One of the selling points of Windows 11 was the ability to run Android apps natively in it without the need for any third-party software. It is not a big surprise that even after its release Microsoft is evolving and expanding Windows 11 and its features.
Microsoft is now rolling out an update for the Windows Subsystem for Android on the Dev Channel of the Windows Insiders program. The new version upgrades the core operating system from Android 11 to Android 12.1 (also known as Android 12L), which means the new system and app features in Android 12 and 12.1 are now available on Windows for the first time. However, not the new features in those updates apply to the modified version that runs on top of Windows. For example, one of the main improvements in 12.1 was a dual-pane notification panel for larger screens, but Android app notifications on Windows just show up in the Windows notification panel.
The upgrade also improves how Android apps integrate into Windows. The Windows taskbar will now show which Android apps are currently using the microphone, location, and other system services — similar to many native Windows applications. Toasts messages (the small popups that some apps use for temporary messages) are now displayed as Windows notifications, and the titlebar on Android apps will use the current activity name for the title.
Full changelog
- Windows Subsystem for Android updated to Android 12.1
- Advanced networking on by default for newer x64 Windows builds
- Updated Windows Subsystem for Android Settings app: redesigned UX and diagnostics data viewer added
- Simpleperf CPU profiler recording now works with Windows Subsystem for Android
- Windows taskbar now shows which Android apps are using microphone and location
- Improvements to Android app notifications appearing as Windows notifications
- Reduced flicker when apps are restored from minimized state
- Apps are not restarted when devices come out of connected standby on recent Windows builds
- New video hardware decoding (VP8 and VP9)
- Fixes for on-screen keyboard in apps
- Fixes for full-screen Android apps and auto-hidden Windows taskbar
- Windows Subsystem for Android updated with Chromium WebView 100
- Added support for Android NetworkLocationProvider in addition to GpsLocationProvider
- Improved general stability, performance, and reliability
The new update is limited to Windows Insiders for now, but once Microsoft fixes all the bugs, it should start rolling out to everyone on Windows 11 that has the Android Subsystem enabled.

 Skinning of applications is not new to PC users, but did you knew you could skin Steam?
With skin, you can customize the UI and style of the client to what you want making it more personal and to your liking. First thing is to find the skin that you would like to install. There are a lot of sites where you could find custom made Steam skins but we would recommend
Skinning of applications is not new to PC users, but did you knew you could skin Steam?
With skin, you can customize the UI and style of the client to what you want making it more personal and to your liking. First thing is to find the skin that you would like to install. There are a lot of sites where you could find custom made Steam skins but we would recommend 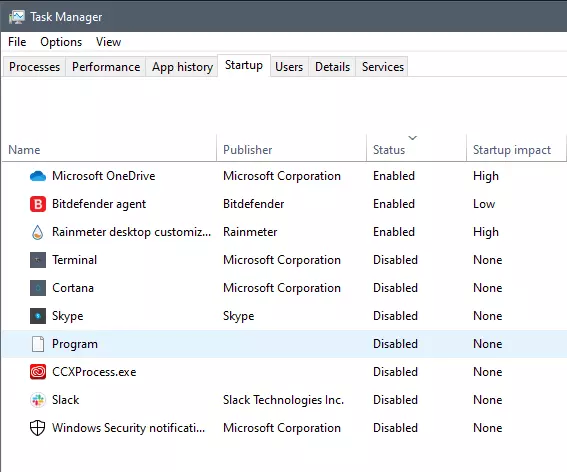
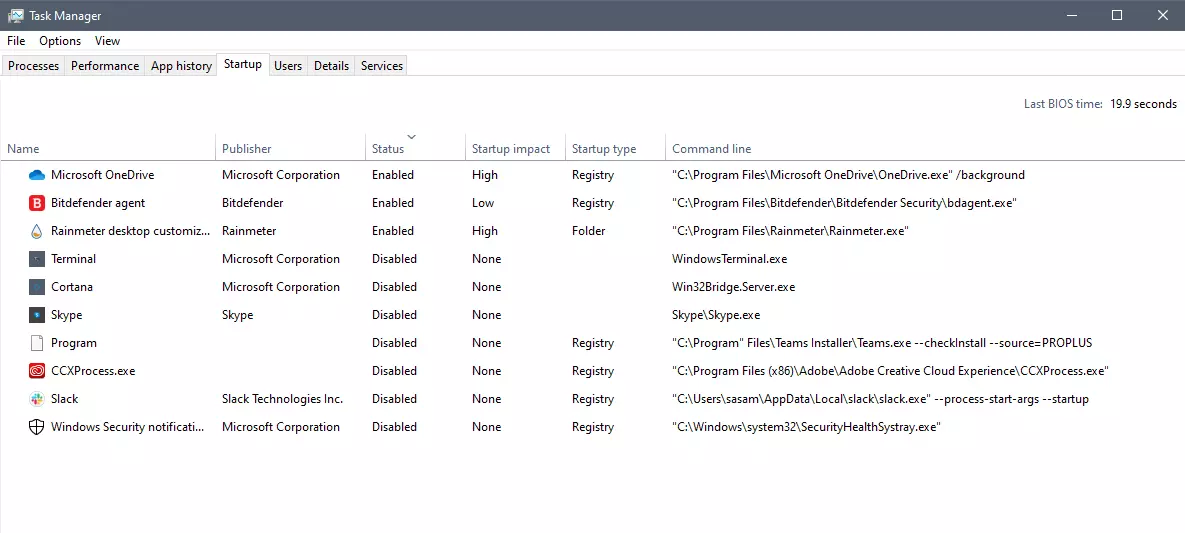

 That being said, now when services are back we stopped and reflected on the platform itself and on its users. If Facebook is vulnerable so are its users, but sometimes users themselves are responsible for being a target. We step back and take a look at posts that manifest on Facebook and have come with some advice on what things you should never post on Facebook and on other social platforms.
That being said, now when services are back we stopped and reflected on the platform itself and on its users. If Facebook is vulnerable so are its users, but sometimes users themselves are responsible for being a target. We step back and take a look at posts that manifest on Facebook and have come with some advice on what things you should never post on Facebook and on other social platforms.
