CrazyForCrafts is a Browser Extension from Mindspark Interactive. This Toolbar Extension allegedly offers users tons of DIY crafting guides and tricks, however all that it does is point you in the right direction. It links you back to some of the most popular DIY Crafting websites on the internet that you can find at any time by a simple search.
While this may look useful and faster than looking around the internet for good DIY projects, remember that this extension injects itself into your browser, changing your new tab page to Search.MyWay.com and records your browsing habits, can view your internet history, and know whatever you are looking for or viewing online.
While using this extension you will see additional pop-up ads, sponsored content, and injected ads throughout your browsing sessions.
Due to its behavior this extension has been marked for removal by several anti-virus scanners, and it is recommended to remove it from your computer to prevent data leaks.
About Browser Hijackers
Browser hijackers (sometimes called hijackware) are a type of malicious software that alters web browser configuration settings without the computer owner’s knowledge or permission. These hijacks appear to be increasing at an worrying rate around the world, and it can be really nefarious and sometimes dangerous too. They’re designed to disrupt browser functions for many different reasons. These are typically used to force visitors to a specific website, manipulating web-traffic to earn ad revenue. Although it might appear naive, all browser hijackers are damaging and therefore always classified as security threats. In a much worst case, your internet browser could be hijacked to download malware that will do a great deal of damage to your computer or laptop.
How one can know whether the browser is hijacked?
Symptoms that a web browser is hi-jacked include: the browser’s homepage is changed; new bookmarks pointing to pornographic sites have been added to your favorite pages; the essential web browser settings are modified and unwanted or insecure sites are added to the trusted websites listing; you are finding new toolbars you have never found before; you might see numerous pop-up ads on your computer screen; your browser has become unstable or starts running sluggishly; Inability to navigate to certain sites, especially antivirus as well as other computer security software websites.
How browser hijacker infects computers
Browser hijackers may use drive-by downloads or file-sharing websites or perhaps an e-mail attachment to reach a targeted PC. They also come from add-on software, also called browser helper objects (BHO), browser extensions, or toolbars. Also, certain freeware and shareware can put the hijacker in your PC through “bundling”. Examples of well-known browser hijackers are Fireball, CoolWebSearch. GoSave, Ask Toolbar, RocketTab, and Babylon Toolbar.
The presence of any browser hijacker on your system might substantially diminish the web browsing experience, track your online activities that result in serious privacy concerns, develop system stability problems and eventually cause your computer to slow down or to an almost unusable condition.
How to remove a browser hijacker
Some hijackers can be easily removed by uninstalling the free software they were included with or by removing any extension you’ve recently added to your browser. But, most hijacking codes are certainly not very easy to get rid of manually, as they go much deeper into your operating system. You should consider performing manual repairs only if you’re a tech-savvy person, as potential risks are associated to tinkering with the system registry and HOSTS file.
Browser hijackers could be effectively removed by installing anti-malware software on the affected system. SafeBytes Anti-Malware can counter relentless browser hijackers and provide you with proactive PC protection against all kinds of malware. In addition to anti-virus software, a system optimizer software, like Total System Care, will help you correct Windows registry errors, remove unwanted toolbars, secure online privacy, and stabilize software programs installed on your PC.
Virus Blocking Access To Safebytes Website And Anti-Malware Downloads - What You Should Do?
Malware can cause all kinds of damage once they invade your PC, ranging from stealing your private details to deleting files on your PC. Some malware is meant to interfere with or prevent things that you wish to do on your PC. It may well not allow you to download anything from the net or it will stop you from accessing a few or all internet sites, especially the anti-malware sites. If you’re reading this, odds are you’re stuck with a malware infection which is preventing you to download or install Safebytes Anti-Malware program on your system. Although this type of issue will be difficult to get around, there are a few steps you can take.
Get rid of malware in Safe Mode
The Windows-based PC has a special mode referred to as “Safe Mode” in which only the minimum required applications and services are loaded. In the event the malware is blocking access to the internet and affecting your computer, starting it in Safe Mode enables you to download antivirus and run a scan while limiting potential damage. To enter into Safe Mode or Safe Mode with Networking, press the F8 key while the computer is booting up or run MSCONFIG and locate the “Safe Boot” options under the “Boot” tab. As soon as you restart the PC into Safe Mode with Networking, you may download, install, as well as update anti-malware software from there. Following installation, run the malware scanner to eliminate standard infections.
Obtain the antivirus software using an alternate web browser
Malicious code could exploit vulnerabilities on a particular browser and block access to all anti-virus software websites. If you appear to have a virus attached to Internet Explorer, then switch over to a different browser with built-in safety features, such as Firefox or Chrome, to download your favorite anti-malware program – Safebytes.
Make a bootable USB anti-virus drive
Here’s yet another solution which is using a portable USB anti-malware software package that can check your computer for malicious software without needing installation. To run anti-malware using a USB drive, follow these simple steps:
1) Download the anti-malware on a virus-free PC.
2) Plug the Flash drive into the uninfected computer.
3) Double click on the exe file to run the installation wizard.
4) Choose the drive letter of the pen drive as the place when the wizard asks you where you would like to install the antivirus. Follow activation instructions.
5) Remove the pen drive. You can now utilize this portable anti-malware on the affected computer system.
6) Run the Safebytes Anti-malware directly from the pen drive by double-clicking the icon.
7) Click “Scan Now” to run a complete scan on the infected computer for malware.
Features of SafeBytes Anti-Malware
If you are planning to buy anti-malware for your computer system, there are lots of brands and packages for you to consider. A few of them are great, some are ok types, and some will destroy your computer themselves! You have to be careful not to select the wrong application, especially if you buy a paid software. Amongst few good applications, SafeBytes Anti-Malware is the highly recommended tool for security-conscious people.
SafeBytes antimalware is a very effective and easy to use protection tool which is designed for end-users of all levels of computer literacy. With its cutting edge technology, this software will help you get rid of multiples types of malware which includes viruses, worms, PUPs, trojans, adware, ransomware and browser hijackers.
SafeBytes anti-malware takes PC protection to a whole new level with its enhanced features. A few of them are given as below:
Real-time Threat Response: SafeBytes offers complete and real-time security for your personal machine. This utility will constantly keep track of your PC for any suspicious activity and updates itself regularly to keep abreast of the latest threats.
World-class AntiMalware Protection: Using its advanced and sophisticated algorithm, this malware elimination tool can identify and get rid of the malware threats hiding in your computer effectively.
Web protection: SafeBytes checks the hyperlinks present on a web page for possible threats and alerts you if the website is safe to view or not, through its unique safety rating system.
Lightweight: SafeBytes is lightweight software. It use up a very small amount of processing power as it works in the background so you’re free to use your Windows-based PC the way you would like.
24/7 Support: You can get totally free 24/7 technical assistance from their computer experts on any product queries or computer security issues.
Overall, SafeBytes Anti-Malware is a solid program since it has plenty of features and could detect and remove any potential threats. Now you may realize that this tool does more than just scan and delete threats from your PC. For the best protection and the best value for money, you can’t get better than SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
To get rid of CrazyForCrafts manually, navigate to the Add/Remove programs list in the Control Panel and choose the offending program you want to get rid of. For web browser plug-ins, go to your web browser’s Addon/Extension manager and select the plug-in you want to remove or disable. It is also suggested to reset your browser to its default condition to fix corrupt settings.
If you choose to manually delete the system files and registry entries, use the following checklist to make sure you know exactly what files to remove before undertaking any actions. Please keep in mind that this is for skilled users only and might be challenging, with incorrect file removal leading to additional system errors. Additionally, certain malicious programs have the capability to defend against its deletion. Completing this task in Safe Mode is advised.
Registry:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesWpm
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain Default_Page_URL
HKEY_LOCAL_Machine\Software\Classes\[adware name]
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run .exe
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\run\random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings CertificateRevocation = 0
 Good thing is that website or web application will prompt you to allow it to use this feature like when a site/application wants to use your microphone or web camera. Developers are on board with this feature since it can provide them with more telemetric data on how users are interacting with their website/application but there are some that are strongly voicing against this.
Good thing is that website or web application will prompt you to allow it to use this feature like when a site/application wants to use your microphone or web camera. Developers are on board with this feature since it can provide them with more telemetric data on how users are interacting with their website/application but there are some that are strongly voicing against this.
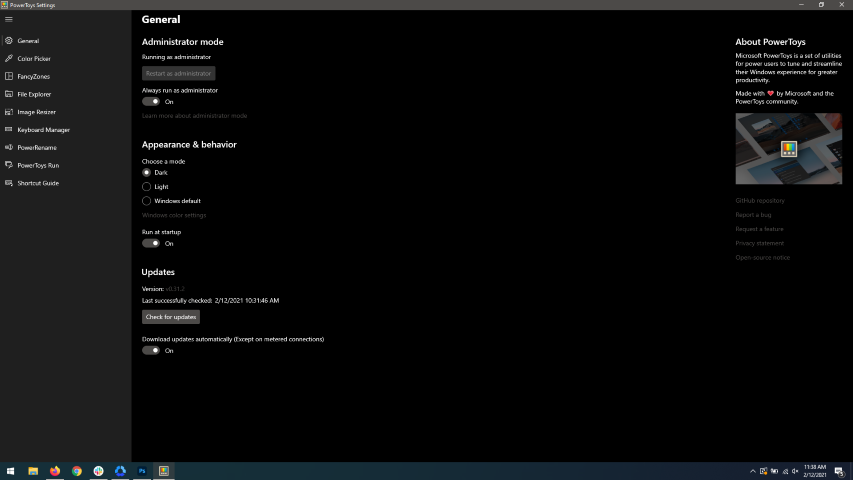 When opened you will be greeted with general settings window. These are settings for power toys themselves, Here you can check for updates, change the looks of power toys, run it on system startup and run them as administrator. Set them up so they best suit your needs.
When opened you will be greeted with general settings window. These are settings for power toys themselves, Here you can check for updates, change the looks of power toys, run it on system startup and run them as administrator. Set them up so they best suit your needs.
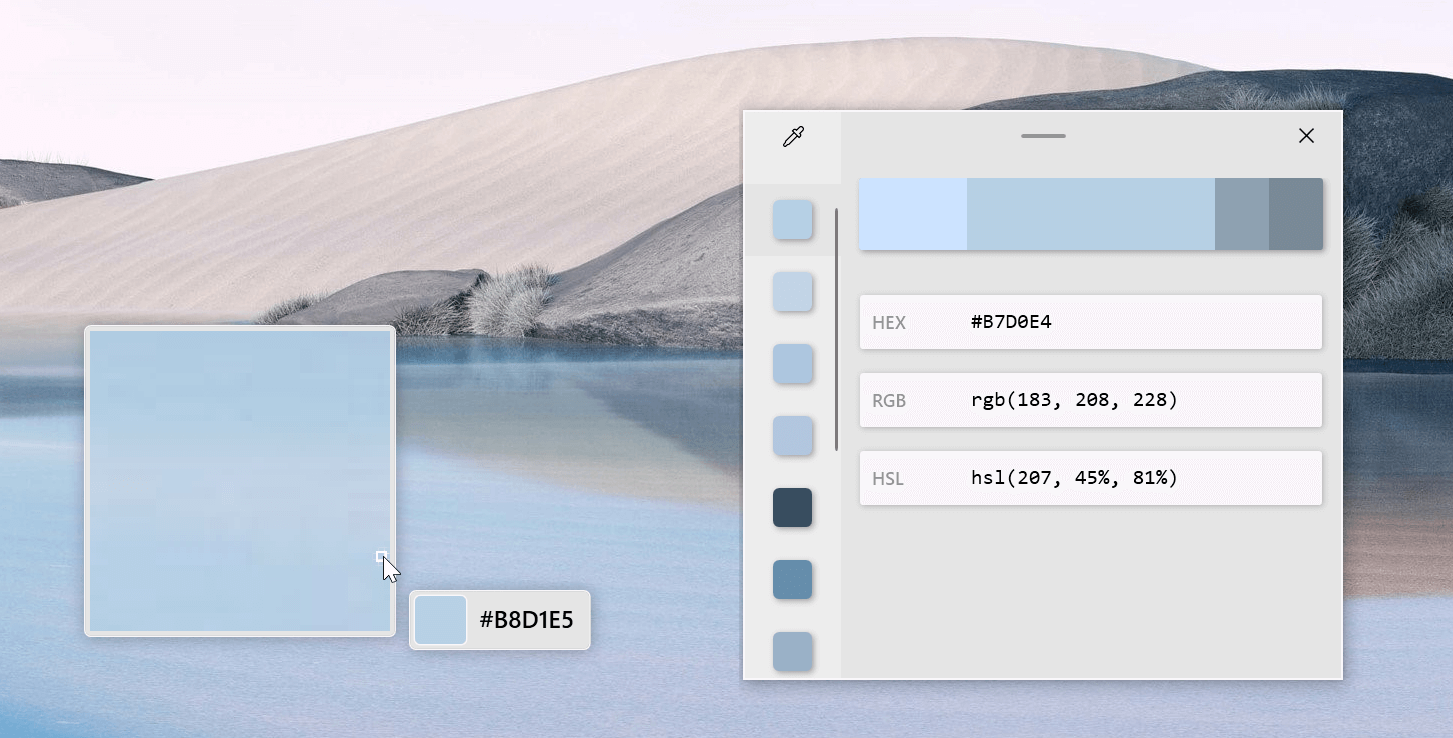 The color picker will let you as the name suggests pick colors, it will sample colors from running applications and windows, snap their values, and place them in the clipboard. A useful application if you are working as a graphic designer, want to create some cool word document, or just want to compare the difference between colors.
After the Color Picker is activated, hover your mouse cursor over the color you would like to copy and left-click the mouse button to select a color. If you want to see the area around your cursor in more detail, scroll up to zoom in. The copied color will be stored in your clipboard in the format that is configured in the settings (HEX by default). The editor lets you see the history of picked colors (up to 20) and copy their representation in any predefined string format. You can configure what color formats are visible in the editor, along with the order that they appear. This configuration can be found in PowerToys settings. The editor also allows you to fine-tune any picked color or get a new similar color. Editor previews different shades of currently selected color - 2 lighter and 2 darker ones. Clicking on any of those alternative color shades will add the selection to the history of picked colors (appears on the top of the colors history list). Color in the middle represents your currently selected color from the history of the colors. By clicking on it, the fine-tuning configuration control will appear, which will let you change the HUE or RGB values of the current color. Pressing OK will add newly configured color into the history of the colors.
The color picker will let you as the name suggests pick colors, it will sample colors from running applications and windows, snap their values, and place them in the clipboard. A useful application if you are working as a graphic designer, want to create some cool word document, or just want to compare the difference between colors.
After the Color Picker is activated, hover your mouse cursor over the color you would like to copy and left-click the mouse button to select a color. If you want to see the area around your cursor in more detail, scroll up to zoom in. The copied color will be stored in your clipboard in the format that is configured in the settings (HEX by default). The editor lets you see the history of picked colors (up to 20) and copy their representation in any predefined string format. You can configure what color formats are visible in the editor, along with the order that they appear. This configuration can be found in PowerToys settings. The editor also allows you to fine-tune any picked color or get a new similar color. Editor previews different shades of currently selected color - 2 lighter and 2 darker ones. Clicking on any of those alternative color shades will add the selection to the history of picked colors (appears on the top of the colors history list). Color in the middle represents your currently selected color from the history of the colors. By clicking on it, the fine-tuning configuration control will appear, which will let you change the HUE or RGB values of the current color. Pressing OK will add newly configured color into the history of the colors.
 FancyZones is a window manager utility for arranging and snapping windows into efficient layouts to improve the speed of your workflow and restore layouts quickly. FancyZones allows the user to define a set of window locations for a desktop that are drag targets for windows. When the user drags a window into a zone, the window is resized and repositioned to fill that zone. When first launched, the zones editor presents a list of layouts that can be adjusted by how many windows are on the monitor. Choosing a layout shows a preview of that layout on the monitor. The selected layout is applied automatically.
FancyZones is a window manager utility for arranging and snapping windows into efficient layouts to improve the speed of your workflow and restore layouts quickly. FancyZones allows the user to define a set of window locations for a desktop that are drag targets for windows. When the user drags a window into a zone, the window is resized and repositioned to fill that zone. When first launched, the zones editor presents a list of layouts that can be adjusted by how many windows are on the monitor. Choosing a layout shows a preview of that layout on the monitor. The selected layout is applied automatically.
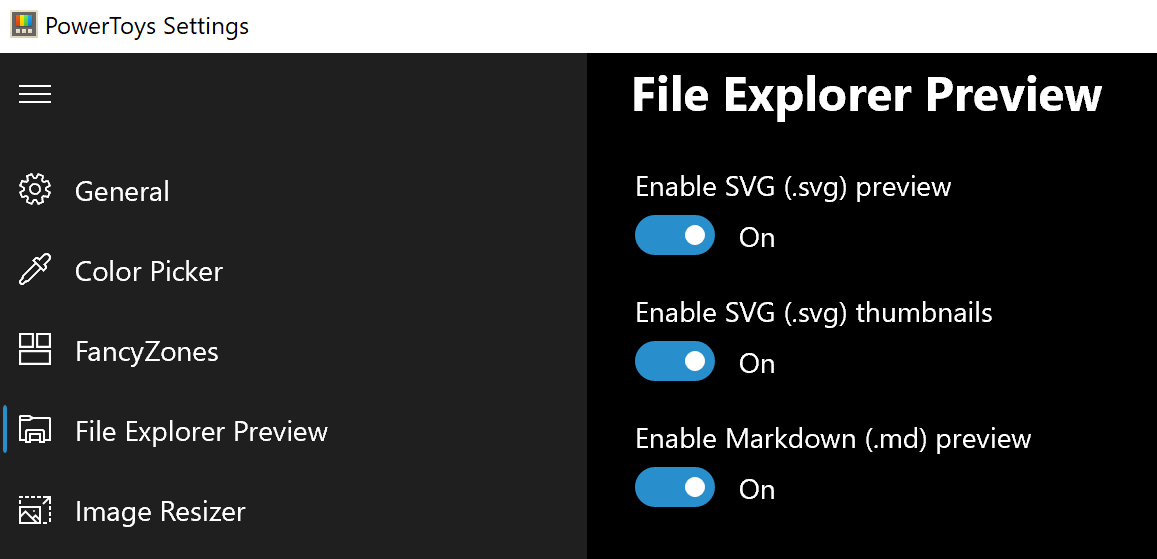 Only 3 options here but maybe some are important to you. This extension lets you enable SVG file preview in File Explorer, enable Markdown preview, and enable SVG thumbnails. Turn on each one you might need.
Only 3 options here but maybe some are important to you. This extension lets you enable SVG file preview in File Explorer, enable Markdown preview, and enable SVG thumbnails. Turn on each one you might need.
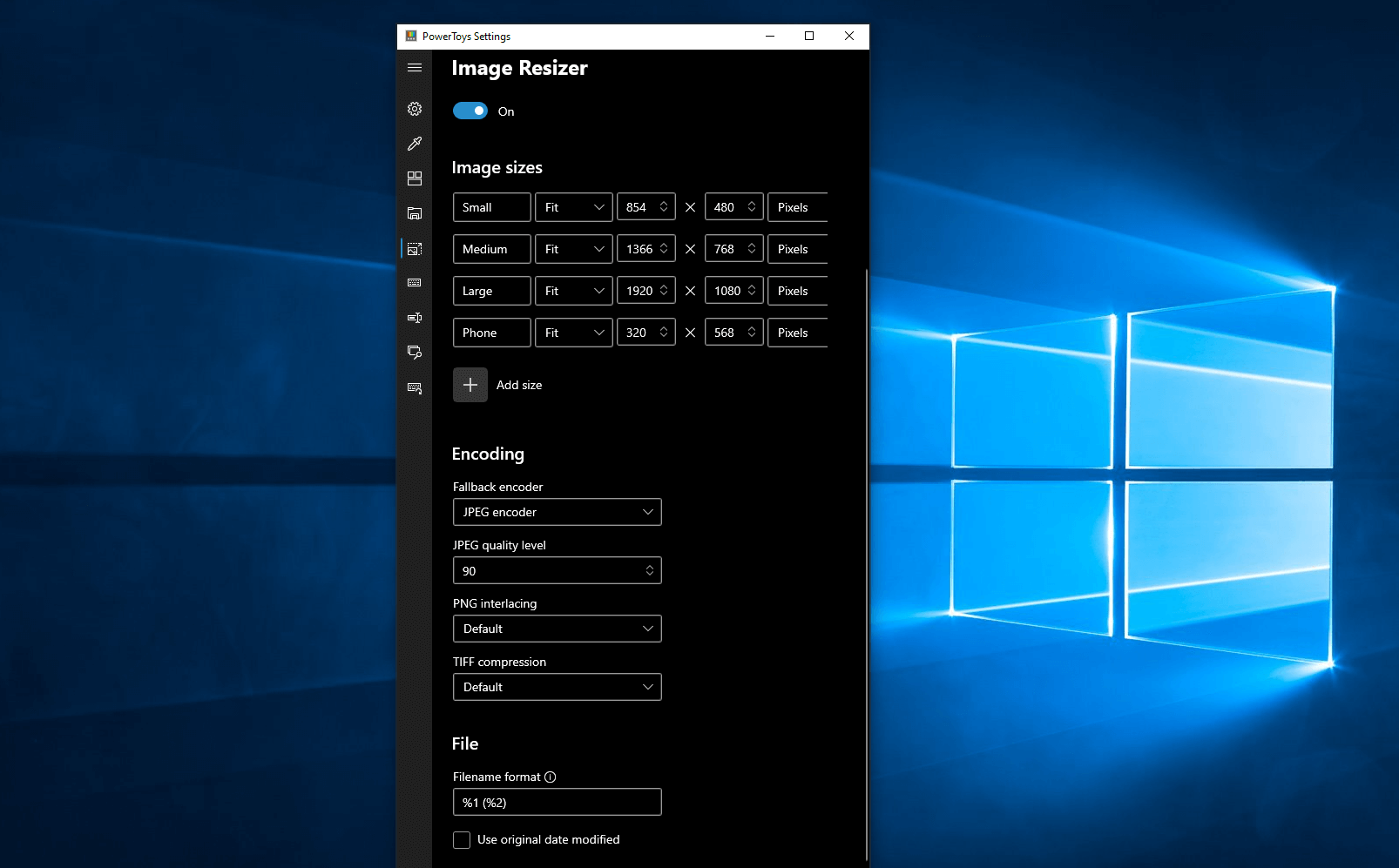 Image Resizer is a Windows shell extension for bulk image-resizing. After installing PowerToys, right-click on one or more selected image files in File Explorer, and then select Resize pictures from the menu. You can specify your own sizes if you want, you can resize when dragging files, you can overwrite files or make new copies of new sizes, and many more options. A very useful tool I am sure plenty of users can use since this eliminates the need for pictures or any other image application for common resizing tasks.
Image Resizer is a Windows shell extension for bulk image-resizing. After installing PowerToys, right-click on one or more selected image files in File Explorer, and then select Resize pictures from the menu. You can specify your own sizes if you want, you can resize when dragging files, you can overwrite files or make new copies of new sizes, and many more options. A very useful tool I am sure plenty of users can use since this eliminates the need for pictures or any other image application for common resizing tasks.
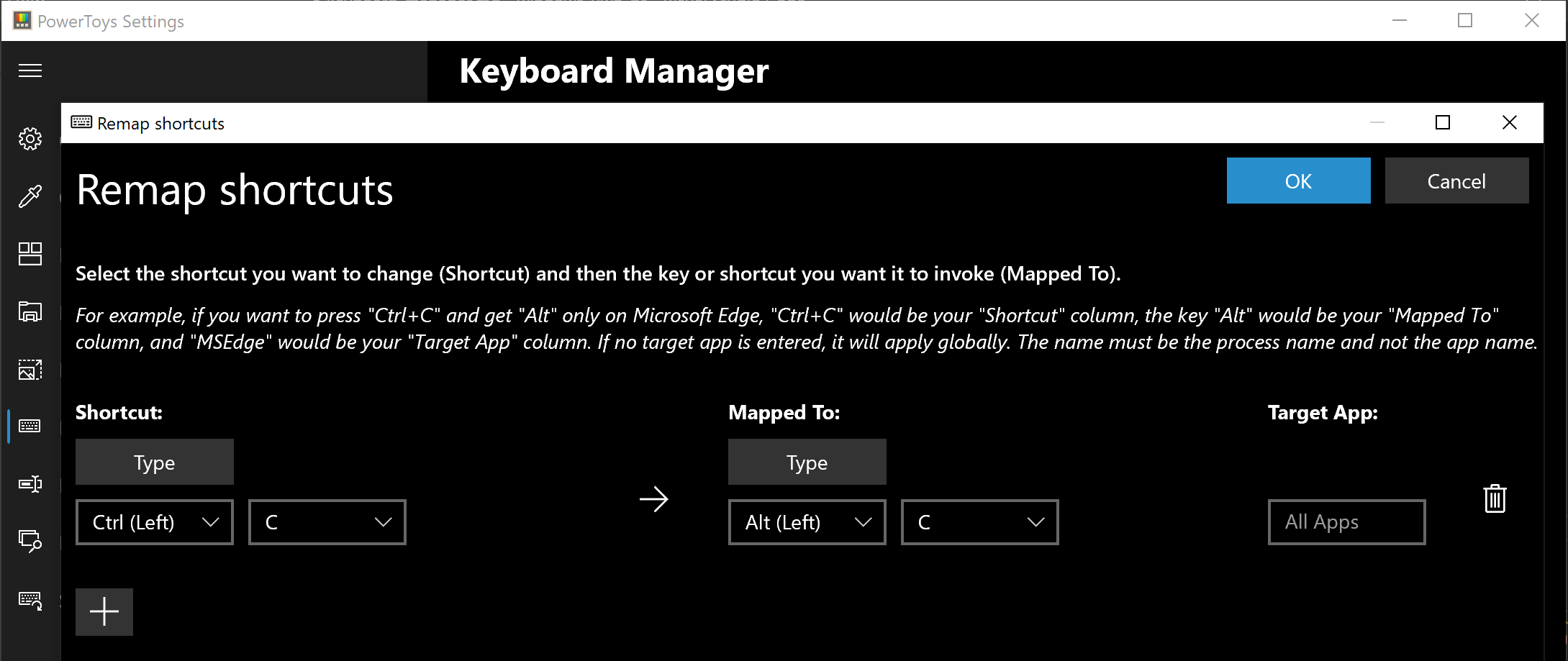 The PowerToys Keyboard Manager enables you to redefine keys on your keyboard. For example, you can exchange the letter A for the letter D on your keyboard. When you select the A key, a D will display. You can also exchange shortcut key combinations. For example, the shortcut key, Ctrl+C, will copy the text in Microsoft Word. With the PowerToys Keyboard Manager utility, you can exchange that shortcut for ⊞ Win+C). Now, ⊞ Win+C) will copy text. If you do not specify a targeted application in PowerToys Keyboard Manager, the shortcut exchange will be applied globally across Windows. PowerToys Keyboard Manager must be enabled (with PowerToys running in the background) for remapped keys and shortcuts to be applied. If PowerToys is not running, key remapping will no longer be applied.
The PowerToys Keyboard Manager enables you to redefine keys on your keyboard. For example, you can exchange the letter A for the letter D on your keyboard. When you select the A key, a D will display. You can also exchange shortcut key combinations. For example, the shortcut key, Ctrl+C, will copy the text in Microsoft Word. With the PowerToys Keyboard Manager utility, you can exchange that shortcut for ⊞ Win+C). Now, ⊞ Win+C) will copy text. If you do not specify a targeted application in PowerToys Keyboard Manager, the shortcut exchange will be applied globally across Windows. PowerToys Keyboard Manager must be enabled (with PowerToys running in the background) for remapped keys and shortcuts to be applied. If PowerToys is not running, key remapping will no longer be applied.
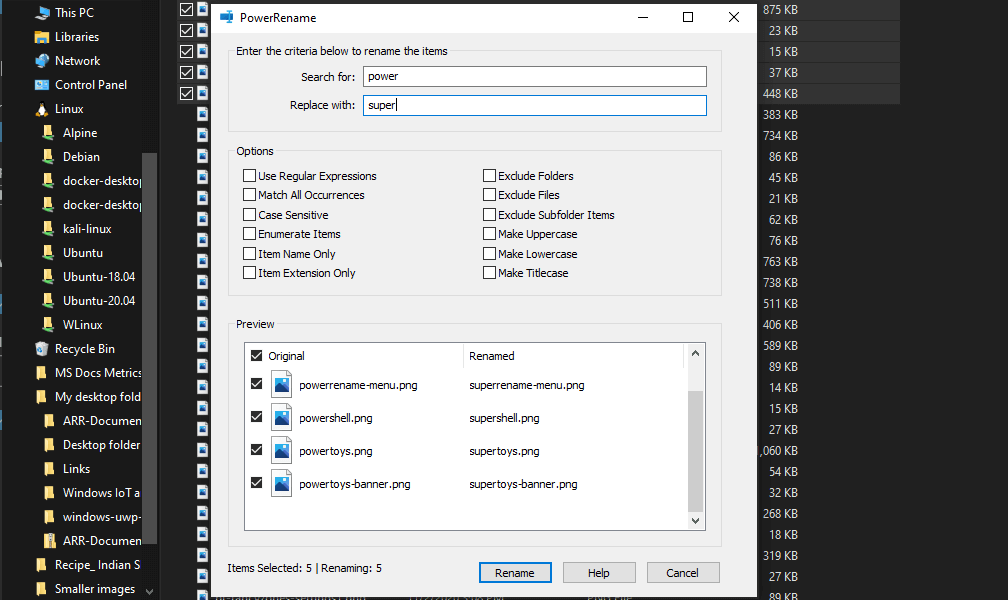 PowerRename is a bulk renaming tool that enables you to:
PowerRename is a bulk renaming tool that enables you to:
 PowerToys Run is a quick launcher for power users that contains some additional features without sacrificing performance.
PowerToys Run features include:
PowerToys Run is a quick launcher for power users that contains some additional features without sacrificing performance.
PowerToys Run features include:
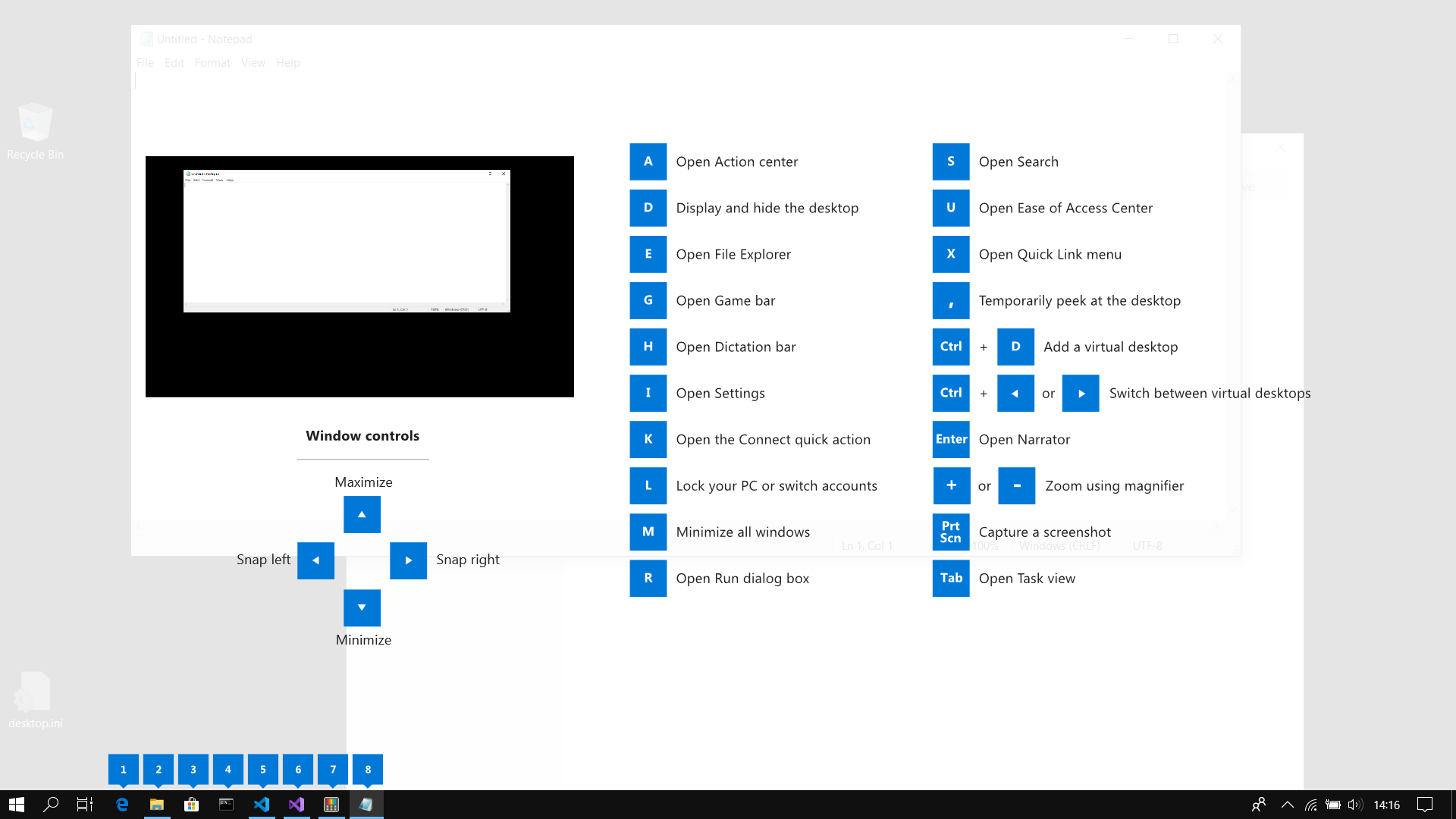 This guide uses PowerToys to display common keyboard shortcuts that use the Windows ⊞ key. Windows key keyboard shortcuts can be used while the guide is being shown and the result of those shortcuts (active window moved, arrow shortcut behavior changes, etc) will be displayed in the guide. Releasing the Windows ⊞ key will make the overlay disappear. Tapping the Windows ⊞ key will display the Windows Start menu.
Hey, you made it till the end, thank you for reading and I hope to see you soon.
This guide uses PowerToys to display common keyboard shortcuts that use the Windows ⊞ key. Windows key keyboard shortcuts can be used while the guide is being shown and the result of those shortcuts (active window moved, arrow shortcut behavior changes, etc) will be displayed in the guide. Releasing the Windows ⊞ key will make the overlay disappear. Tapping the Windows ⊞ key will display the Windows Start menu.
Hey, you made it till the end, thank you for reading and I hope to see you soon.  Antivirus software has become the kind of a must-have in every computer in this day and age. When you think about it, our systems are connected to the internet most of the time if not always, and therefore kind placed in from the line of various cyber-attacks. Here antivirus software comes into focus, especially because it has evolved long from just a simple virus removal tool to full security suites.
We will be going through the best of these applications in order to present both their good and bad sides and hope that we will help you in picking the right one for you. Remember, picking either one of the presented solutions is way better than not having one at all. The list is made from best down in our opinion so number one is highly recommended.
Antivirus software has become the kind of a must-have in every computer in this day and age. When you think about it, our systems are connected to the internet most of the time if not always, and therefore kind placed in from the line of various cyber-attacks. Here antivirus software comes into focus, especially because it has evolved long from just a simple virus removal tool to full security suites.
We will be going through the best of these applications in order to present both their good and bad sides and hope that we will help you in picking the right one for you. Remember, picking either one of the presented solutions is way better than not having one at all. The list is made from best down in our opinion so number one is highly recommended.