnowledge
Files:
File%COMMONPROGRAMSRelevantKnowledgeAbout RelevantKnowledge.lnk.
File%COMMONPROGRAMSRelevantKnowledgePrivacy Policy and User License Agreement.lnk.
File%COMMONPROGRAMSRelevantKnowledgeSupport.lnk.
File%COMMONPROGRAMSRelevantKnowledgeUninstall Instructions.lnk.
File%PROGRAMFILESRelevantKnowledgechrome.manifest.
File%PROGRAMFILESRelevantKnowledgecomponentsrlxg.dll.
File%PROGRAMFILESRelevantKnowledgecomponentsrlxh.dll.
File%PROGRAMFILESRelevantKnowledgecomponentsrlxi.dll.
File%PROGRAMFILESRelevantKnowledgecomponentsrlxj.dll.
File%PROGRAMFILESRelevantKnowledgeinstall.rdf.
File%PROGRAMFILESRelevantKnowledgerlcm.crx.
File%PROGRAMFILESRelevantKnowledgerlcm.txt.
File%PROGRAMFILESRelevantKnowledgerlls.dll.
File%PROGRAMFILESRelevantKnowledgerlls64.dll.
File%PROGRAMFILESRelevantKnowledgerloci.bin.
File%PROGRAMFILESRelevantKnowledgerlph.dll.
File%PROGRAMFILESRelevantKnowledgerlservice.exe.
File%PROGRAMFILESRelevantKnowledgerlvknlg.exe.
File%PROGRAMFILESRelevantKnowledgerlvknlg64.exe.
File%PROGRAMFILESRelevantKnowledgerlxf.dll.
Directory %COMMONPROGRAMSRelevantKnowledge.
Directory %PROGRAMFILESRelevantKnowledgecomponents.
Directory %PROGRAMFILESRelevantKnowledge.
Registry:
Key mkndcbhcgphcfkkddanakjiepeknbgle at HKEY_LOCAL_MACHINESOFTWAREGoogleChromeExtensions.
Key RelevantKnowledge at HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogonNotify.
Key rlvknlg at HKEY_LOCAL_MACHINESOFTWAREMicrosoftESENTProcess.
Value 3C5F0F00-683D-4847-89C8-E7AF64FD1CFB at HKEY_LOCAL_MACHINESOFTWAREMozillaFirefoxExtensions.
Value %PROGRAMFILESrelevantknowledgerlvknlg.exe at HKEY_LOCAL_MACHINESYSTEMControlSet001ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.
Value %PROGRAMFILESrelevantknowledgerlvknlg.exe at HKEY_LOCAL_MACHINESYSTEMControlSet002ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.
Value %PROGRAMFILESRelevantKnowledgerlvknlg.exe at HKEY_LOCAL_MACHINESYSTEMControlSet003ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.
 Windows 11 has brought some bad reviews for its inability to change the taskbar location to the screen. Luckily we can still hide it if needed.
In order to hide the taskbar from the screen follow these simple instructions:
Windows 11 has brought some bad reviews for its inability to change the taskbar location to the screen. Luckily we can still hide it if needed.
In order to hide the taskbar from the screen follow these simple instructions:


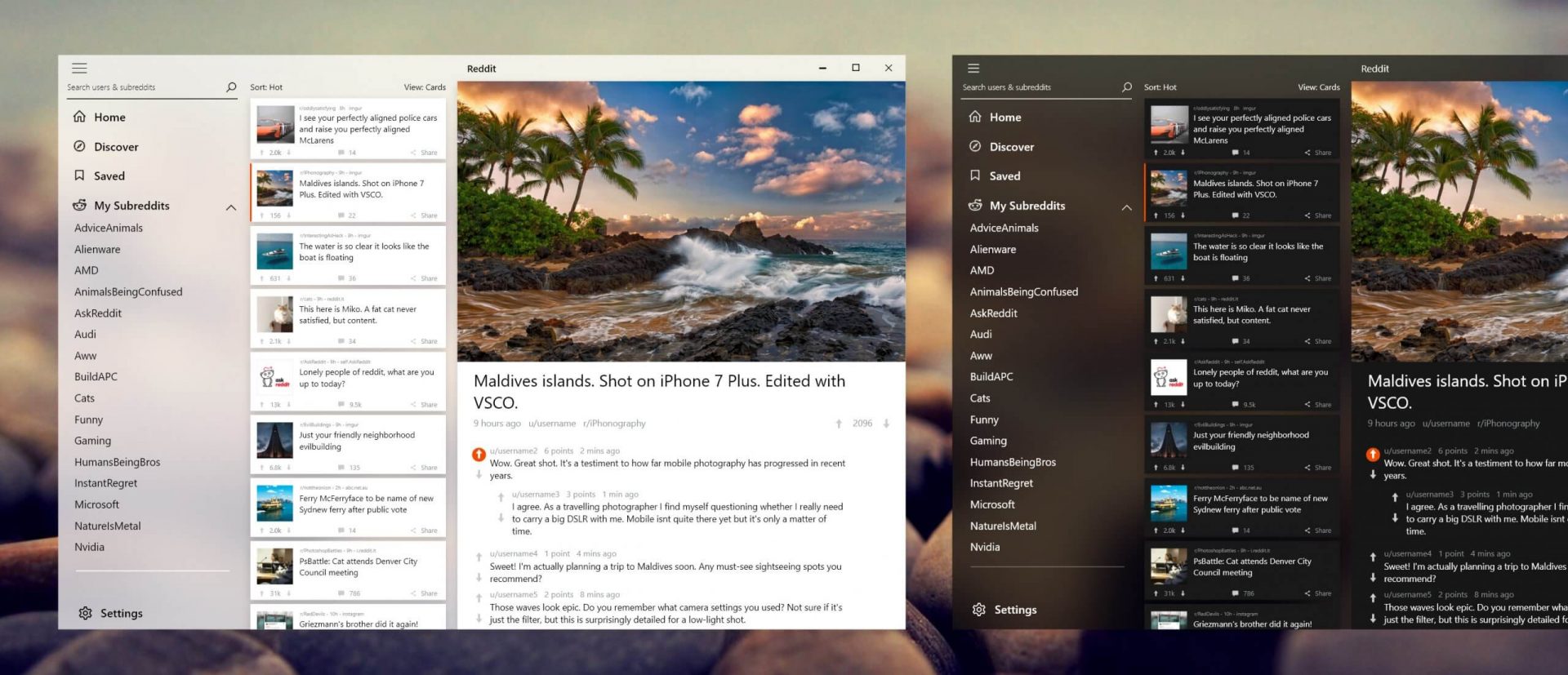 Reddit is one of the most popular websites in the world and how Microsoft is opening doors to everyone in its new store Reddit took a logical step and made a Progressive web application and placed it in it.
Being a Progressive web app makes it more familiar and feels like a home experience using it for a lot of Reddit users.
Reddit itself has a large community and active topics discussions all the time about anything. Bringing it to Windows as an application is, in my opinion, a great move since as an application it is independent, more light-weighted, and offering some other advantages specifically tied to being a standalone windows application.
Everyone familiar with and using the Reddit website will feel right at home in this app and you can start using it right away.
Reddit is one of the most popular websites in the world and how Microsoft is opening doors to everyone in its new store Reddit took a logical step and made a Progressive web application and placed it in it.
Being a Progressive web app makes it more familiar and feels like a home experience using it for a lot of Reddit users.
Reddit itself has a large community and active topics discussions all the time about anything. Bringing it to Windows as an application is, in my opinion, a great move since as an application it is independent, more light-weighted, and offering some other advantages specifically tied to being a standalone windows application.
Everyone familiar with and using the Reddit website will feel right at home in this app and you can start using it right away. 