RebateInformer is a browser extension for Google Chrome. This extension monitors the web pages the user is visiting and checks against an affiliate database for various rebates and coupons related to the context of the products being shown in the browser.
This extension analyzes websites your browser visits and attempts to find deals associated with the merchant’s product offerings. If an offer is found, it is injected into the deals page even if it's sold by a different merchant at a higher price.
Several anti-virus scanners have marked this extension as Potentially Unwanted, and due to its data mining behavior, it is not recommended to keep it on your computer.
About Browser Hijackers
Browser hijacking is regarded as the web’s constant problem that targets web browsers. It is a type of malicious software that alters your web browser’s settings and redirects you to sites or webpages that you had no intention of visiting. Browser hijacker malware is created for numerous reasons. It redirects you to the sponsored sites and injects adverts on your internet browser that helps its creator generate ad revenue. It could seem naive, but the majority of these websites are not legitimate and may pose a serious threat to your online safety. Additionally, hijackers can make the whole infected system fragile – other dangerous malware and viruses will use these opportunities to intrude into your computer system effortlessly.
Browser hijacking symptoms
There are many different symptoms that indicate the web browser has been highjacked: your browser’s home page is suddenly different; new bookmarks pointing to porn websites are added to your bookmarks; the default internet search engine and the default browser settings are modified; unsolicited new toolbars are added to your browser; numerous pop-up adverts show up and/or your browser pop-up blocker is disabled; your web browser starts running slowly or displays frequent errors; you’re blocked to access the websites of computer security solution providers.
How browser hijacker infects computers
There are several ways your PC could become infected with a browser hijacker. They usually arrive through spam e-mail, via file-sharing networks, or by a drive-by-download. They also come from add-on applications, also called browser helper objects (BHO), browser extensions or toolbars. Sometimes you may have inadvertently accepted a browser hijacker as part of an application package (generally freeware or shareware). An example of some notorious browser hijacker includes Conduit, Anyprotect, Babylon, DefaultTab, SweetPage, Delta Search, and RocketTab, however, the names are continually changing.
Browser hijackers could record user keystrokes to collect potentially valuable information that leads to privacy concerns, cause instability on systems, drastically disrupt the user experience, and eventually slow down the computer to a point where it becomes unusable.
Browser hijacker removal
Some browser hijacking can be simply stopped by finding and removing the corresponding malware software through your control panel. Unfortunately, many of the software packages utilized to hijack a web browser are deliberately built to be hard to detect or remove. Furthermore, manual removals require in-depth system knowledge and thus could be a very difficult job for novice computer users.
Professionals always suggest users remove any malicious software including browser hijacker by using an automatic malware removal tool, which is better, safer, and quicker than the manual removal technique. Safebytes Anti-Malware features a state-of-the-art anti-malware engine to help you prevent browser hijacker infection in the first place, and mop up any existing problems. And employ a PC optimizer to erase all associated files in the registry and fix browser problems.
Can’t Install Safebytes Anti-malware due to the presence of a Virus? Try This!
Malware can cause all sorts of damage once they invade your system, from stealing your personal information to deleting data files on your computer. Some malware sits in between the computer and the net connection and blocks a few or all internet sites that you would like to visit. It could also block you from the installation of anything on your system, especially the anti-malware program. If you’re reading this right now, you’ve perhaps recognized that a malware infection is the real cause of your blocked web traffic. So how to proceed when you want to install an anti-virus application such as Safebytes? Refer to the instructions below to eliminate malware by alternate methods.
Download the software in Safe Mode with Networking
In Safe Mode, you can actually modify Windows settings, uninstall or install some applications, and get rid of hard-to-delete viruses. If the malware is set to load automatically when the computer boots, shifting into this mode may prevent it from doing so. In order to enter into Safe Mode or Safe Mode with Networking, press F8 while the computer is booting up or run MSConfig and find the “Safe Boot” options under the “Boot” tab. As soon as you reboot into Safe Mode with Networking, you could download, install, and update the anti-malware program from there. After installation, run the malware scanner to remove standard infections.
Obtain the anti-malware software using an alternate web browser
Web-based malware can be environment-specific, targeting a particular web browser or attacking specific versions of the web browser. The ideal solution to avoid this issue is to choose a browser that is renowned for its security measures. Firefox contains built-in Malware and Phishing Protection to keep you secure online.
Install anti-malware on a thumb drive
Here’s another solution which is using a portable USB antivirus software that can check your system for malicious software without needing installation. Do these simple steps to clean up your infected PC by using a portable antivirus.
1) Download Safebytes Anti-Malware or MS Windows Defender Offline onto a virus-free computer.
2) Connect the USB flash drive to a USB port on the clean computer.
3) Double-click the Setup icon of the anti-malware program to run the Installation Wizard.
4) Choose the drive letter of the flash drive as the place when the wizard asks you where you want to install the antivirus. Follow activation instructions.
5) Transfer the USB drive from the uninfected computer to the infected PC.
6) Double-click the anti-malware program EXE file on the USB flash drive.
7) Hit the “Scan Now” button to begin the virus scan.
Review of SafeBytes Anti-Malware
These days, an anti-malware program can protect your computer or laptop from different types of internet threats. But how to select the right one amongst various malware protection application that’s available in the market? You may be aware, there are numerous anti-malware companies and tools for you to consider. A few are very good ones, some are ok types, and some are simply just bogus anti-malware programs that can damage your PC themselves! You need to be very careful not to pick the wrong application, particularly if you purchase a premium application. With regards to commercial antimalware tool options, many people go with popular brands, such as SafeBytes, and are quite happy with it.
SafeBytes anti-malware is a reliable tool that not only protects your PC permanently but is also quite user-friendly for people of all skill levels. With its most advanced virus detection and repair technology, this software will help you protect your personal computer against infections brought on by different types of malware and other internet threats, including spyware, adware, trojans, worms, computer viruses, keyloggers, potentially unwanted program (PUPs), and ransomware.
SafeBytes has got a plethora of features that can help you protect your computer from malware attacks and damage. Here are some typical features found in this application:
Real-time Protection: SafeBytes provides round-the-clock protection for your computer restricting malware intrusions instantly. It will check your PC for suspicious activity regularly and its unparalleled firewall guards your PC against illegal entry by the outside world.
Robust, Anti-malware Protection: This deep-cleaning anti-malware software goes much deeper than most antivirus tools to clean your personal computer. Its critically acclaimed virus engine detects and disables hard-to-remove malware that conceals deep inside your PC.
Safe Web Browsing: Safebytes assigns all sites a unique safety rating that helps you to get an idea of whether the webpage you’re just about to visit is safe to view or known to be a phishing site.
Low CPU Usage: SafeBytes is really a lightweight tool. It consumes a very small amount of processing power as it runs in the background so you won’t notice any system performance issues.
24/7 Online Support: Expert technicians are at your disposal 24/7! They will quickly fix any technical issues you may be experiencing with your security software.
To sum it up, SafeBytes Anti-Malware offers superb protection combined with an acceptable low system resources usage with great malware detection and prevention. You now may know that this particular tool does more than just scan and delete threats on your computer. So if you are looking for the best anti-malware subscription for your Windows-based PC, we strongly recommend the SafeBytes Anti-Malware tool.
Technical Details and Manual Removal (Advanced Users)
If you do not wish to use malware removal software and prefer to get rid of RebateInformer manually, you may do so by going to the Add/Remove Programs menu in the Control Panel and removing the offending software; in cases of browser plug-ins, you can uninstall it by visiting the browsers Add-on/Extension manager. You will definitely also want to reset your browser.
Lastly, check your hard drive for all of the following and clean your registry manually to get rid of leftover application entries following an uninstallation. However, this can be a difficult task and only computer professionals could perform it safely. Also, some malware is capable of replicating itself or preventing deletion. It is highly recommended that you carry out the removal process in Windows Safe Mode.

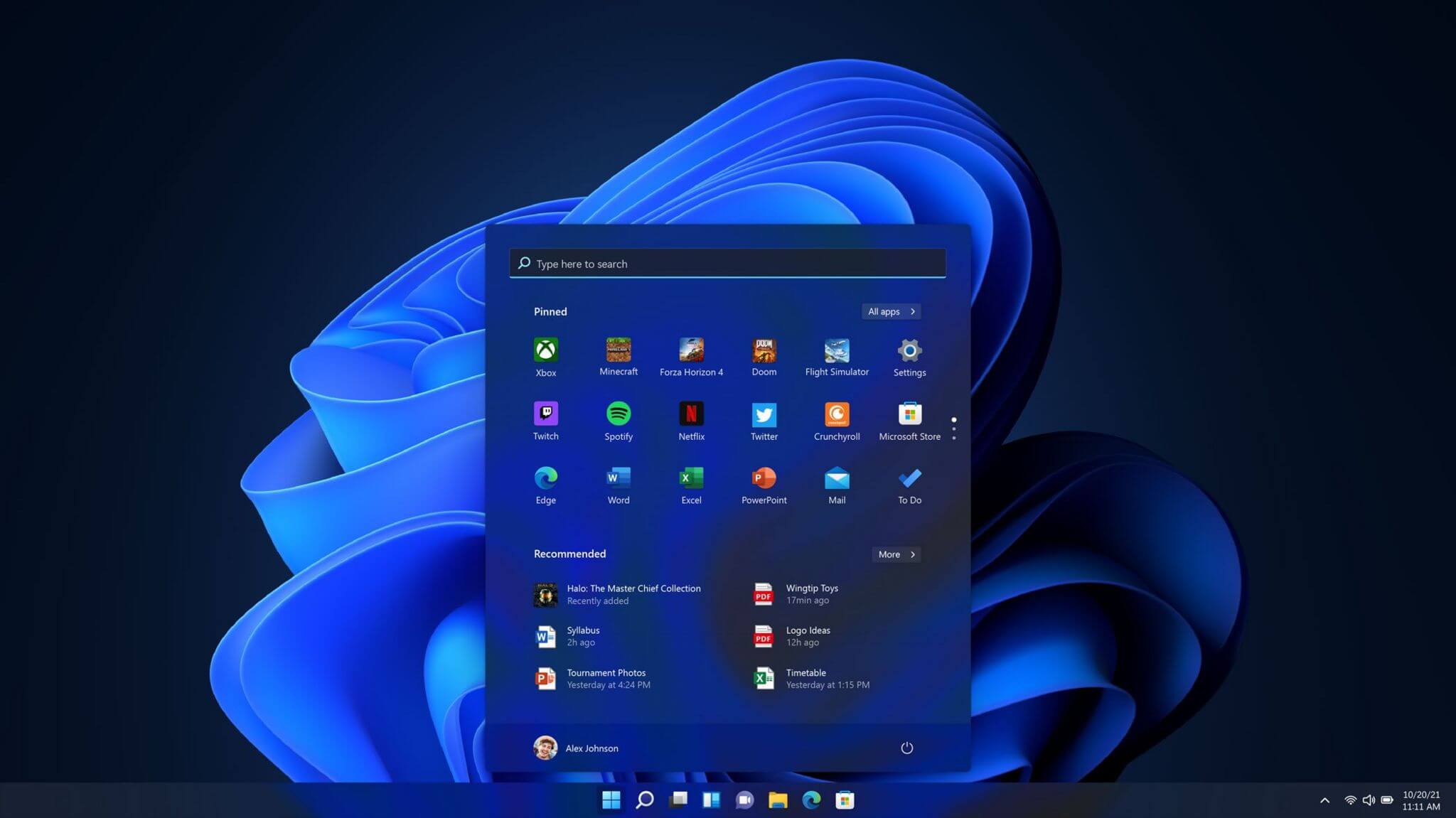 One of the first things that everyone saw when Microsoft has unveiled Windows 11 is its Start menu. Funny enough this is what has caused most of the divide among users, some find it interesting, and some do not like it. Truth is, it is different, and it is centered in the middle instead of the lower left part of the screen.
It has been confirmed however that the Start menu can be moved to any part of the screen so if you want, you could place it on the lower left as it has always been.
Live tiles do not longer exist in the Start menu, instead, we have styled simple icons.
One of the first things that everyone saw when Microsoft has unveiled Windows 11 is its Start menu. Funny enough this is what has caused most of the divide among users, some find it interesting, and some do not like it. Truth is, it is different, and it is centered in the middle instead of the lower left part of the screen.
It has been confirmed however that the Start menu can be moved to any part of the screen so if you want, you could place it on the lower left as it has always been.
Live tiles do not longer exist in the Start menu, instead, we have styled simple icons.
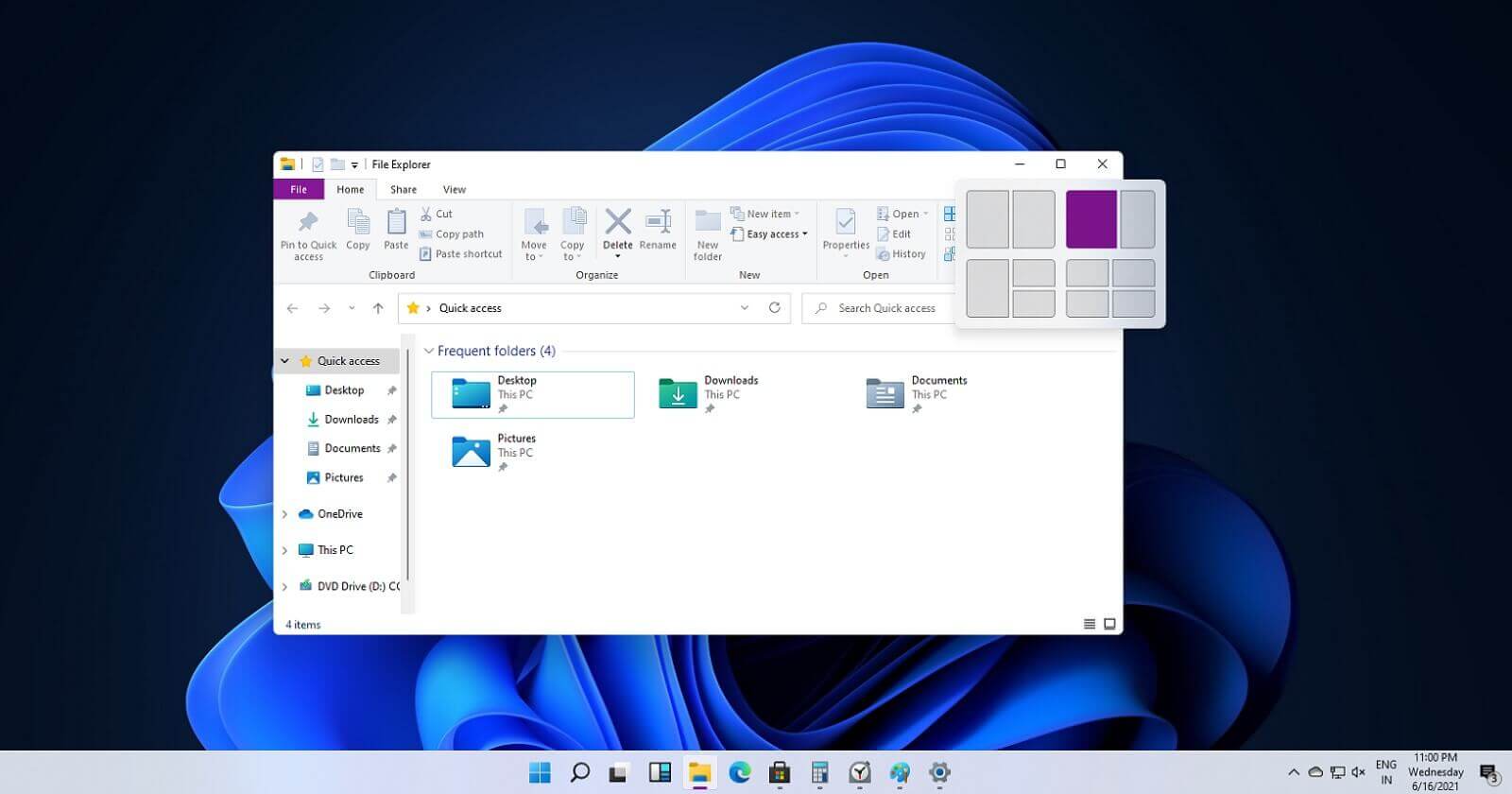 If you have used the cascade option in previous Windows versions then it is most likely that you will like the new Snap controls.
You can quickly snap windows side by side, or arrange them in sections on your desktop just by hovering over maximize button on the title bar.
If you have used the cascade option in previous Windows versions then it is most likely that you will like the new Snap controls.
You can quickly snap windows side by side, or arrange them in sections on your desktop just by hovering over maximize button on the title bar.
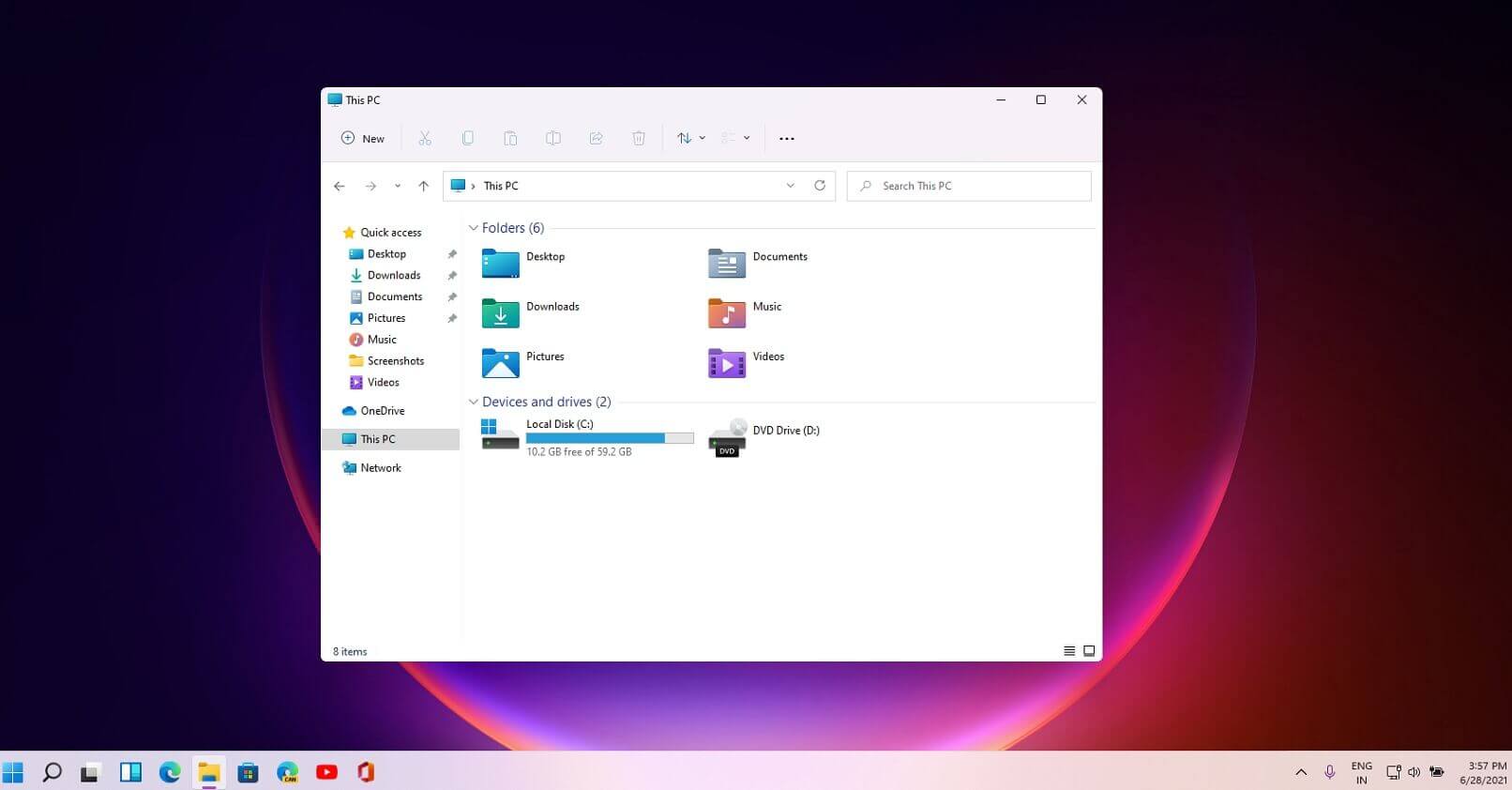 File explorer has gone through some visual and design changes, the ribbon on top has been completely removed and replaced with a header-like feature with a slick and clean design.
The header contains a nice organized and designed single row of icons like cut, paste, copy, rename, delete, and new folder icons.
File explorer has gone through some visual and design changes, the ribbon on top has been completely removed and replaced with a header-like feature with a slick and clean design.
The header contains a nice organized and designed single row of icons like cut, paste, copy, rename, delete, and new folder icons.
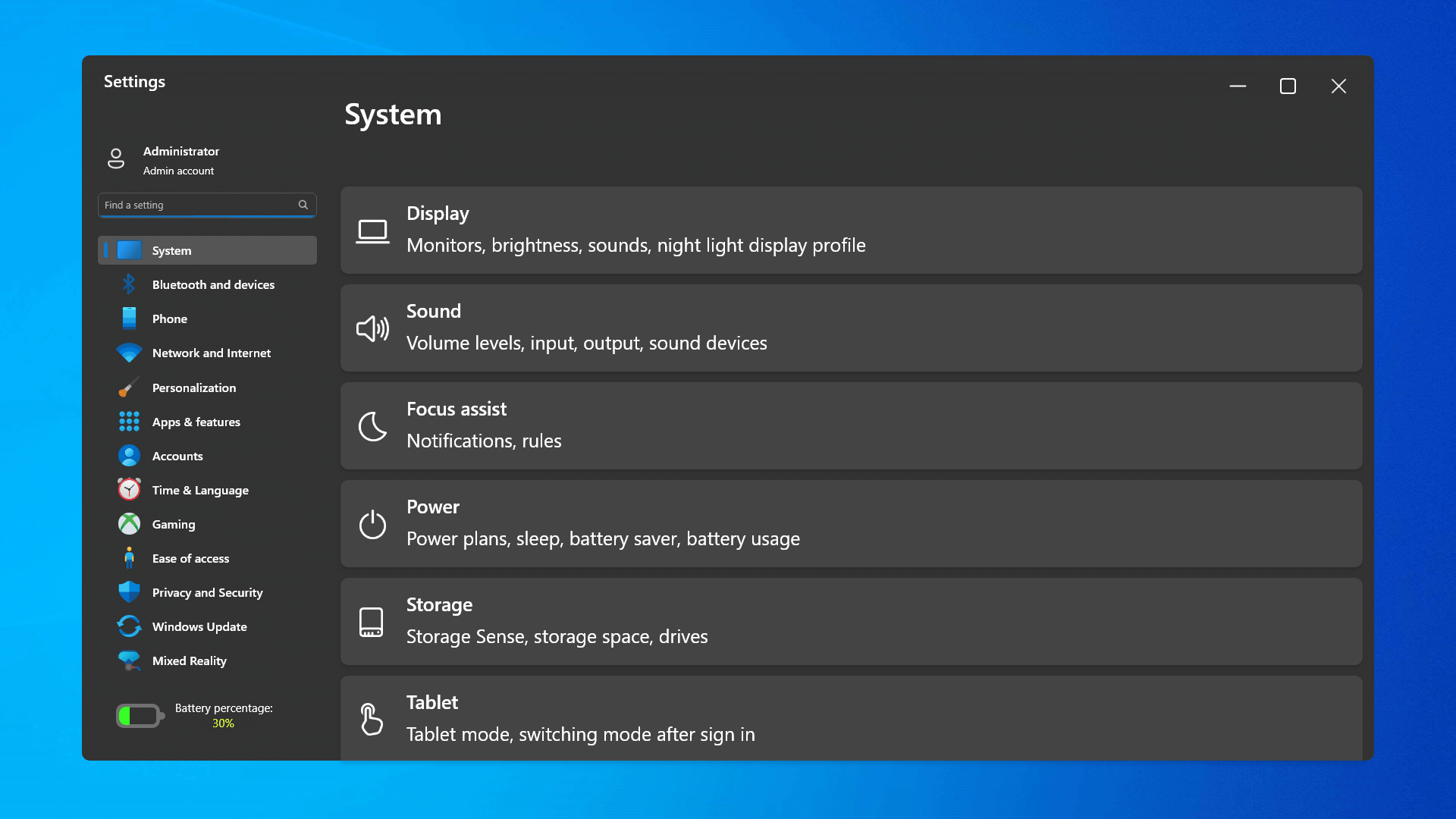 The settings app also has gone through visual and design changes. It has a new design that is very visually appealing and navigation has been simplified and more organized. Finding the right and desired setting is much faster and clearer now.
The settings app also has gone through visual and design changes. It has a new design that is very visually appealing and navigation has been simplified and more organized. Finding the right and desired setting is much faster and clearer now.
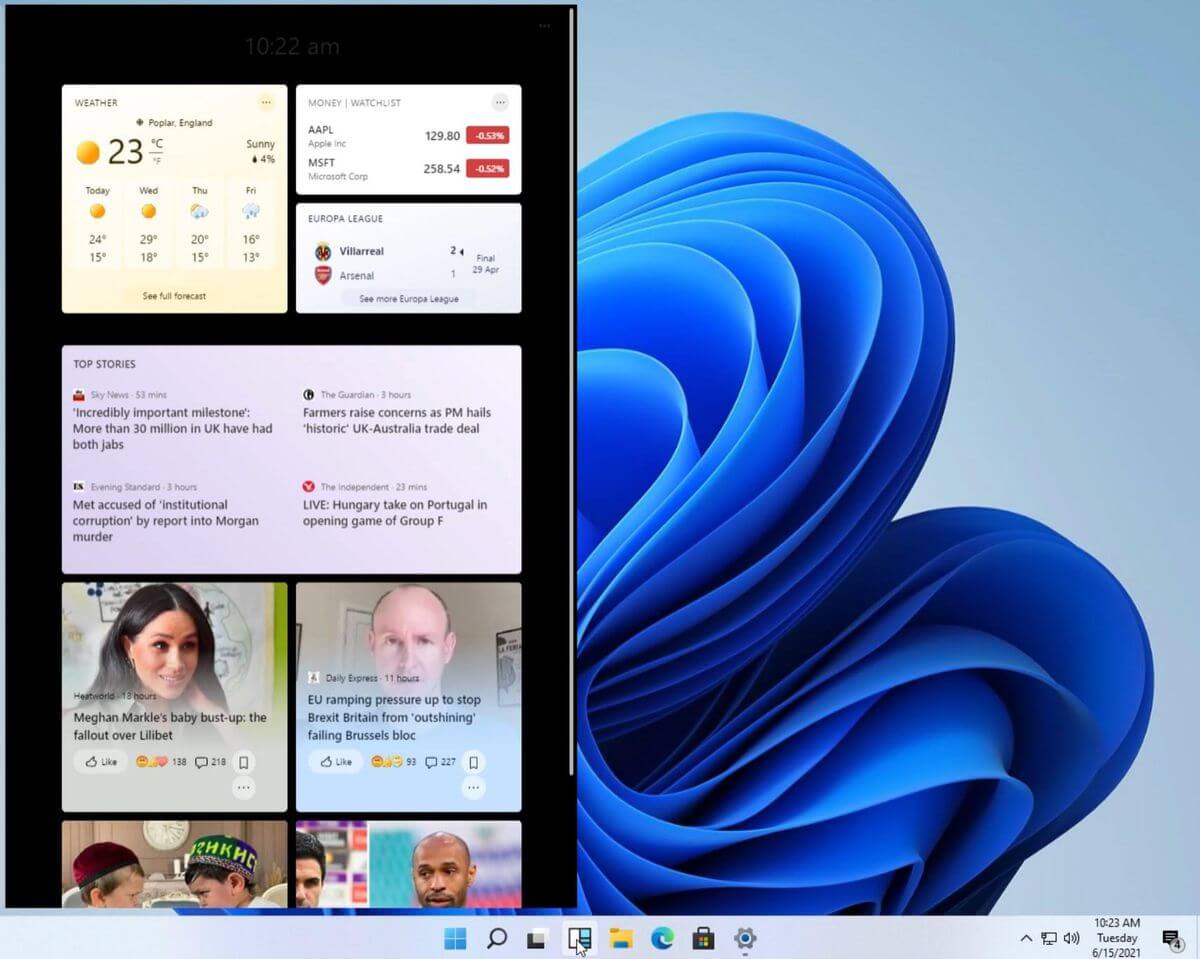 Yes, widgets are back but not like you remember them.
Instead of being all-time present at your desktop like once they used to be, now there is a button on the taskbar which brings the widget bar up that contains desired widgets. This way they are easily accessible and do not clutter desktops.
So far we have weather, news, calendar, and stocks widget but we will see how development on these goes. I expect to have community-made widgets like in old days for all of our needs.
Yes, widgets are back but not like you remember them.
Instead of being all-time present at your desktop like once they used to be, now there is a button on the taskbar which brings the widget bar up that contains desired widgets. This way they are easily accessible and do not clutter desktops.
So far we have weather, news, calendar, and stocks widget but we will see how development on these goes. I expect to have community-made widgets like in old days for all of our needs.
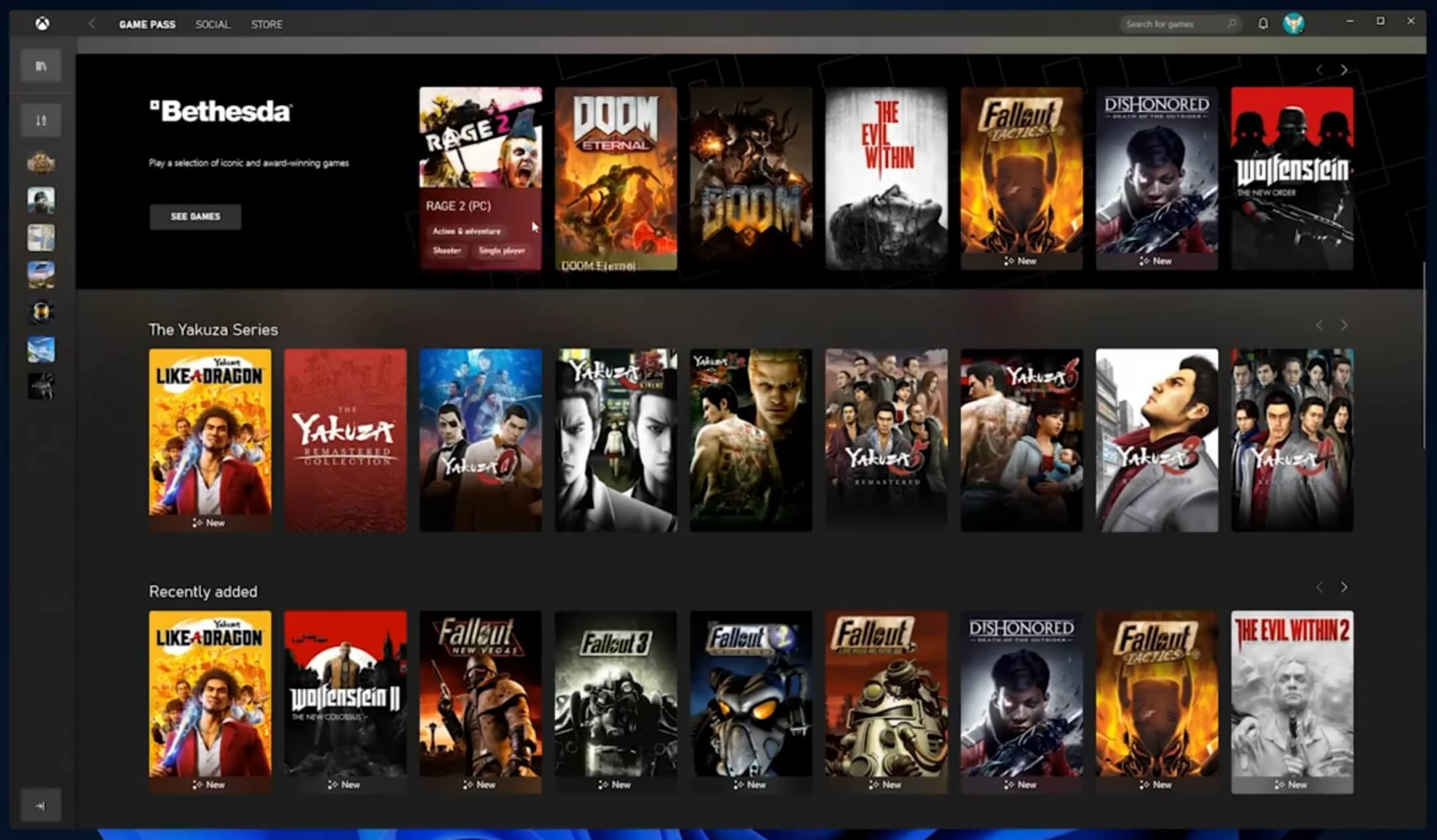 The new Xbox app is now integrated into Windows 11, offering quick access to Xbox Game Pass games, the social parts of the Xbox network, and the Xbox store.
The new Xbox app is now integrated into Windows 11, offering quick access to Xbox Game Pass games, the social parts of the Xbox network, and the Xbox store.
 As widely known by now Windows 11 will require you to have a TPM 2.0 module capable CPU in order to install it.
This system requirement has caused a lot of controversies but essentially it seems that MS's goal is to protect your personal data by using this module.
The upside of course is that your data will be protected much more than in previous Windows versions, the downside, of course, will be that you will need newer hardware to run OS on it.
and that is essentially it, keep on tuned on more Windows 11 information and overall articles tied to PC and technology here at errortools.com
As widely known by now Windows 11 will require you to have a TPM 2.0 module capable CPU in order to install it.
This system requirement has caused a lot of controversies but essentially it seems that MS's goal is to protect your personal data by using this module.
The upside of course is that your data will be protected much more than in previous Windows versions, the downside, of course, will be that you will need newer hardware to run OS on it.
and that is essentially it, keep on tuned on more Windows 11 information and overall articles tied to PC and technology here at errortools.com 

