Hello and welcome to another problem-solving tutorial on errortools.com. Today we will be solving error 0x80070057, we could not format the selected partition which occurs during setup and installation when performing a clean install of Windows from a USB drive.
So, you have backed up your files and decided to format and do clean WIndows installation, you have your USB ready, you reboot the system, plug in USB, start Windows setup, choose the hard drive on which you want to do a clean install and then this happens.
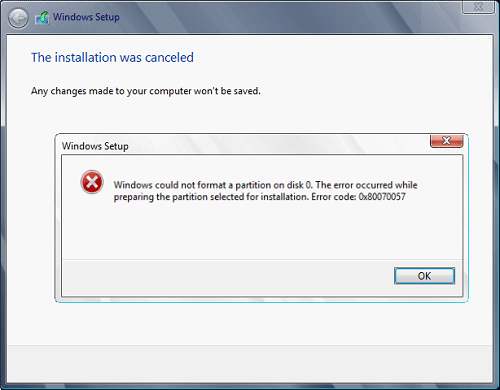 This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.

'Error 1603: A fatal error occurred during installation.'It indicates a problem occurred during the installation process and unsuccessful installation.
 Error Causes
Error CausesDISM.exe /Online /Cleanup-image /Scanhealth DISM.exe /Online /Cleanup-image /Restorehealth
Google's Pixel smartphone is one if not the best Android smartphone on the market. It regularly gets updates and Google is really trying to keep it as a top choice for Android smartphone users. One of the new things that Google has released for its smartphone series is a new emergency dialer.

With an emergency dialer, you will be able to quickly access local contact information for police, fire, and medical services. This dialer is able to contact before mentioned services even when the phone is locked and when you are traveling.
The idea is to quickly access the default emergency number no matter in which country you are currently in, service will find the appropriate number and set it as default so if you need it there is no delay in searching for the appropriate number and dialing it.
Once the service is enabled on the device you can swipe up and tap Emergency call without unlocking your phone or you can press and hold the power button for five seconds and tap Emergency.
If you have a Pixel smartphone go to the Google support page and follow instructions on how to enable this service. It costs nothing and it could potentially even save your life.
 Error Causes
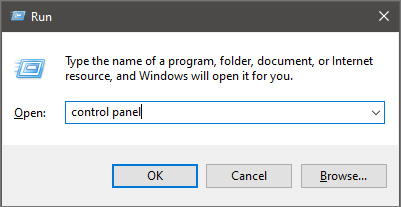
Error Causes Once run dialog is shown type in it control panel as shown in the picture and press OK
Once run dialog is shown type in it control panel as shown in the picture and press OK
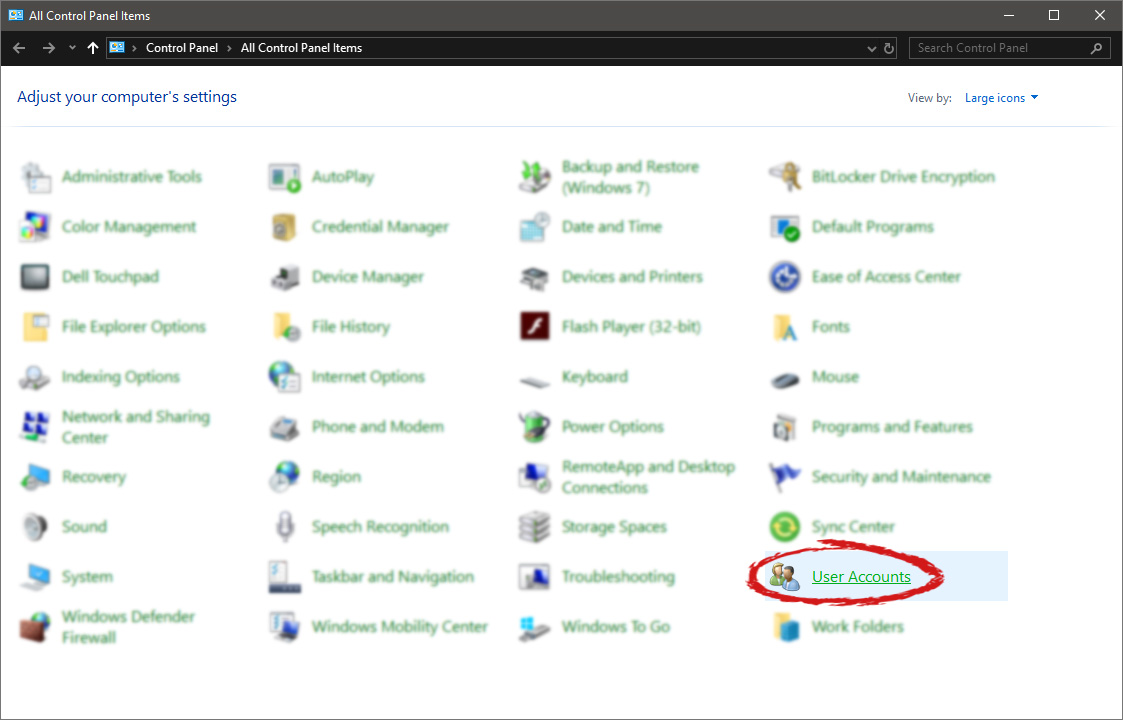
 If you have followed the steps precisely, you should be now in the control panel of Windows 10. Click on the top-right view and choose large icons. The Control panel will switch to a grid-like view, in the current view go to the far-right and almost bottom icon where it says User Accounts and click on it.
If you have followed the steps precisely, you should be now in the control panel of Windows 10. Click on the top-right view and choose large icons. The Control panel will switch to a grid-like view, in the current view go to the far-right and almost bottom icon where it says User Accounts and click on it.
 User account settings
User account settings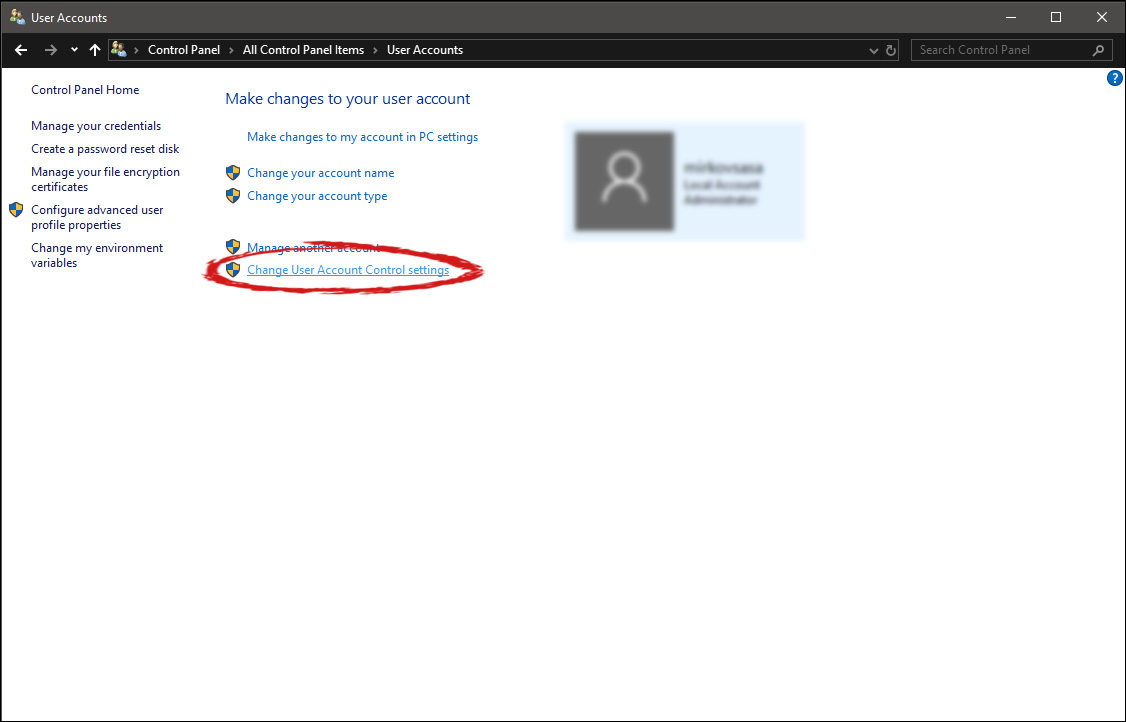 Once you click on the link you will be presented with a User account control slider on the left and a brief explanation on the right
Once you click on the link you will be presented with a User account control slider on the left and a brief explanation on the right
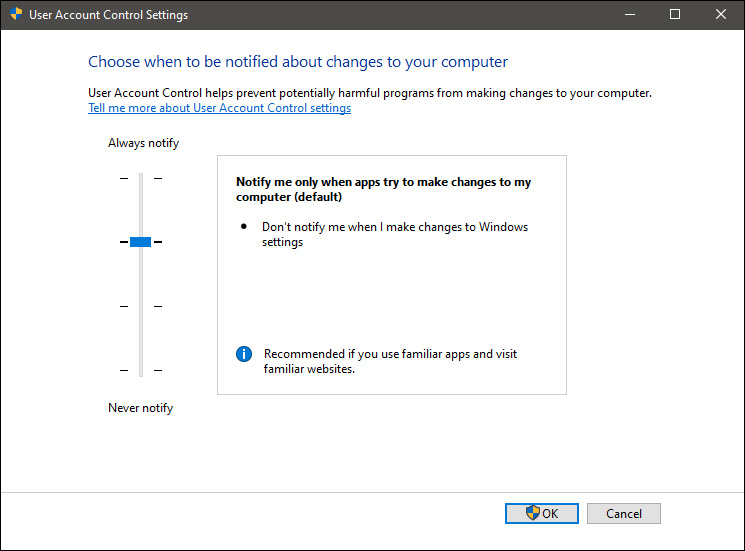 Here in the picture, we see Windows default setting and an explanation of when and how he will notify you. If you wish to turn all notifications linked to programs changing computer or you making windows changes, click on the left slider and bring it all the way to the bottom where it says never notify me. If you prefer some notifications try to find which of the remaining 3 settings best suit your needs. Once you are done and satisfied with your choice click on OK.
Here in the picture, we see Windows default setting and an explanation of when and how he will notify you. If you wish to turn all notifications linked to programs changing computer or you making windows changes, click on the left slider and bring it all the way to the bottom where it says never notify me. If you prefer some notifications try to find which of the remaining 3 settings best suit your needs. Once you are done and satisfied with your choice click on OK.