ExpressFiles is a program developed by Express Solutions. A number of Anti-Virus programs have flagged this program as a Potentially Unwanted Application. In many instances, it is bundled with additional programs on installation.
The program claims it offers users easy to search for various currently popular search terms. During our testing, the software never displays any search results, no matter the search words.
Upon installation and setup, it defines an auto-start registry entry which makes this program run on each Windows boot for all user logins. A scheduled task is added to Windows Task Scheduler in order to launch the program at various scheduled times. The program defines an exception rule in Windows Firewall, allowing it to connect to the internet without limitations and auto-update itself.
About Browser Hijackers
Precisely what is a PUP?
If you’ve ever downloaded a free application or shareware, chances are high that the computer can get installed with a bunch of unwanted applications. A PUA / PUP (potentially unwanted application / potentially unwanted program) is a software program that comes bundled with free software and you consent to install it on your PC. These are programs you almost certainly don’t want on your computer simply because it doesn’t give any valuable service.
Despite being regarded as very detrimental, PUPs aren’t always viruses or malware One simple difference between PUP and malware is distribution. Malware is normally dropped by silent installation vectors like drive-by downloads while PUP gets installed with the consent of the computer user, who purposefully or unknowingly approves the PUP installation on its PC. Having said that, there is no doubt that PUPs remain bad news for PC users as they can be incredibly damaging to the computer in numerous ways.
Exactly how do unwanted programs look like?
Potentially Unwanted Programs appear in different forms and varieties, however, in the majority of instances, they are adware programs that exhibit irritating pop-up ads and advertisements on websites you explore. In addition, the majority of free programs these days come with some unwanted add-ons; in most cases an internet browser toolbar or browser modification like a homepage hijacker. They’ll keep track of your online routines, redirect your search results to risky websites where viruses can be downloaded and installed, hijack your home page, and slow your browser down to a crawl.
Potentially Unwanted Programs occasionally act quite much like computer viruses or spyware. They might carry keyloggers, dialers, browser hijackers, and tracking components that gather system details, or tracks customer habits and relays this information to third-party firms. Even if the PUPs really aren’t basically malicious, these software programs still do absolutely nothing good on your personal computer – they will take valuable system resources, slow down your PC, weaken your computer security, and make your system more susceptible to trojans.
How do you avoid PUPs?
• Read cautiously before accepting the license agreement as it may have a clause about PUPs.
• Always opt for the custom if you’re presented an option between “Custom” and “Recommended” Installations – never click Next, Next, Next blindly.
• Have a top-notch antivirus program like Safebytes Anti-Malware which can protect your computer from PUPs. As soon as you install this software, protection from malware and PUPs is already switched on.
• Think carefully before you download any kind of shareware or freeware. Disable or get rid of toolbars and browser extensions you don’t really need.
• Only use official product websites for downloading programs. Stay away from download portals altogether as most websites compel users to download the software using their own download manager, which is often bundled up with some sort of PUPs.
What To Do If You Cannot Install Any Anti-Malware?
All malware is bad, but certain types of malicious software do a lot more damage to your computer than others. Some malware types modify browser settings by adding a proxy server or modify the PC’s DNS settings. In these instances, you will be unable to visit some or all of the websites, and therefore not able to download or install the required security software to remove the infection. If you are reading this right now, you have perhaps recognized that a malware infection is a reason for your blocked web connectivity. So how to proceed when you want to install an anti-malware application like Safebytes? Follow the instructions below to eliminate malware by alternative methods.
Install in Safe Mode
The Windows-based PC comes with a special mode called “Safe Mode” where just the bare minimum required applications and services are loaded. If the malware is set to load immediately when the computer starts, shifting to this mode may well prevent it from doing so. In order to enter into Safe Mode or Safe Mode with Networking, press the F8 key while the PC is starting up or run MSConfig and locate the “Safe Boot” options under the “Boot” tab. As soon as you restart the PC into Safe Mode with Networking, you could download, install, and update anti-malware software from there. Right after installation, run the malware scanner to get rid of standard infections.
Utilize an alternate internet browser to download antivirus software
Web-based malware could be environment-specific, targeting a specific web browser or attacking particular versions of the web browser. If you’re not able to download the anti-virus application using Internet Explorer, this means the virus is targeting IE’s vulnerabilities. Here, you need to switch to a different web browser such as Chrome or Firefox to download the Safebytes Anti-malware program.
Install and run antivirus from a Thumb drive
Here’s yet another solution which is creating a portable USB anti-virus software that can scan your computer for malware without the need for installation. Try these simple actions to clean up your infected computer using portable anti-malware.
1) Download Safebytes Anti-Malware or Microsoft Windows Defender Offline onto a clean PC.
2) Mount the pen drive on the same PC.
3) Run the setup program by double-clicking the executable file of the downloaded software, which has a .exe file extension.
4) Select the drive letter of the USB drive as the location when the wizard asks you exactly where you would like to install the anti-malware. Follow activation instructions.
5) Now, insert the thumb drive into the corrupted PC.
6) Run the Safebytes Anti-malware directly from the pen drive by double-clicking the icon.
7) Click the “Scan” button to run a full computer scan and remove viruses automatically.
Overview of SafeBytes Anti-Malware
If you are looking to download the anti-malware program for your computer, there are lots of tools in the market to consider nonetheless, you just cannot trust blindly anyone, irrespective of whether it is free or paid software. A few of them do a great job in removing threats while some will ruin your PC by themselves. You need to pick a company that develops industry-best antimalware and has achieved a reputation as trustworthy. When considering commercial tool options, most people opt for well-known brands, such as SafeBytes, and they are quite happy with it.
SafeBytes anti-malware is really a powerful, very effective protection software made to help users of all levels of computer literacy in detecting and removing malicious threats out of their computer. Using its outstanding protection system, this utility will quickly detect and get rid of the majority of the security threats, which include adware, viruses, browser hijackers, ransomware, PUPs, and trojans.
SafeBytes anti-malware takes computer protection to a totally new level with its advanced features. Here are a few typical features present in this software:
Live Protection: SafeBytes offers complete and real-time security for your laptop or computer. It’ll regularly monitor your computer for hacker activity and also gives end-users superior firewall protection.
Most Reliable AntiMalware Protection: With its enhanced and sophisticated algorithm, this malware elimination tool can find and eliminate the malware threats hiding in your PC effectively.
“Fast Scan” Features: SafeBytes’s high-speed malware scanning engine minimizes scanning times and extends battery life. Simultaneously, it will effectively identify and remove infected computer files or any online threat.
Web Protection: SafeBytes checks and gives a unique safety ranking to each and every website you visit and block access to webpages considered to be phishing sites, thus safeguarding you from identity theft, or known to contain malicious software.
Low CPU/Memory Usage: SafeBytes is well known for its low effect on computer resources and great detection rate of diverse threats. It runs quietly and efficiently in the background so you’re free to use your PC at full power all of the time.
24/7 Premium Support: SafeBytes gives you 24/7 technical support, automatic maintenance, and upgrades for the best user experience.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove ExpressFiles without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by ExpressFiles
Files:
%APPDATAExpressFilescurrent-cloud.html
%COMMONDESKTOPExpressFiles.lnk
%COMMONSTARTMENUExpressFilesExpressFiles.lnk
%COMMONSTARTMENUExpressFilesUninstall.lnk
%PROGRAMFILESExpressFilescurrent-cloud.de.html
%PROGRAMFILESExpressFilescurrent-cloud.en.html
%PROGRAMFILESExpressFilescurrent-cloud.fr.html
%PROGRAMFILESExpressFilescurrent-cloud.ru.html
%PROGRAMFILESExpressFilesEFupdater.exe
%PROGRAMFILESExpressFilesExpressDL.exe
%PROGRAMFILESExpressFilesExpressFiles.exe
%PROGRAMFILESExpressFilesuninstall.exe
%WINDIRTasksExpress Files Updater.job
%APPDATAExpressFiles
%COMMONSTARTMENUExpressFiles
%PROGRAMFILESExpressFileslanguage
%PROGRAMFILESExpressFiles
Registry:
key ExpressFiles.exe at HKEY_LOCAL_MACHINESOFTWAREConduitAppPaths.
key ExpressFiles at HKEY_CURRENT_USERSoftware.
key ExpressFiles at HKEY_LOCAL_MACHINESOFTWARE.
key ExpressFiles at HKEY_USERS.DEFAULTSoftware.
HKEY_CLASSES_ROOTMagnetsshellopencommand
value $PROGRAMFILESExpressFilesExpressDL.exe at HKEY_LOCAL_MACHINESYSTEMControlSet001ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.
value $PROGRAMFILESExpressFilesExpressDL.exe at HKEY_LOCAL_MACHINESYSTEMControlSet002ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.
value $PROGRAMFILESExpressFilesExpressDL.exe at HKEY_LOCAL_MACHINESYSTEMControlSet003ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.
value $PROGRAMFILESExpressFilesExpressFiles.exe at HKEY_LOCAL_MACHINESYSTEMControlSet001ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.
value $PROGRAMFILESExpressFilesExpressFiles.exe at HKEY_LOCAL_MACHINESYSTEMControlSet002ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.
value $PROGRAMFILESExpressFilesExpressFiles.exe at HKEY_LOCAL_MACHINESYSTEMControlSet003ServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList.



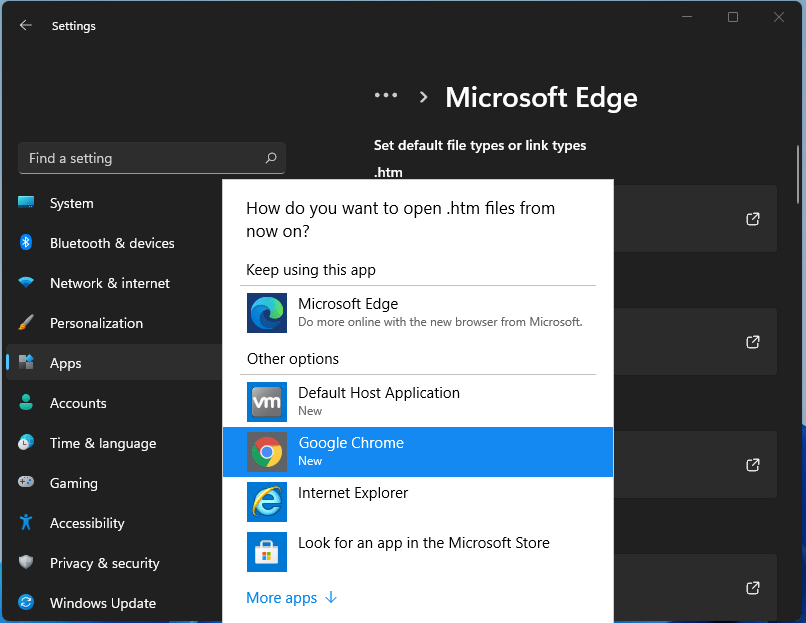 For anyone who is not aware, when Windows 11 was released if you wanted to switch to another browser you had to go into the settings app and choose the default browser for different types of file extensions like HTML, HTM, PDF for opening on the web, etc. Of course, this was completely unnecessary and it was not well received by users. So after some time, Microsoft backpedaled to standard one click, choose your default browser solution that existed in the previous version of Windows OS.
Altho sometimes Microsoft knows how to irritate its users base, it is good to know that they can also listen and fix things that are required.
For anyone who is not aware, when Windows 11 was released if you wanted to switch to another browser you had to go into the settings app and choose the default browser for different types of file extensions like HTML, HTM, PDF for opening on the web, etc. Of course, this was completely unnecessary and it was not well received by users. So after some time, Microsoft backpedaled to standard one click, choose your default browser solution that existed in the previous version of Windows OS.
Altho sometimes Microsoft knows how to irritate its users base, it is good to know that they can also listen and fix things that are required. 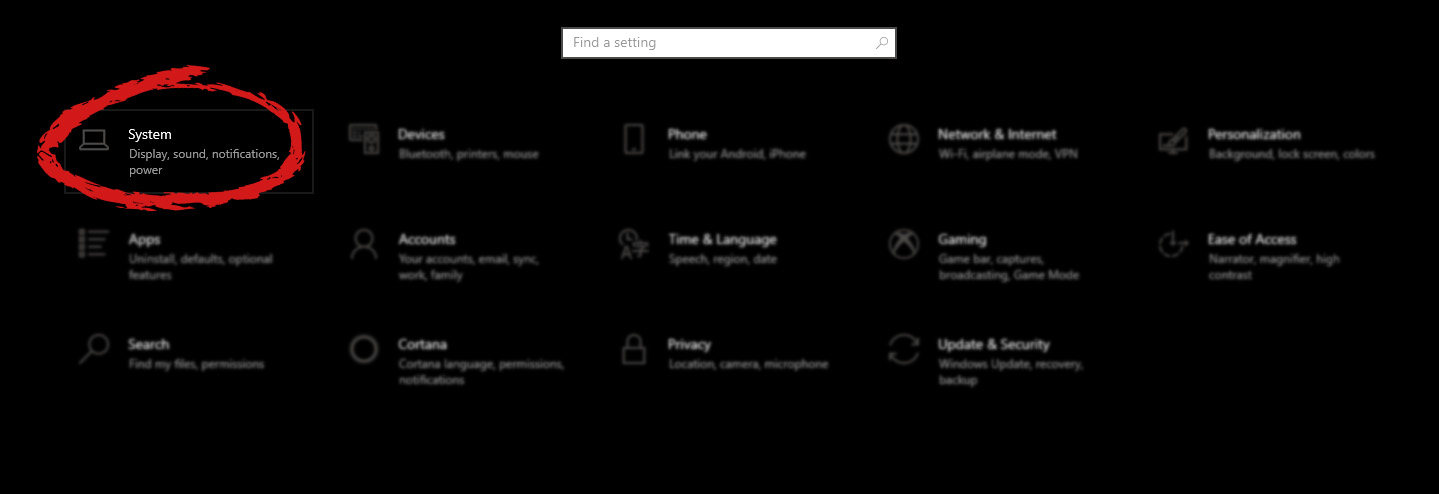 Once you are in the system, on the left tabs find and click on Clipboard.
Once you are in the system, on the left tabs find and click on Clipboard.
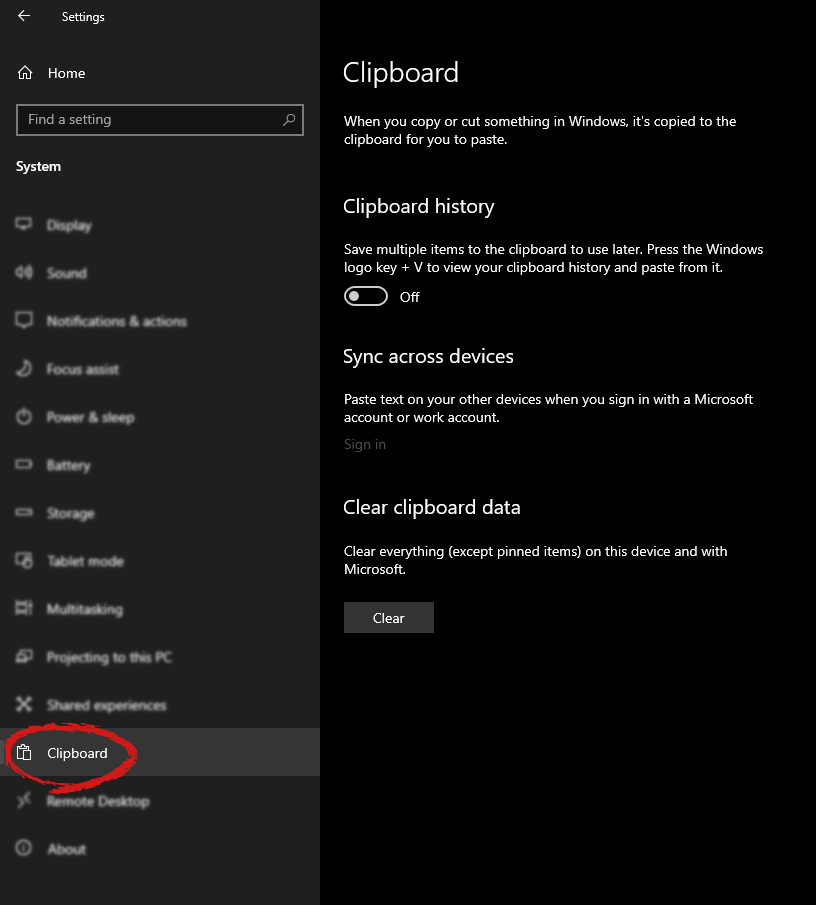 If you are not logged in to your Microsoft account do so on the right panel by locating Sync across devices and click on sign in.
If you are not logged in to your Microsoft account do so on the right panel by locating Sync across devices and click on sign in.
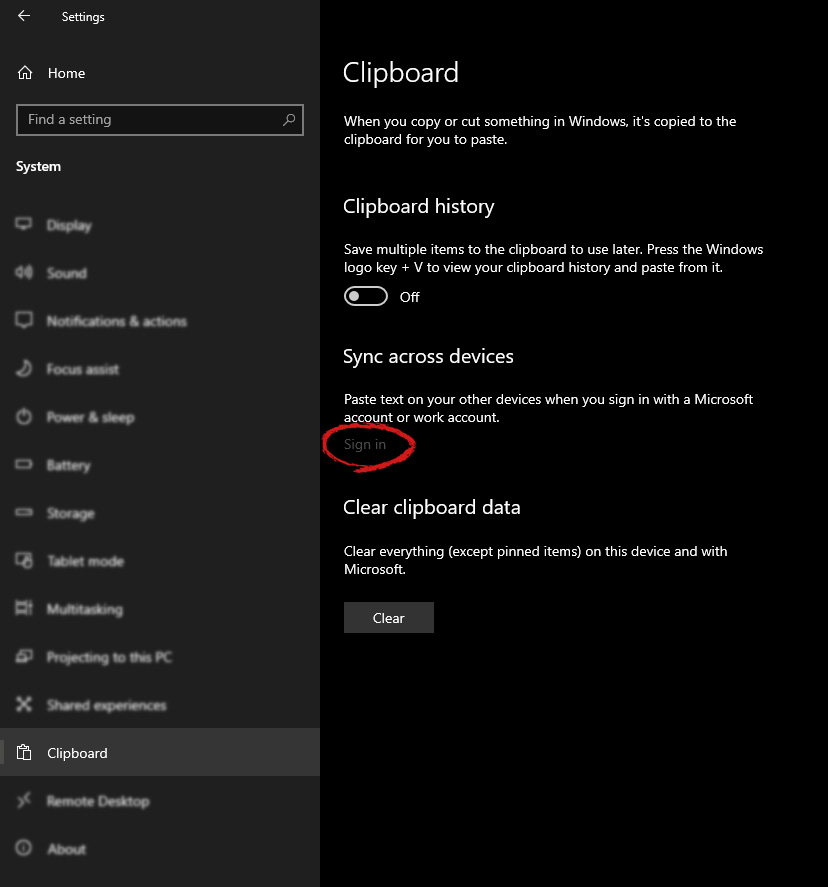 When you are signed in click on the option to turn it on.
When you are signed in click on the option to turn it on.
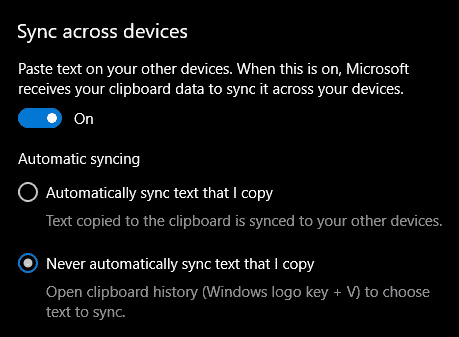 One option is turned ON, you will be greeted with two choices, to copy everything from the clipboard automatically or to choose text which you want to sync and paste it with ⊞ WINDOWS + V. Choose whatever better suits your needs, and you are done.
Repeat these steps for other devices and you are done.
One option is turned ON, you will be greeted with two choices, to copy everything from the clipboard automatically or to choose text which you want to sync and paste it with ⊞ WINDOWS + V. Choose whatever better suits your needs, and you are done.
Repeat these steps for other devices and you are done. 