EverydayLookup is a browser extension for Google Chrome developed by Mindspark Inc. This extension allows users to find what mobile network a certain number belongs to, to find out an area code of a country/town, or locate a town by zip code. While these features look promising and interesting, this extension comes with a downside.
When installed, this extension will change your default search engine, the home page, and new tab to search from MyWay.com, it will monitor user browsing activity, log searches, visited links, opened websites, and other information. This information is forwarded to Mindspark ad servers, then later sold/used to better target ads.
While browsing the internet with this extension you will see additional injected ads and sponsored content throughout your browsing sessions (even if the ads do not match your search queries). It can inject banners to websites, and sometimes even put an ad above website content making it extremely annoying to deal with.
Browser hijacking means that a malicious code has taken power over and modified the settings of your web browser, without your permission. Browser hijackers are capable of doing many different things on your computer. Typically, browser hijacking is used for earning ad revenue that comes from forced advert mouse clicks and site visits. Even though it might seem naive, all browser hijackers are damaging and thus always classified as security threats. Browser hijackers can also permit other destructive programs without your knowledge to further damage the computer.
How one can determine if your browser is hijacked
Signs that a browser is a hi-jacked include:
1. your home page is reset to some unknown webpage
2. new bookmarks pointing to pornographic websites have been added to your favorite pages
3. the essential web browser settings are modified and unwanted or unsafe resources are added to the trusted sites list
4. find new toolbars that you simply did not add
5. you find lots of pop-ups on your screen
6. your web browser starts running slowly or presents frequent errors
7. Inability to navigate to certain websites, particularly antivirus and other security software webpages.
Browser hijackers can get into a computer in some way or other, for instance via file sharing, downloads, and e-mail too. Many web browser hijackings come from add-on programs, i.e., browser helper objects (BHO), toolbars, or extensions added to browsers to give them additional features. Sometimes you may have mistakenly accepted a browser hijacker as part of a software bundle (generally freeware or shareware). A good example of some well-known browser hijackers includes Conduit, Anyprotect, Babylon, DefaultTab, SweetPage, Delta Search, and RocketTab, but the names are continually changing.
Browser hijackers can record user keystrokes to gather potentially invaluable information leading to privacy concerns, cause instability on computers, severely disrupt user’s browsing experience, and eventually slow down the computer to a stage where it becomes unusable.
Certain browser hijacking could be simply stopped by discovering and removing the corresponding malware application through your control panel. Many times, it could be a tough job to find and delete the malicious program because the associated file will be running as part of the operating system process. Moreover, manual removal requires you to perform many time-consuming and tricky procedures that are very hard to conduct for new computer users.
Industry experts always suggest users eliminate any malware including browser hijacker by using an automatic removal tool, which is easier, safer, and faster than the manual removal solution. If you’d like to eliminate persistent hijackers effectively, install the award-winning anti-malware software Safebytes Anti-Malware. And employ a system optimizer, such as Total System Care, to erase all related files from the registry and fix browser issues.
Practically all malware is inherently harmful, but certain types of malware do a lot more damage to your computer than others. Some malware types modify browser settings by adding a proxy server or modify the computer’s DNS configuration settings. In such cases, you will be unable to visit some or all sites, and thus unable to download or install the required security software to remove the infection. So what to do if malicious software prevents you from downloading or installing Anti-Malware? There are some fixes you could try to get around with this problem.
In the event the malware is set to load at Windows startup, then booting in safe mode should avoid it. Since only the bare minimum applications and services launch in “Safe Mode”, there are rarely any reasons for issues to take place. To start your Windows XP, Vista, or 7 computers in Safe Mode with Networking, do as instructed below.
1) At power on, press the F8 key while the Windows splash screen starts to load. This will conjure up the Advanced Boot Options menu.
2) Choose Safe Mode with Networking with arrow keys and hit Enter.
3) Once you get into this mode, you should have an internet connection once again. Now, utilize your browser to download and install Safebytes Anti-malware.
4) After installation, run a full scan and let the program delete the threats it discovers.
Malicious program code may exploit vulnerabilities on a specific browser and block access to all anti-malware software sites. In the event you suspect that your Internet Explorer has been hijacked by a computer virus or otherwise compromised by online hackers, the ideal approach would be to switch to a different internet browser like Mozilla Firefox, Google Chrome, or Apple Safari to download your chosen security software – Safebytes Anti-Malware.
Another way is to download and transfer anti-malware software from a clean PC to run a scan on the affected computer. Abide by these steps to run the anti-malware on the infected computer.
1) On a clean computer, install Safebytes Anti-Malware.
2) Insert the USB drive into the uninfected computer.
3) Double-click the executable file to open the installation wizard.
4) Pick the USB drive as the location when the wizard asks you exactly where you want to install the application. Follow the directions to complete the installation process.
5) Now, transfer the pen drive to the infected PC.
6) Double-click the EXE file to open the Safebytes software right from the pen drive.
7) Hit the “Scan Now” button to start the virus scan.
Today an anti-malware tool can protect your computer or laptop from different types of internet threats. But how to choose the right one amongst various malware protection application that’s available on the market? Perhaps you might be aware, there are numerous anti-malware companies and tools for you to consider. A few are well worth your money, but most aren’t. You need to be careful not to select the wrong application, particularly if you purchase a premium program. One of the highly recommended tools by industry leaders is SafeBytes Anti-Malware, the most dependable program for Windows computers.
SafeBytes anti-malware is a trustworthy tool that not only secures your computer permanently but is also quite easy to use for people of all ability levels. This program can easily identify, remove, and protect your personal computer from the latest malware attacks such as spyware, adware, trojan horses, ransomware, PUPs, worms, parasites along other potentially harmful software programs.
Anti-Malware Protection: Using its advanced and sophisticated algorithm, this malware elimination tool can detect and eliminate the malware threats hiding in your computer system effectively.
Active Protection: SafeBytes provides round-the-clock protection for your computer limiting malware attacks instantly. This software will constantly keep track of your computer for suspicious activity and updates itself continuously to keep current with the latest threats.
Web Protection: Through its unique safety rating, SafeBytes alerts you whether a website is safe or not to access it. This will assure that you’re always certain of your online safety when browsing the internet.
High-Speed Malware Scanning Engine: SafeBytes’s high-speed malware scanning engine lessens scan times and extends battery life. At the same time, it’ll effectively find and eradicate infected computer files or any internet threat.
Low Memory/CPU Usage: SafeBytes is renowned for its minimal influence on computer resources and great detection rate of diverse threats. It runs quietly and efficiently in the background so you’re free to use your computer or laptop at full power all of the time.
Premium Support: For any technical inquiries or product guidance, you can obtain 24/7 professional assistance via chat and e-mail.
To conclude, SafeBytes Anti-Malware is really great for securing your computer against all sorts of malware threats. Malware trouble will become a thing of the past once you put this software program to use. If you’re looking for the very best malware removal application out there, and when you don’t mind shelling out some dollars for it, go for SafeBytes Anti-Malware.
If you’d like to manually get rid of EverydayLookup without using an automated tool, it might be possible to do so by removing the application from the Microsoft Windows Add/Remove Programs menu, or in cases of browser plug-ins, going to the browsers AddOn/Extension manager and uninstalling it. You will likely also want to reset your internet browser.
To be certain of complete removal, find the following registry entries on your computer and delete them or reset the values appropriately. However, this is a complicated task and only computer experts can perform it safely. Furthermore, certain malware is capable of replicating or preventing removal. It is recommended that you carry out the removal procedure in Windows Safe Mode.
Files:
%LOCALAPPDATA%\EverydayLookup_d9
%UserProfile%\Local Settings\Application Data\EverydayLookup_d9
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\fpeepicldbpmefboahpolegllmiglnai
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Extensions\fpeepicldbpmefboahpolegllmiglnai
%PROGRAMFILES%\EverydayLookup_d9
%PROGRAMFILES(x86)%\EverydayLookup_d9
%UserProfile%\Local Settings\Application Data\EverydayLookupTooltab
Registry:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\EverydayLookup_d9Service
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run, value: EverydayLookup EPM Support
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run, value: EverydayLookup EPM Support
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Toolbar, value: 0a7d3c2c-131d-4b0a-9c1b-2045f6bae42a
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Toolbar, value: 0a7d3c2c-131d-4b0a-9c1b-2045f6bae42a
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\SearchScopes\3eb9a50f-f2ab-4d63-8e33-96d71f659640
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\SearchScopes\3eb9a50f-f2ab-4d63-8e33-96d71f659640
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Approved Extensions, value: 0A7D3C2C-131D-4B0A-9C1B-2045F6BAE42A
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\EverydayLookup_d9
HKEY_CURRENT_USER\Software\EverydayLookup_d9
HKEY_CURRENT_USER\Software\AppDataLow\Software\EverydayLookup_d9
HKEY_CURRENT_USER\Software\EverydayLookup

DEL /F /A <file path with extension>Note: In the given command, “/F” is the force delete command, while “/A” is the command that selects the files with the ready for archiving attribute. Step 4: After that, go to the location where you can find the folder you want to delete by using the “cd” command again. And then execute the following command right after:
RD /S <folder path>Note: In the given command, “RD” is the command that removes the folder from the directory, while “/S” removes all of its sub-folders and files. On the other hand, if you also use the “/Q” parameter, you won’t see the “Y/N” confirmation but if you didn’t use it, then simply tap the Y button to proceed.
Error code 0x80240020 is a Windows 10 upgrade error code that affects users who attempt to upgrade their Windows operating system. This may occur due to a particular program that blocks the upgrade from completing. It can also result when other PC issues interfere with the upgrade process by disrupting the ability of Windows Update to download updates on one’s machine. Common symptoms of error code 0x80240020 include the following:
 Error Causes
Error CausesTo correct issues related to error codes, it is often best to apply manual repair methods. These help Windows users determine the root causes of the error code and provide solutions that permanently fix these issues. For instance, if error code 0x80240020 on your machine is due to an issue within the Windows Update tool, you will need to first verify that this is the problem by using a troubleshooter option found within your machine’s settings. The troubleshooter will detect and fix the issue.
Most of these manual repair methods can be implemented by any Windows user, regardless of their background, technical abilities, or lack thereof. However, in certain cases, technical skills are required. If you have trouble implementing the procedures highlighted below or in any other error code article found on this site, consider getting help from a Windows repair technician or use a powerful automated tool.
Below are details regarding the manual repair methods for fixing error code 0x80240020. Ensure you follow the instructions correctly. After all, any error you make will likely cause further problems on your machine and prevent you from resolving error code 0x80240020 in Windows 10.One way to fix error code 0x80240020 is to troubleshoot Windows Update. To do this you will need to access Settings within your machine then simply select the relevant troubleshooting options available. Follow the instructions below:
If there are problems with Windows Update, the troubleshooter will be able to fix them. Once this process is complete, restart your PC and then reopen Windows Update. Attempt to upgrade your Windows operating system. If Windows Update completes the process and your machine downloads and runs the upgrade, you have successfully resolved error code 0x80240020.
If, however, there is another upgrade failure and the message box detailing the presence of error code 0x80240020 in Windows 10 appears, you will need to apply another manual repair procedure. Please see below for further details regarding manual repair method two.Corrupted or missing system files may interfere with your machine’s ability to successfully download an upgrade. For this reason, scan and fix any problems related to system files on your machine using Command Prompt. This manual repair method is often called a System File Check/ Checker (SFC).
To ensure you follow this procedure correctly, enter the command as it is written above, with a space between “sfc” and “/scannow”. Once missing, corrupted or damaged files are present on your machine, the SFC command will enable Command Prompt to scan and fix these issues. Wait until the process is complete then reboot your PC.
With your system successfully rebooted, reattempt the Windows 10 upgrade process in Windows Update or on the Windows Update website. If the issue causing error code 0x80240020 was related to problems with system files, you should be able to complete the upgrade after using the SFC tool.
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise, download and install a powerful automated tool.
There is a lot of software on the market today, but from time to time we discover something extraordinary and unique worth sharing and today we have a threat for you. Ventoy is a tool that will help you with system reinstallations and system maintenance once and for all.
If you are a computer user that has multiple operating systems or you are installing and maintaining different hardware via different OS there is a high chance that you have multiple USB sticks with different operating systems on them.
Now the problem with that is that there are probably too many unlabeled sticks around or you do not have enough so you keep making system USBs depending on which one you might need.
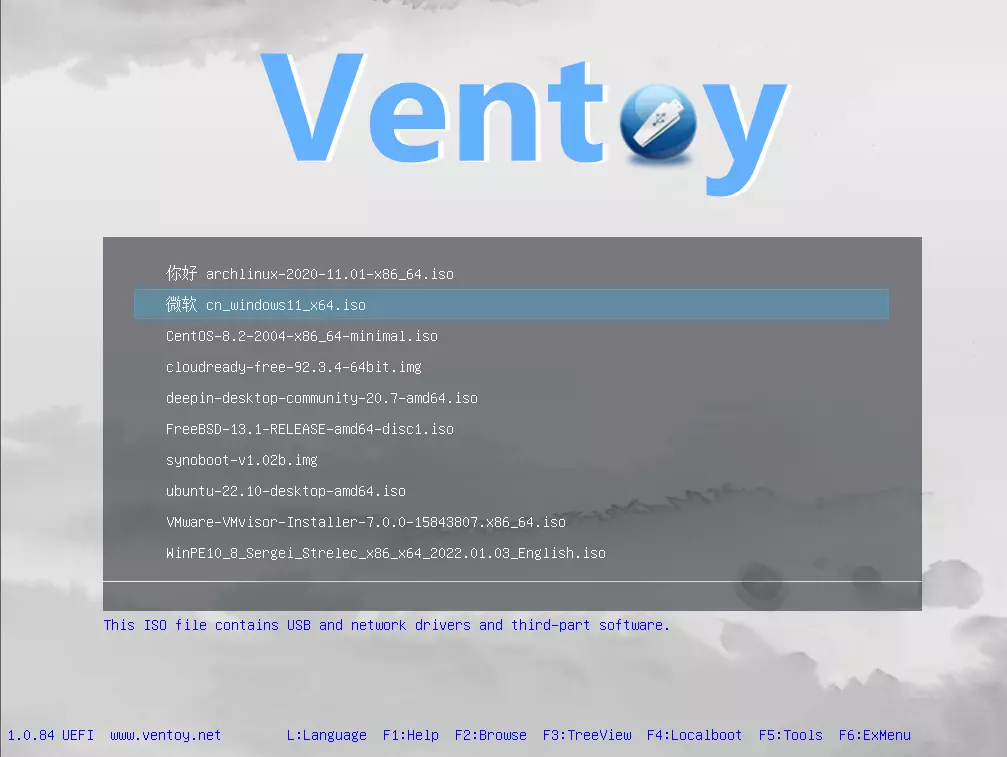
Ventoy solves all of these problems by letting you have as many operating systems images as your USB has capacity. The only thing you need to do is get the software here: https://www.ventoy.net/en/index.html and make a USB with it, then you can freely just copy your ISO images onto the USB and once it is inserted into the computer you will be given a menu to choose which one you would like to start with, simple as that.
“Install applications the easy way and without the hassle, using the Schooldozer downloader. The Schooldozer platform stems from years of experience with installing applications, resulting in a highly optimized process, yielding faster downloads, better user experience, and more successful installations.”In addition, once installed Search.schooldozer.com is installed, it will change the default settings of a browser such as the default search engine, homepage, and new tab page. This is why security experts regard this browser extension as a browser hijacker and a potentially unwanted program. The modification of the browser's settings allows it to control users’ browsing by redirecting them to sponsored sites as well as deliver sponsored content from its affiliated sites in order to gain profit via pay-per-click marketing. And if you think that the ads it displays are harmless, think again for some of these ads can redirect you to suspicious websites that might contain harmful content. What’s more is that this browser hijacker can also keep track and monitor all your browsing activities in order to obtain your browsing data like search queries, what sites you always visit, browsing history, browser type, OS version, and so on. The information collected is then used and may even be shared with its affiliated third parties to deliver more customized and personalized advertisements.