Many Windows 10 users use a Bluetooth headset as these kinds of Audio devices, as you know, lack wires since wires tend to get entangled and break which could get quite inconvenient. This is why using a wireless headphone is more preferable since it’s much simpler, however, using a wireless headphone also means it comes with a charging requirement and if it fails to charge, there is no music or audio or anything that you need a Bluetooth headphone for.
However, wireless headphones are also susceptible to problems as you might encounter some problems when connecting your wireless headphone to your Windows 10 computer. One of these problems include when you try to get sound from the wireless device but nothing happened. This indicates that the Bluetooth headphone is disconnected in some way for some unknown reason even if you’ve already plugged it in. Thus, if you encounter this scenario, then there are several options you need to check out to fix the problem. To start troubleshooting the problem, here are the options you need to use as a reference.
The first thing you can do to resolve the problem is to turn off your wireless audio device and wait for a couple of seconds before you turn it back on. In most cases, this should fix the problem. In fact, you can also try to unpair and pair the Bluetooth audio device and see if it fixes the problem or not.
There are times when you plug a headphone, it does not toggle the default audio device. Thus, to fix this issue, you have to set the default audio device to the headphones manually. To do that, follow these steps:
As you know, Windows 10 has various troubleshooters with user-friendly interfaces where you can utilize them to fix issues in your PC. And since you’re dealing with some Bluetooth problem, you have to run the built-in Bluetooth Troubleshooter. To do this, follow these steps:
The issue might have something to do with the Bluetooth drivers. It could be that it is outdated and needs to be updated or that you recently updated it and since then you have trouble in removing the Bluetooth devices and so to fix the issue, you can update, roll back or uninstall the Bluetooth drivers. How? Follow the steps below.
Note: Checking the update may take a few minutes so you’ll have to wait until it finishes. If it is able to find an update, you must install it. And if you want to reinstall the Bluetooth driver, just select the “Uninstall driver” option and follow the next on-screen instructions that follow.

Instaling and removing applications from your Windows can sometimes leave some traces that are unpleasant and can cause annoyances. One of these annoyances is the program in the startup section of the task manager.
If you ever opened task manager and went into the startup section trying to disable some of the startup items on your Windows boot there might be a chance that you have experienced and seen a program without any icon or information about it just sitting there.
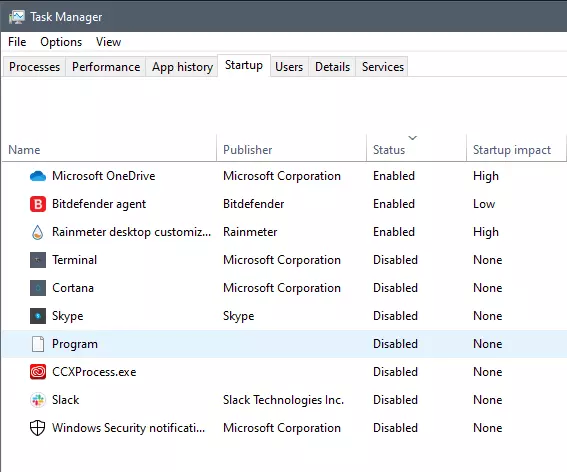
This is due to some applications being removed from the system but for some reason, it still shows itself in startup and it is quite annoying. So here we will show you how to get rid of this annoyance so your startup is clean again without junk in it.
The first thing of course is to open the task manager itself and navigate to the startup tab. Inside the startup tab right-click on the column header and tick or enable Startup type and command line. Now you will see the location of the supposed file (that is missing or you could just go there by right-clicking on the item, but here it is greyed).
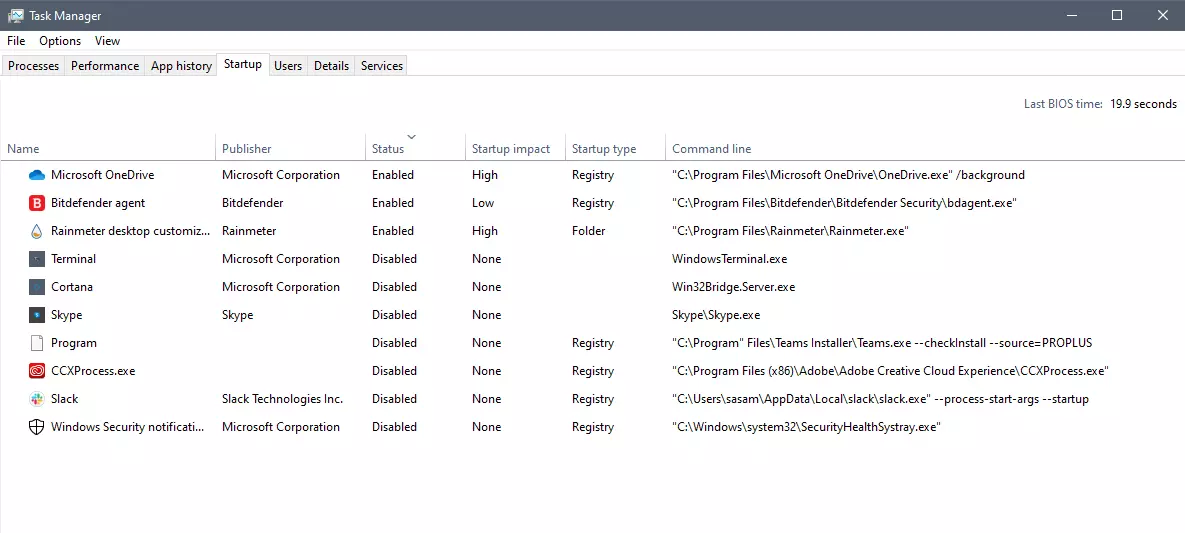
99% of the time startup type will be registry since the file is missing, if it was a file fix would be just to simply delete the file in the folder but since it was installed and not properly removed registry key is still present but the file cannot be found. After confirmation that the file is indeed missing and that the startup type is registry open the registry editor by typing Regedit in search and pressing enter.
Inside Registry editor navigate to: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. Inside on right part, you will see all auto-start entries added by installed applications.
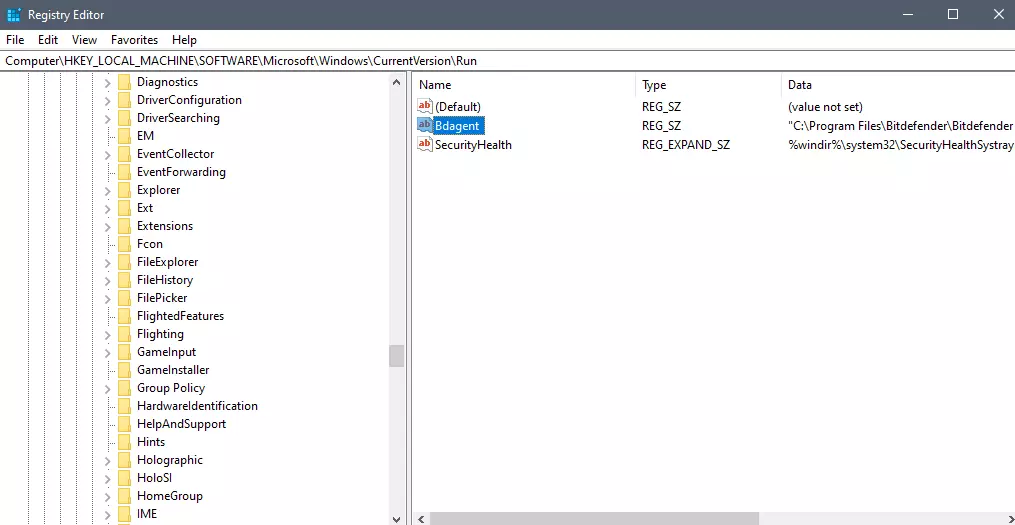
Locate one that is causing issues by comparing its path with the path inside the task manager command line and delete the key. Once the key is deleted right-click on RUN on the left part and choose HKEY_LOCAL_MACHINE to quickly jump on that key location and repeat the process of key deletion if needed. HKEY_LOCAL_MACHINE will delete startup entry for all users and sometimes entry will not be present here since the application is not installed for all users or there are no other users on the machine.
After the procedure is finished, reboot your systems in order to apply changes.
“Windows is unable to reach your company’s activation service. Please connect to your corporate network. If you are connected and continue to see the error, contact your system administrator. You can also click on the error detail to find the exact error. Error code: 0xC004F074.” “Activating Windows(R), (Key hash)… Error: 0xC004F074 The Software Licensing Service reported that the computer could not be activated. No Key Management Service (KMS) could be contacted. Please see the Application Event Log for additional information.” “Error 0xC004F074, SL_E_AUTHN_MISMATCHED_KEY, The Software Licensing Service reported that the key is mismatched.”To fix the Windows 10 Activation error 0xC004F078, you have to use the correct key for your type of Windows copy or use Command Prompt to reinstall the key or you could also try running the Activation troubleshooter.
 Error Causes
Error Causes