Error Code 0xd0000272 – What is it?
Error code 0xd0000272 occurs when Windows users are unable to activate their operating system. This usually occurs due to activation servers being busy or unavailable and affects Windows 8, Windows 8.1, and Windows 10 users.
Common symptoms of the error code include the following:
- Inability to activate Windows operating system
- Message box with error code 0xd0000272
Solution
 Error Causes
Error Causes
Windows users affected by error code 0xd0000272 usually receive a message stating that the “activation server is busy or unavailable”. Some users report the error is resolved on its own after a few hours, while others experience activation issues that resolve only after manual repair methods are implemented.
Further Information and Manual Repair
To improve your chances of resolving issues related to Windows activation error codes, use manual repair methods and procedures. These are often successful as they address the issues causing the error codes to occur, whether there be missing or corrupted system files, network connectivity issues, or invalid product keys.
Error code 0xd0000272 may be resolved by simply waiting until later – a few hours at most – to reattempt activation. If, however, the activation process fails, proceed with the methods suggested below or contact a Windows repair technician.
-
Method One: Verify Internet Connection to Activate Windows
Are network connectivity issues preventing your machine from activating Windows? Check for this issue by verifying whether or not you are connected. Once you’ve been able to check your connection via your Internet settings and troubleshoot your network where necessary, proceed to the Product Activation Wizard.
The Product Activation Wizard will check if you have permission or authorized access to the version of Windows you are attempting to activate. This process usually involves the use of a product key. Once you enter the 25-character code – in the correct order, of course – proceed by selecting the activation option.
If the process is successful, you will be able to complete the activation and access all the features of the Windows edition you have activated. You will also notice the absence of the error code 0xd0000272 message. In cases where this manual repair method is unable to successfully resolve the issue, however, move to the next manual repair procedure on this list.
-
Method Two: Run Windows Update Troubleshooter
Another tool available to Windows users is the Windows Update Troubleshooter. You may access the Windows Update Troubleshooter offered on Windows 8 since it does not require an internet connection and runs most of the functions required. To do so, follow the steps below.
- Step one: Swipe to the right of the screen and click Search
- Step two: Type Troubleshooting
- Step three: Click Settings then select Troubleshooting
- Step four: Under System & Security, click Fix Problems with Windows Update
- Step five: Select Next
You can also visit Microsoft’s website to access a more comprehensive Windows Update Troubleshoot tool. Download the troubleshooter and run it to fix problems related to Windows Update. Afterward, restart your computer then check the Product Activation Wizard to verify whether or not you can activate Windows 8 or 8.1. If the problem persists, however, and error code 0xd0000272 reoccurs, proceed to the third manual repair method.
-
Method Three: Disable Proxy Settings
Your computer’s proxy settings may in some cases interfere with the activation process, resulting in issues like error code 0xd0000272. To fix this problem, first, disable your proxy setting then reattempt the activation process using the Product Activation Wizard.
- Step one: Press Win + C keyboard combination
- Step two: Select Settings
- Step three: Click Change PC Settings
- Step four: Select Network, then Proxy
- Step six: Switch proxy server settings to Off
Open the Product Activation Wizard once you’ve disabled the proxy settings. Complete the activation process based on the instructions provided. If you are successful, you will no longer be bothered by error code 0xd0000272 as the symptoms of the error code will not occur.
If, however, this manual repair method fails to resolve the error code, you may need to consider other alternatives. These may include the use of a powerful automated tool. You can also consider getting help from a Windows repair technician as such professionals are able to assess your computer and provide solutions as needed.
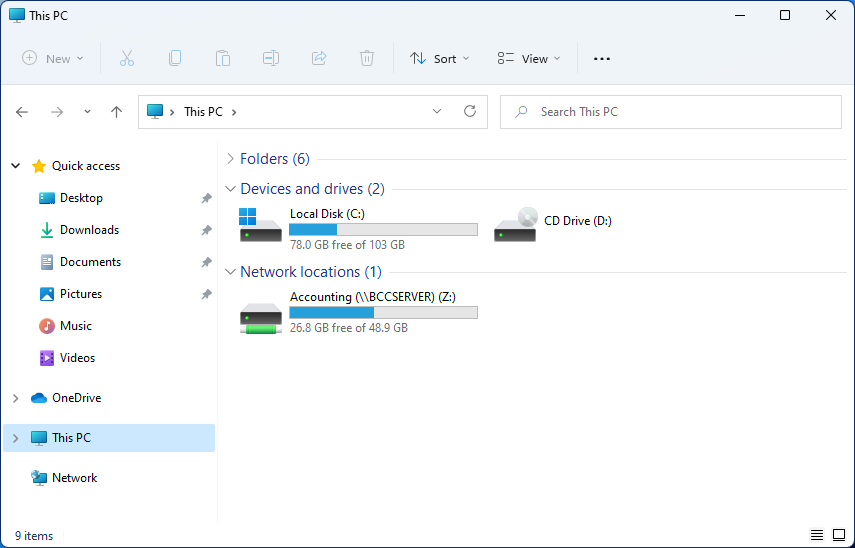 Mapping network drive has many benefits in terms of speed and ease of access of files via network. It lets you access the hard drive over the whole network like it was the hard drive inside your PC case. In order to easily and quickly map a folder as a network drive follow the guide below.
Mapping network drive has many benefits in terms of speed and ease of access of files via network. It lets you access the hard drive over the whole network like it was the hard drive inside your PC case. In order to easily and quickly map a folder as a network drive follow the guide below.
 However, if you are working on a computer with a keyboard and mouse this feature might annoy you and seem like something that is not needed. Like many things inside Windows 11 this feature also can be customized and turned OFF if you do not want it.
In this guide, we will see how to turn these boxes off. Microsoft has somewhat hidden this feature but luckily it is not difficult to find it if you know where to look.
However, if you are working on a computer with a keyboard and mouse this feature might annoy you and seem like something that is not needed. Like many things inside Windows 11 this feature also can be customized and turned OFF if you do not want it.
In this guide, we will see how to turn these boxes off. Microsoft has somewhat hidden this feature but luckily it is not difficult to find it if you know where to look.

 This is not the first time that Intel is trying to enter the GPU field but its adventures so far were, well let us agree not so good. All of that is hoping to be changed with the upcoming ARC GPU. The first generation of Arc graphics, code-named Alchemist and previously known as DG2, will support desktop PCs and laptops and is set to arrive in the first quarter of 2022.
Alchemist will have hardware-based Ray tracing and AI-driven supersampling. This indicates that GPU is aimed to compete in the Hi-end spectrum and battle side by side with Nvidia and AMD on the market. Alchemist will also pack full DirectX 12 Ultimate support.
Intel also released names for the next upcoming future generations of ARC GPUs: Battlemage, Celestial & Druid. More information about ARC products will be released later this year.
“Today marks a key moment in the graphics journey we started just a few years ago. The launch of the Intel Arc brand and the reveal of future hardware generations signifies Intel’s deep and continued commitment to gamers and creators everywhere,” Roger Chandler, Intel vice president, and general manager of client graphics products and solutions.
This is not the first time that Intel is trying to enter the GPU field but its adventures so far were, well let us agree not so good. All of that is hoping to be changed with the upcoming ARC GPU. The first generation of Arc graphics, code-named Alchemist and previously known as DG2, will support desktop PCs and laptops and is set to arrive in the first quarter of 2022.
Alchemist will have hardware-based Ray tracing and AI-driven supersampling. This indicates that GPU is aimed to compete in the Hi-end spectrum and battle side by side with Nvidia and AMD on the market. Alchemist will also pack full DirectX 12 Ultimate support.
Intel also released names for the next upcoming future generations of ARC GPUs: Battlemage, Celestial & Druid. More information about ARC products will be released later this year.
“Today marks a key moment in the graphics journey we started just a few years ago. The launch of the Intel Arc brand and the reveal of future hardware generations signifies Intel’s deep and continued commitment to gamers and creators everywhere,” Roger Chandler, Intel vice president, and general manager of client graphics products and solutions.  When Task Manager opens, click on the startup tab on top.
When Task Manager opens, click on the startup tab on top.
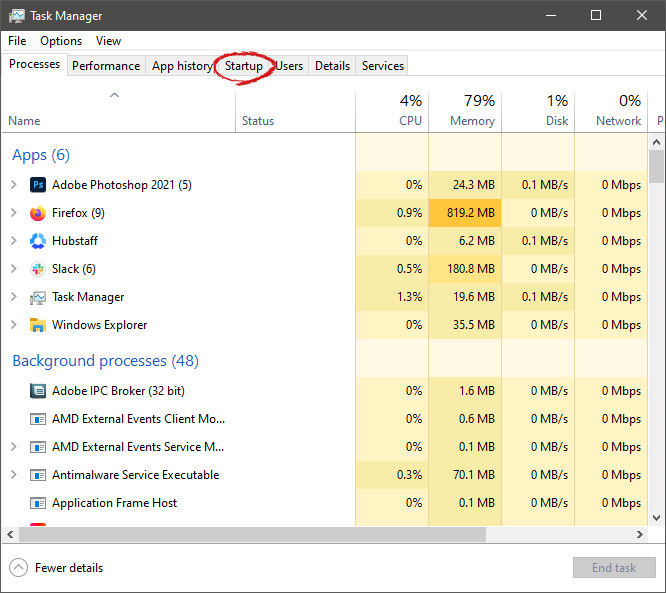 Once you click on startup you will get a list of applications that are set to be started when Windows is booted.
Once you click on startup you will get a list of applications that are set to be started when Windows is booted.
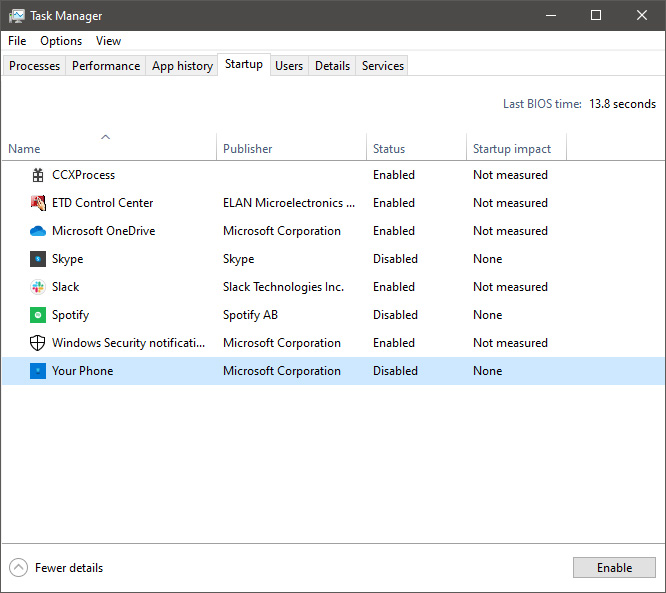 You can now click on the application and then click on disable on the bottom button, the application status will update in task manager to disabled and it will not be booted anymore when Windows starts. In this same manner, you can enable back some applications if you changed your mind about them.
Please note that some applications are using some services and must have them running or they will not work properly. The best practice is to disable applications you are positive you will not use or use rarely so you do not want them to slow down Windows.
You can now click on the application and then click on disable on the bottom button, the application status will update in task manager to disabled and it will not be booted anymore when Windows starts. In this same manner, you can enable back some applications if you changed your mind about them.
Please note that some applications are using some services and must have them running or they will not work properly. The best practice is to disable applications you are positive you will not use or use rarely so you do not want them to slow down Windows. 