BringMeSports is a browser extension developed by Mindspark Inc. that lets you watch live sports streams, follow sports scores, and catch up on the latest news from the sports world.
BringMeSports installs an extension into your browser that replaces your default home page with the MyWebSearch starting page, it also replaces your default search engine, shows additional ads, and while running, collects personal and web browsing data that is later sent back to be Sold / Forwarded to serve ads. While browsing the internet with this extension installed, you will see additional ads and sponsored links appear in your search results. It may even show pop-up ads.
Several anti-virus scanners have marked this extension as a Browser Hijacker and are therefore not recommended to keep on your computer.
About Browser Hijackers
Browser hijacking is a type of unwanted software, commonly a web browser add-on or extension, which causes modifications in web browser’s settings. Browser hijacker malware is created for many different reasons. The idea would be to force users to visit particular websites that are trying to increase their website visitor traffic and produce higher ad income. Although it might appear naive, all browser hijackers are damaging and therefore always regarded as security risks. Browser hijackers can even allow other harmful programs without your knowledge to further damage your personal computer.
Signs of browser hijack
There are various symptoms of browser hijacking. Here are a few of them:
1. you notice unauthorized changes to your Internet browser’s homepage
2. you find re-directed to websites you never meant to visit
3. the default search engine is changed and the web browser security settings have been lowered without your knowledge
4. you’re finding new toolbars you have never seen before
5. you observe numerous ads pop up on the browsers or computer screen
6. your web browser gets slow, buggy crashes frequently
7. you are blocked to access those sites of computer security solution providers.
Precisely how browser hijacker infects computers
Browser hijackers attack computer systems through malicious email attachments, downloaded infected computer files, or by going to infected internet sites. They could also come from add-on programs, also called browser helper objects (BHO), web browser extensions, or toolbars. A browser hijacker could also be installed as a part of freeware, shareware, demoware, and pirated programs. Common examples of browser hijackers include CoolWebSearch, Conduit, Coupon Server, OneWebSearch, RocketTab, Snap.do, Delta Search, and Searchult.com.
The existence of any browser hijacker malware on your computer might drastically diminish the web browsing experience, track your online activities that result in troublesome privacy concerns, create system stability problems and eventually cause your computer to slow down or to a practically unusable state.
How you can remove browser hijackers
Some hijackers could be removed by deleting the free software they were included with or by removing any extension you have recently added to your system. Having said that, many hijackers are quite tenacious and need specialized tools to eliminate them. And there’s no denying the very fact that the manual fixes and removal methods can certainly be a complicated job for a novice PC user. Also, there are plenty of risks associated with fiddling around with the system registry files.
What To Do If You Cannot Install Any Anti-Malware?
Every malware is bad and the consequences of the damage could vary based on the specific kind of malware. Certain malware variants alter internet browser settings by including a proxy server or modify the computer’s DNS configurations. In these instances, you will be unable to visit certain or all of the websites, and therefore unable to download or install the required security software to remove the infection. If you are reading this, odds are you’re stuck with a malware infection that is preventing you to download or install Safebytes Anti-Malware software on your system. Although this type of issue will be difficult to circumvent, there are a few actions you can take.
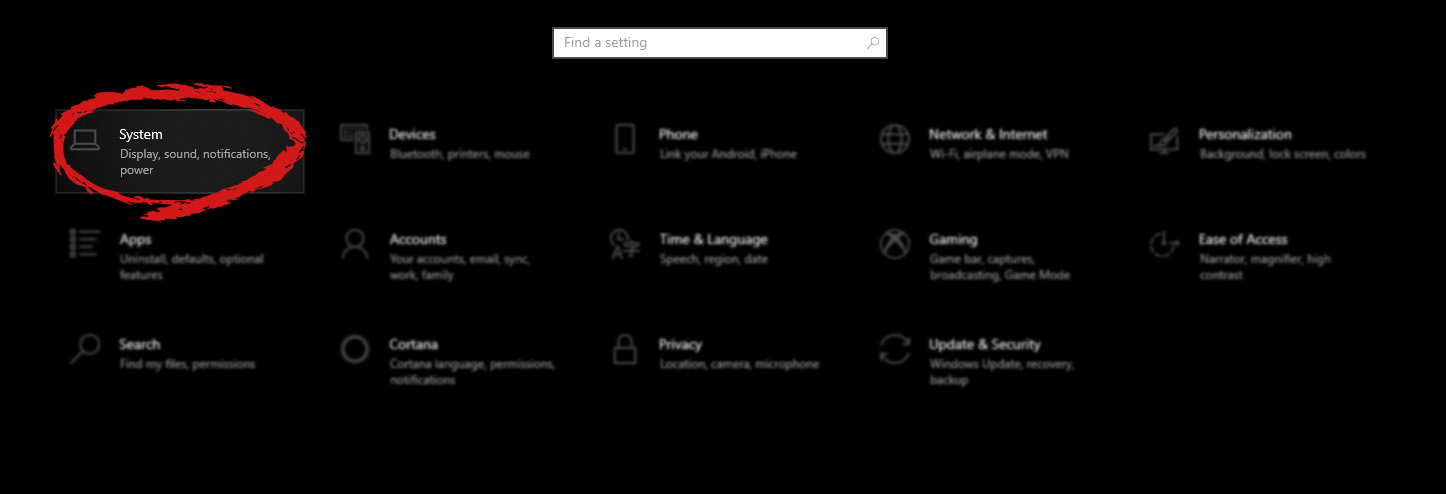
Install in Safe Mode
In Safe Mode, you could change Windows settings, uninstall or install some programs, and remove hard-to-delete malware. If the malicious software is set to load automatically when the computer starts, switching to this particular mode may prevent it from doing so. To enter into Safe Mode or Safe Mode with Networking, press F8 while the PC is starting up or run MSCONFIG and look for the “Safe Boot” options in the “Boot” tab. Once you are in Safe Mode, you can try to install your antivirus software application without the hindrance of the malware. After installation, run the malware scanner to get rid of most standard infections.
Utilize an alternate internet browser to download the anti-malware application
Web-based viruses could be environment-specific, aiming for a particular browser or attacking particular versions of the browser. The most effective way to overcome this issue is to select a web browser that is renowned for its security features. Firefox comprises built-in Malware and Phishing Protection to keep you safe online.
Create a portable anti-malware for removing viruses
Another option is to create a portable anti-malware program onto your USB stick. To run anti-virus using a USB flash drive, follow these simple steps:
1) Download the anti-malware on a virus-free PC.
2) Insert the USB drive on the same system.
3) Run the setup program by double-clicking the executable file of the downloaded software, which has a .exe file format.
4) Select the drive letter of the pen drive as the place when the wizard asks you exactly where you want to install the anti-malware. Do as instructed on the screen to complete the installation process.
5) Transfer the flash drive from the uninfected PC to the infected PC.
6) Run the Safebytes Anti-malware directly from the flash drive by double-clicking the icon.
7) Click the “Scan” button to run a full system scan and remove malware automatically.
Protect Your PC & Privacy With SafeBytes Anti-Malware
If you are looking to buy anti-malware for your PC, there are lots of brands and packages for you to consider. A few of them do a great job in getting rid of malware threats while some will affect your PC themselves. You need to be careful not to pick the wrong product, especially if you buy a premium program. One of the recommended software is SafeBytes AntiMalware. SafeBytes carries a very good reputation for top-quality service, and clients appear to be very happy with it.
Safebytes is among the well-established computer solutions firms, which provide this complete anti-malware application. Using its cutting-edge technology, this application will assist you to eliminate multiples types of malware such as viruses, PUPs, trojans, worms, ransomware, adware, and browser hijackers.
SafeBytes has got a variety of features that can help you protect your computer from malware attacks and damage. Let’s check out a few of them below:
Robust Anti-malware Protection: With a critically acclaimed malware engine, SafeBytes offers multilayered protection which is intended to catch and get rid of viruses and malware which are hidden deep in your computer system.
Active Protection: SafeBytes provides real-time active checking and protection against all known viruses and malware. It’ll continuously monitor your laptop or computer for hacker activity and also provides users with superior firewall protection.
“Fast Scan” Abilities: SafeBytes Anti-Malware has a multi-thread scan algorithm that works up to 5 times faster than any other anti-malware software.
Internet Security: Safebytes assigns all sites a unique safety score that helps you to have an idea of whether the webpage you are going to visit is safe to view or known to be a phishing site.
Lightweight Utility: SafeBytes is a lightweight and user-friendly anti-virus and anti-malware solution. Since it utilizes negligible computer resources, this application leaves the computer’s power exactly where it belongs: with you actually.
Premium Support: Support service is available for 24 x 7 x 365 days via email and chats to answer your queries.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove BringMeSports without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by BringMeSports
Files:
C:Program Filesbringmesports_1c chrome extensionbarBringMeSportsCrxSetup.exe
C:Program Filesbringmesports_1c chrome extensiont8sql.dll
C:Program Filesbringmesports_1c chrome extensionBringMeSportsCrxSetup.exe
C:Program Filesbringmesports_1c chrome extensionBringMeSportsCrxSetup.05F72CDF-5595-450B-9BAB-B1F6C606AAEC.exe
C:Program Filesbringmesports_1c chrome extensionBringMeSportsCrxSetup.1E4C7E0D-19E7-4C18-ADB3-3D45FC4BE84C.exe
C:Program Filesbringmesports_1c chrome extensionBringMeSportsCrxSetup.85D40F0D-233C-463F-8BAB-F6D446902D65.exe
C:Program Filesbringmesports_1c chrome extensionBringMeSportsCrxSetup.A94A3339-330B-4B96-B05A-B909E6BB85A1.exe
C:Program Filesbringmesports_1c chrome extensionBringMeSportsCrxSetup.EEE1FB37-85E3-49E8-BC44-36CC97CE3B73.exe
C:Program Filesbringmesports_1c chrome extensionsqlite3.dll
C:Program Files (x86)BringMeSports_1cEI
C:Program Files (x86)BringMeSports_1c
C:Users%USERNAME%AppDataLocalBringMeSports_1c
C:Users%USERNAME%AppDataLocalIAC
C:Users%USERNAME%AppDataLocalLowBringMeSports_1cEI
C:Users%USERNAME%AppDataLocalLowBringMeSports_1c
C:Users%USERNAME%AppDataRoamingMozillaFirefoxProfilesXXX.defaultextensionscffxtbr@BringMeSports_1c.com
C:Users%USERNAME%AppDataLocalGoogleChromeUserDataDefaultExtensionsllkjooekcinmdmojmfdjhidbakfpepod
Registry:
HKEY_CURRENT_USERMicrosoftInternet ExplorerApproved Extensions, value: F653D037-97FA-4755-98C1-7F382EEB59A7
HKEY_CURRENT_USERMicrosoftInternet ExplorerApproved Extensions, value: CC53BD19-7B23-43B0-AB7C-0E06C708CCED
HKEY_CURRENT_USERMicrosoftInternet ExplorerApproved Extensions, value: 002D1BA6-4766-4D7D-82B8-F49439C66F97
HKEY_CURRENT_USERMicrosoftInternet ExplorerToolbar, value: cc53bd19-7b23-43b0-ab7c-0e06c708cced
HKEY_CURRENT_USERWow6432NodeMicrosoftInternet ExplorerToolbar, value: cc53bd19-7b23-43b0-ab7c-0e06c708cced
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionExtPreApprovedbc61ca7a-6b81-47ec-b62d-ae1a236cadb9
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionExtPreApproved82c7004a-078e-468c-9c0f-2243618ff7cb
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionExtPreApproved6285c254-4465-4f8b-a009-5f42ab02c291
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionExtPreApprovedA8CC25D-66FF-41DF-B3B4-416079EF8F87
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionexplorerBrowser Helper Objectsf653d037-97fa-4755-98c1-7f382eeb59a7
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionexplorerBrowser Helper Objects02d1ba6-4766-4d7d-82b8-f49439c66f97
HKEY_CURRENT_USERWow6432NodeMicrosoftWindowsCurrentVersionExtPreApprovedf0c8ccc2-baaa-4236-ad0a-22b5a401b9ef
HKEY_CURRENT_USERWow6432NodeMicrosoftWindowsCurrentVersionExtPreApprovedA8CC25D-66FF-41DF-B3B4-416079EF8F87
HKEY_CURRENT_USERWow6432NodeMicrosoftWindowsCurrentVersionexplorerBrowser Helper Objectsf653d037-97fa-4755-98c1-7f382eeb59a7
HKEY_CURRENT_USERWow6432NodeMicrosoftWindowsCurrentVersionexplorerBrowser Helper Objects02d1ba6-4766-4d7d-82b8-f49439c66f97
HKEY_CURRENT_USERMicrosoftInternet ExplorerLow RightsElevationPolicyfa460720-7b38-421d-981c-66f0ae288fb9
HKEY_CURRENT_USERMicrosoftInternet ExplorerLow RightsElevationPolicya2b4da91-a53c-4a84-b486-40080de13a9b
HKEY_CURRENT_USERMicrosoftInternet ExplorerLow RightsElevationPolicy89b7ae32-9c52-41d6-a64d-14d7bdec9c58
HKEY_CURRENT_USERMicrosoftInternet ExplorerLow RightsElevationPolicy32a63172-5bcc-4d7e-9fe8-072eee6c287e
HKEY_CURRENT_USERWow6432NodeMicrosoftInternet ExplorerLow RightsElevationPolicya2b4da91-a53c-4a84-b486-40080de13a9b
HKEY_CURRENT_USERWow6432NodeMicrosoftInternet ExplorerLow RightsElevationPolicy89b7ae32-9c52-41d6-a64d-14d7bdec9c58
HKEY_CURRENT_USERWow6432NodeMicrosoftInternet ExplorerLow RightsElevationPolicy32a63172-5bcc-4d7e-9fe8-072eee6c287e
HKEY_CURRENT_USERWow6432NodeMicrosoftInternet ExplorerLow RightsElevationPolicy1856a7bd-de8c-488b-aa7a-5682d13166fc
HKEY_CURRENT_USERWow6432NodeMicrosoftInternet ExplorerLow RightsElevationPolicy164ea1fc-b0a0-4202-8c65-e4ba4d54a3ae
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionExtStatsF653D037-97FA-4755-98C1-7F382EEB59A7
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionExtStatsCC53BD19-7B23-43B0-AB7C-0E06C708CCED
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionExtSettingsCC53BD19-7B23-43B0-AB7C-0E06C708CCED
HKEY_CURRENT_USERMicrosoftWindowsCurrentVersionExtSettings02D1BA6-4766-4D7D-82B8-F49439C66F97
HKEY_CURRENT_USERWow6432NodeMicrosoftInternet ExplorerSearchScopes8c9ef753-beb6-4582-b653-93ac59274437
HKEY_CURRENT_USERMicrosoftInternet ExplorerSearchScopes8c9ef753-beb6-4582-b653-93ac59274437
HKEY_CURRENT_USERMicrosoftInternet ExplorerDOMStoragebringmesports.com
HKEY_CURRENT_USERMicrosoftInternet ExplorerDOMStoragebringmesports.dl.tb.ask.com
HKEY_CURRENT_USERBringMeSports
HKEY_CURRENT_USERMicrosoftInternet ExplorerDOMStoragebringmesports.dl.myway.com
HKEY_LOCAL_MACHINEHKEY_CURRENT_USER[APPLICATION]MicrosoftWindowsCurrentVersionUninstall..Uninstaller
BringMeSports_1cbar Uninstall Internet Explorer
BringMeSports_1cbar Uninstall Firefox
BringMeSportsTooltab Uninstall Internet Explorer




 If you consider yourself a power user or you value your privacy then firefox is the browser for you. It is open source and is packed with great features like reporting when your email has been used for a known data breach, it stops annoying pop-up notifications, stops browser fingerprinting, and many more. Firefox is also a cross-platform browser making it a great choice if you want to transfer and use your data across multiple devices with one account. The downside of firefox however is its speed, this browser is the slowest on this list, I guess features and advantages took their tool in the speed department, but if that is not a concern for you and you feel like the positives outweigh some slower speed, grab it
If you consider yourself a power user or you value your privacy then firefox is the browser for you. It is open source and is packed with great features like reporting when your email has been used for a known data breach, it stops annoying pop-up notifications, stops browser fingerprinting, and many more. Firefox is also a cross-platform browser making it a great choice if you want to transfer and use your data across multiple devices with one account. The downside of firefox however is its speed, this browser is the slowest on this list, I guess features and advantages took their tool in the speed department, but if that is not a concern for you and you feel like the positives outweigh some slower speed, grab it  Chrome browser has been a game-changer when it was released and even today some of its features are still great and needed. It is packed with some great features like tab freezing, for example, it is cross-platform meaning that also as firefox you can change data between browsers on different devices. it is a very expandable browser with tons of extensions and its speed performance is very very good. The downside of Chrome are two things sadly, one of them is its hunger for RAM, the browser takes a big chunk of RAM once it is active and on some older computer with limited RAM it performs slowly, another is telemetry which its sending, in other words, other browsers don’t come with the lingering fear that Google’s just a little bit too involved in all of our lives. But if downsides do not trouble you and you have a decent amount of RAM in your system chrome might be the best solution for you, grab it
Chrome browser has been a game-changer when it was released and even today some of its features are still great and needed. It is packed with some great features like tab freezing, for example, it is cross-platform meaning that also as firefox you can change data between browsers on different devices. it is a very expandable browser with tons of extensions and its speed performance is very very good. The downside of Chrome are two things sadly, one of them is its hunger for RAM, the browser takes a big chunk of RAM once it is active and on some older computer with limited RAM it performs slowly, another is telemetry which its sending, in other words, other browsers don’t come with the lingering fear that Google’s just a little bit too involved in all of our lives. But if downsides do not trouble you and you have a decent amount of RAM in your system chrome might be the best solution for you, grab it  Or should I say Microsoft edge 2.0 since this new Edge is completely recoded and rethought, a completely new browser based on chromium. The first version of the edge was an inhouse attempt from Microsoft and it was a disaster, I guess the lesson was learned, and this new edge we have today is a great Browser, it is lightning fast and packed with some great features with one among them standing out I just love, that is the ability to save web pages as applications and truth to be told you have to try this in order to see al great advantages it offers. A very interesting feature is that edge itself wins the speed race from all of the 5 contestants here which is a great surprise. Of course, the downside of annoying Microsoft pushing it to be your default is, well it's Microsoft, as chrome is tied to Google so is edge tied to Microsoft, and the same dreaded feeling that big MS is watching you. If however, you do not concern yourself with these kinds of things, since it is already part of Windows 10, give it a spin and try it, I am sure you will at least love its blazing speed.
Or should I say Microsoft edge 2.0 since this new Edge is completely recoded and rethought, a completely new browser based on chromium. The first version of the edge was an inhouse attempt from Microsoft and it was a disaster, I guess the lesson was learned, and this new edge we have today is a great Browser, it is lightning fast and packed with some great features with one among them standing out I just love, that is the ability to save web pages as applications and truth to be told you have to try this in order to see al great advantages it offers. A very interesting feature is that edge itself wins the speed race from all of the 5 contestants here which is a great surprise. Of course, the downside of annoying Microsoft pushing it to be your default is, well it's Microsoft, as chrome is tied to Google so is edge tied to Microsoft, and the same dreaded feeling that big MS is watching you. If however, you do not concern yourself with these kinds of things, since it is already part of Windows 10, give it a spin and try it, I am sure you will at least love its blazing speed. A new kid on the block, relatively unknown Browser Vivaldi offers some great customizable features no other one on this list offers, a very unique and down to each detail customization option, you can literally tweak each and every aspect of this browser making it best customizable and personal browser ever. How it is also based o chromium, every chrome extension works in it naturally. It is very good in speed and constantly updated and developed. The downside, well if you are anything like me, you could spend ages trying to customize it, ages, it has tons of features, and making it really feel and tick as you want can consume a really lot of time. If this thing does not bother you at all, grab Vivaldi
A new kid on the block, relatively unknown Browser Vivaldi offers some great customizable features no other one on this list offers, a very unique and down to each detail customization option, you can literally tweak each and every aspect of this browser making it best customizable and personal browser ever. How it is also based o chromium, every chrome extension works in it naturally. It is very good in speed and constantly updated and developed. The downside, well if you are anything like me, you could spend ages trying to customize it, ages, it has tons of features, and making it really feel and tick as you want can consume a really lot of time. If this thing does not bother you at all, grab Vivaldi  Last but not least, we have another relic of the old browser age, the Opera browser. Packed with great security and great in-house features like a built-in VPN, built-in ad blocker, built-in crypto wallet, etc this browser seems like a swiss army knife. Opera is full of features and it shows once you start using it. The downside of opera is that its look and feel are specifically tailored to a certain type of user and not everyone will find that appealing or attractive, add some great but hidden and hard to come by features and it may go unnoticed. However, I think you should really give it a go since it definitely deserves more attention than it gets. Grab it
Last but not least, we have another relic of the old browser age, the Opera browser. Packed with great security and great in-house features like a built-in VPN, built-in ad blocker, built-in crypto wallet, etc this browser seems like a swiss army knife. Opera is full of features and it shows once you start using it. The downside of opera is that its look and feel are specifically tailored to a certain type of user and not everyone will find that appealing or attractive, add some great but hidden and hard to come by features and it may go unnoticed. However, I think you should really give it a go since it definitely deserves more attention than it gets. Grab it