Error Code 0xc1900106 – What is it?
One of the most common errors encountered by Microsoft users upgrading from Windows 7 or Windows 8/8.1 to Windows 10 is the Error Code 0xc1900106. Microsoft users experience a failure in the installation process. Either they will be notified that the installation process was ended but failed or that Windows is not able to install the update.
Solution
 Error Causes
Error Causes
More and more Windows users are having trouble upgrading their operating system to Windows 10. There are a lot of errors being encountered by users and one of them is the Error Code 0xc1900106. This error is normally due to the misconfigured system files. If a Windows user encounters this error, most likely their device has some registry problems.
Further Information and Manual Repair
Fixing error code-related issues could be best resolved to do manual repair methods. Applying repair methods manually can help Windows users address the root causes of the errors they encounter, as well as apply definite solutions to rectify the issue.
Most Windows users can be able to implement manual repair methods themselves but there are some cases where help from a Windows professional is needed. If you’re not a very tech-savvy person and not confident performing the manual repair methods yourself, it would be advisable to seek help from a professional Windows technician who is knowledgeable enough to address the errors or problems you are encountering. However, if you don’t want to resort to seeking help from a professional, you can also consider using a powerful automated tool.
In trying to fix Error Code 0xc1900106, here are the following manual repair methods you can take:
Method One: Custom Installation
- Make a backup of your personal files
- Users of Windows 8/8.1 should Refresh first then proceed to upgrade.
- If the Refresh process does not work, reset your device then try again.
- If resetting your device still does not work, you can proceed with a custom installation.
- When your Windows installation media is ready, you need to choose to boot from CD, DVD, or USB drive to begin setup. (For example purposes, this article will discuss booting from DVD).
- When your device is all set to boot from DVD, you will be prompted to Press any key to boot from CD or DVD…
- Once you’ve pressed any key, the screen will show the Windows logo which might take a while. No need to worry though, as long as you can see the indicator, you’re good.
- Choose your Language, Time, and Keyboard method from the drop-down menu then hit Next.
- Click on the Install Now button then wait until Setup begins.
- Tick on the I accept the license terms check box then select Next.
- Choose Custom: Install Windows only (advanced)
- Choose the Primary partition then select Next. You will be prompted by the following warning: The partition you selected might contain files from a previous Windows Installation. If it does, these files and folders will be moved to a folder named Windows.old. You will be able to access the information in Windows.old, but you will be able to use your previous version of Windows. Just click the OK button then wait as the Windows continue to install. Windows will restart once this phase of the setup completes and will reboot into setup once again.
- At this point, Windows will detect and install your hardware. Once this finishes, Windows will restart again.
Method Two: Reset Windows Update Components
- From your device’s desktop, hit Windows key + X to open the command prompt as admin.
- Once the command prompt window appears, you can type or copy and paste the following commands (all at once):
net stop wuauserv net stop cryptSvc net stop bits net stop msiserver ren C:WindowsSoftwareDistribution SoftwareDistribution.old ren C:WindowsSystem32catroot2 catroot2.old net start wuauserv net start cryptSvc net start bits net start msiserver pause
- Exit the command prompt.
- After you reset the Windows Update components, see if you receive Windows Updates which includes the firmware updates for your computer.
Method Three: Ensure Windows is Updated
- If you have an antivirus, make sure to disable it during the upgrade process.
- Run Windows Update to check if the system is updated.
- Ensure that the latest firmware and drivers are installed. To be able to do this, go to the computer manufacturer’s website or you can also try contacting company support.

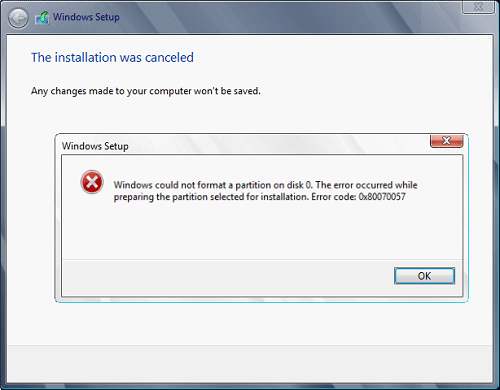 This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.
This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors. 