Error Code 0xC1900101, 0x30018? - What is it?
Users, when upgrading to Windows 10 from Windows 7 or Windows 8/8.1, or when upgrading to a new version, build, service pack, or major update of Windows 10, can encounter error code 0xC1900101, 0x30018. Windows 10 installation fails and stops or hangs. During the installation process, it will reach a certain maximum limit (normally at 6% or 32%) then reverts back to the previous version of the operating system and displays the following message:
We couldn’t install Windows 10. We’ve set your PC back to the way it was right before you started installing Windows 10.
0xC1900101 – 0x30018 The installation failed in the FIRST_BOOT phase with the error during the SYSPREP operation.
Solution
 Error Causes
Error Causes
In attempting to fix Error Code 0xC1900101-0x30018, it is vital to know what causes this issue. The most probable causes of this error are:
- Incompatible hardware or driver
- Incompatible security programs or antivirus or incompatible utility software
- A device driver possibly stopped responding to setup.exe while on the installation process.
Further Information and Manual Repair
In fixing issues related to error codes, it is best to employ manual repair methods. Using these methods helps users pinpoint the root causes of the issue and apply solutions permanently to fix the issues. While most manual repair methods can be done by every Windows user, even those without technical abilities, there are certain cases where help from a Windows professional is needed. If you’re not up to facing risks in implementing manual methods yourself, consider getting help from a professional Windows technician or you can use a powerful automated tool. In fixing Error Code 0xC1900101-0x30018, you can repeat the same steps used for 0xc000021a (Method One) or you can try doing the following:- Disable or uninstall your Antivirus program before proceeding to upgrade the system
- Ensure that the machine name is simple (having at least 8 characters) with no special characters like hyphens or dashes.
- Restart the device a few times then try again.
- Disable General USB Devices such as the Smart Card Reader.
- If you use an SCSI hard disk, ensure that you have available drivers you can use for your storage such as a thumb drive and make sure that it is connected. During the Windows 10 setup, select the Custom Advanced Option and use the Load Driver command to be able to load the suitable driver for the SCSI drive. If this fails, try switching to an IDE-based hard disk.
- You can now perform a clean boot. Restart your device then try again.
- If you are using the .ISO file for upgrading the system, you need to disconnect from the Internet first before proceeding to the setup. If you are connected to Wi-Fi or by Ethernet (LAN), make sure to disable both connections then you can proceed to set up again.
- If you’re performing the update through Windows Update, once the download reaches 100%, disconnect from the Internet, and then proceed with the installation.
NOTE: If this fails, if possible, you can try using the .ISO file in upgrading.
- Switch to a local account if the device is connected to a domain.
- Disconnect all external devices attached to the computer such as gaming controllers, printers, or USB keys.
If you’re using Windows Update in installing Windows 10, you can implement the following:
- Open the Command Prompt window by pressing Windows Key + X. Select Command Prompt (Admin) from the menu.
- Stop the BITS, Cryptographic, MSI Installer, and the Windows Update Services. In order to do this, Type or Copy and Paste the following commands one at a time:
NOTE: Don’t forget to hit Enter after every command.
net stop wuauserv
net stop cryptSvc
net stop bits
net stop msiserver
- Rename the Catroot2 and SoftwareDistribution In order to do this, Type or Copy and Paste the following commands one at a time:
NOTE: Don’t forget to hit Enter after every command.
ren
C:WindowsSoftwareDistribution SoftwareDistribution.old
ren
C:WindowsSystem32catroot2 Catroot2.old
- Restart the BITS, Cryptographic, MSI Installer, and the Windows Update Services. In order to do this, Type or Copy and Paste the following commands one at a time:
NOTE: Don’t forget to hit Enter after every command.
net start wuauserv
net start cryptSvc
net start bits
net start msiserver
- Type Exit in the Command Prompt then close the Command Prompt window then restart the computer.

 Coursera was one of the pioneers when it comes to college education online. When it started all courses were free and offered certificates if the taker has done tasks with a passing grade. Today not everything is free but still, there are tons of free courses that can help you to learn something new and to advance in your work or hobby.
Google is using the Coursera platform to deliver its courses to the audience and besides google a lot of academic professors from Princeton, Stanford, John Hopkins and many more are presently offering their course material.
Coursera was one of the pioneers when it comes to college education online. When it started all courses were free and offered certificates if the taker has done tasks with a passing grade. Today not everything is free but still, there are tons of free courses that can help you to learn something new and to advance in your work or hobby.
Google is using the Coursera platform to deliver its courses to the audience and besides google a lot of academic professors from Princeton, Stanford, John Hopkins and many more are presently offering their course material.
 edX has evolved from MITx, MIT’s free initiative to place some free academic lectures from its classrooms free into the world. Since it was rebranded into edX it started including other big university names like Berkeley, University of Texas System, Harvard, and many more.
Since its infant days, edX has expanded and included many areas that it offers coursework from arts to science. Certificated today are mostly not free but course videos are, so if you care to learn and not wave certificates around this is a great place to do it.
edX has evolved from MITx, MIT’s free initiative to place some free academic lectures from its classrooms free into the world. Since it was rebranded into edX it started including other big university names like Berkeley, University of Texas System, Harvard, and many more.
Since its infant days, edX has expanded and included many areas that it offers coursework from arts to science. Certificated today are mostly not free but course videos are, so if you care to learn and not wave certificates around this is a great place to do it.
 Udemy has a little different approach to course material than previously mentioned websites. Teachers on Udemy are mostly people that are working in a given field. Programmers will teach programming, fitness instructors will teach training, etc.
There are vas variety of topics even on lifestyle, hobbies even gaming to more serious ones like software developing hardware, etc.
There are free courses but mostly are one-time purchases with unlimited access to course material and with frequent discounts udemy might be a good place to look if you can find anything interesting.
Udemy has a little different approach to course material than previously mentioned websites. Teachers on Udemy are mostly people that are working in a given field. Programmers will teach programming, fitness instructors will teach training, etc.
There are vas variety of topics even on lifestyle, hobbies even gaming to more serious ones like software developing hardware, etc.
There are free courses but mostly are one-time purchases with unlimited access to course material and with frequent discounts udemy might be a good place to look if you can find anything interesting.
 Alison is kind of Udemy if we are talking about course material and who is teaching, the difference however is that it has more free content and it is one of the rare websites on this list that has Language courses.
Courses vary from beginner level to more advanced ones.
Alison is kind of Udemy if we are talking about course material and who is teaching, the difference however is that it has more free content and it is one of the rare websites on this list that has Language courses.
Courses vary from beginner level to more advanced ones.
 Udacity was also one of the earlier websites to offer free courses, in today’s world it still has free material but there is also paying one.
The big difference from other competitors is that Udacity focuses mostly on programming, data science, and web development and it is very strong in this field. There are no courses about art. Music or similar, mostly IT stuff is covered here.
If this is something that interests you, make a free account and give it a go.
Udacity was also one of the earlier websites to offer free courses, in today’s world it still has free material but there is also paying one.
The big difference from other competitors is that Udacity focuses mostly on programming, data science, and web development and it is very strong in this field. There are no courses about art. Music or similar, mostly IT stuff is covered here.
If this is something that interests you, make a free account and give it a go.
 Codecademy is a website mainly focused on teaching you how to code. Pro plan is there but there are a lot of basic and free courses on the mentioned subject.
The curriculum is really wide covering Python, R, Java, JavaScript, SQL, Ruby, C#, C++, Swift, PHP, HTML, CSS and more so I am sure that if you are interested in coding this would be a pretty good place to find things.
Besides pure language coding courses site offers also, Cybersecurity, Web design, Data science, web development, Game Development, Mobile Development, and many more courses on provided subjects.
Codecademy is a website mainly focused on teaching you how to code. Pro plan is there but there are a lot of basic and free courses on the mentioned subject.
The curriculum is really wide covering Python, R, Java, JavaScript, SQL, Ruby, C#, C++, Swift, PHP, HTML, CSS and more so I am sure that if you are interested in coding this would be a pretty good place to find things.
Besides pure language coding courses site offers also, Cybersecurity, Web design, Data science, web development, Game Development, Mobile Development, and many more courses on provided subjects.
 Academic Earth has been built with one simple premise: Everyone deserves access to education.
Lead by this kind of mindset on Academic Earth you will find well, academic courses similar to ones found on edX and Coursera, but from mentioned sites here all courses are free and you will find only academic ones, there are no entrepreneur or expert courses here, just pure academic ones.
If you wish to see and learn something the way it is taught in Harvard, Berkeley, MIT, etc this is the place for you.
Academic Earth has been built with one simple premise: Everyone deserves access to education.
Lead by this kind of mindset on Academic Earth you will find well, academic courses similar to ones found on edX and Coursera, but from mentioned sites here all courses are free and you will find only academic ones, there are no entrepreneur or expert courses here, just pure academic ones.
If you wish to see and learn something the way it is taught in Harvard, Berkeley, MIT, etc this is the place for you.
 Khan academy is completely free and it is offering courses matching certain grades for children. It is offering courses for all 8 years of elementary school, math courses for high school and college with some coursework on topics like science, arts & humanities, reading, life skills, etc.
Despite not being on the same level as some university courses presented on other mentioned websites Khan Academy is a good place to learn a lot of basic skills that you could build upon later.
Khan academy is completely free and it is offering courses matching certain grades for children. It is offering courses for all 8 years of elementary school, math courses for high school and college with some coursework on topics like science, arts & humanities, reading, life skills, etc.
Despite not being on the same level as some university courses presented on other mentioned websites Khan Academy is a good place to learn a lot of basic skills that you could build upon later.

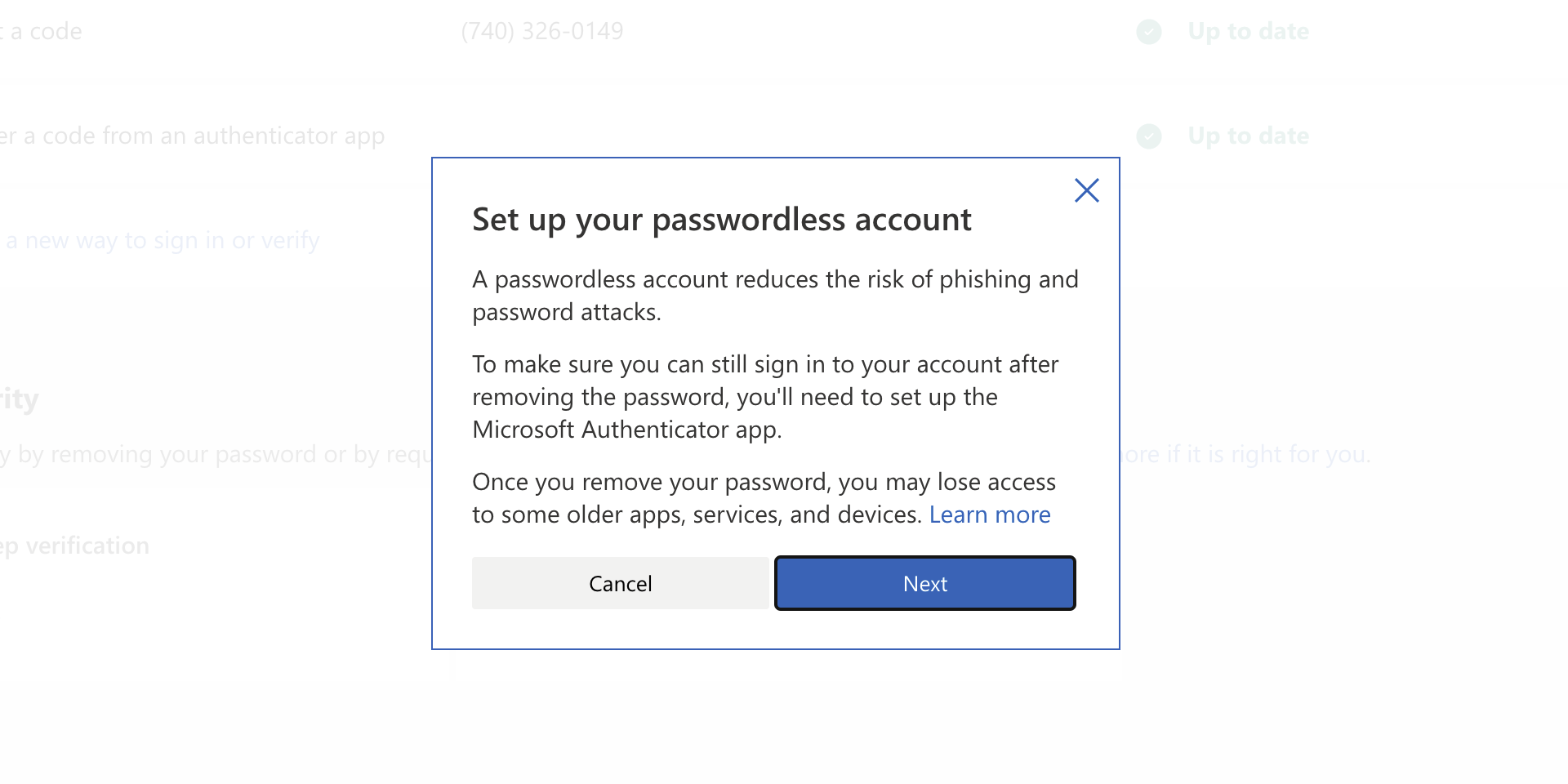 As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.
As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.
