Software Updater is an ad-supported browser extension hijacker that claims to update your PC programs and drivers. In addition to managing the installation of your selected software, this install manager will make recommendations for additional free software that you may be interested in. Additional software may include toolbars, browser add-ons, game applications, anti-virus applications, and other types of applications. The hijacked homepage, softwareupdater.com, did not have valid legal privacy and disclaimer policies on its website as of publication date.
This software adds a Windows Task Scheduler in order to launch the program at various times, including system startup. The software has access to all installed applications on your PC and can install bundled products with unwanted malware. It is also commonly distributed in bundles with unwanted software. Several anti-virus programs have classified this software as malware and are therefore not recommended.
About Browser Hijackers
Browser hijacking means that a malicious code has control over and modified the settings of your internet browser, without your consent. They’re made to interfere with browser programs for several purposes. The idea is to force users to visit specific sites that are trying to increase their visitor traffic and produce higher ad revenue. It may appear harmless, but most of these sites are not legitimate and could present a severe threat to your online safety. Browser hijackers can even allow other malicious programs without your knowledge to further damage your computer.
How to determine if your web browser is hijacked
The common symptoms that indicate having this malicious software on your computer are:
1. home page is changed
2. you find new unwanted bookmarks or favorites added, typically directed to advertisement-filled or pornography websites
3. the default search engine has been changed and your browser security settings have been lowered without your knowledge
4. you find unwanted new toolbars added
5. you may find many pop-up ads on your computer screen
6. your internet browser has become unstable or starts running sluggishly
7. you can’t go to specific websites such as home pages of anti-malware software.
Exactly how browser hijacker infects computers
Browser hijackers infect PCs in numerous ways, including via a drive-by download, a file-share, or an infected email. Many web browser hijackings come from add-on software, i.e., browser helper objects (BHO), toolbars, or extensions added to web browsers to provide them additional functionality. Also, certain freeware and shareware can put the hijacker in your PC through the “bundling” technique. Some of the well-known hijackers are SoftwareUpdater, Conduit Search, Babylon Toolbar, OneWebSearch, Sweet Page, and CoolWebSearch.
Browser hijackers may record user keystrokes to collect potentially valuable information leading to privacy issues, cause instability on systems, drastically disrupt user’s browsing experience, and eventually slow down the computer to a point where it will become unusable.
Browser Hijacker Malware – Removal
Certain hijackers could be removed by just uninstalling the related free software or add-ons through the Add or Remove Programs in the Windows Control Panel. In some cases, it can be a tough task to identify and get rid of the malicious piece because the associated file could be running as part of the operating system process. Besides, browser hijackers might modify the Computer registry so it can be extremely tough to fix manually, especially when you are not a very tech-savvy person.
How To Get Rid Of Malware That Is Preventing Anti-Malware Installation?
Malware can cause many different types of damage to PCs, networks, and data. Some malware is meant to restrict or prevent things that you want to do on your computer system. It may not permit you to download anything from the net or stop you from accessing some or all of the internet sites, especially the anti-virus websites. If you’re reading this now, you’ve perhaps recognized that a malware infection is a reason for your blocked internet traffic. So how to proceed if you need to install an anti-virus software like Safebytes? Even though this type of problem can be difficult to circumvent, there are a few actions you can take.
Install the anti-virus in Safe Mode
In Safe Mode, you can change Windows settings, un-install or install some software, and eliminate hard-to-delete viruses and malware. In the event, the virus is set to load immediately when PC boots, shifting into this particular mode can prevent it from doing so. To start the computer into Safe Mode, hit the “F8” key on your keyboard right before the Windows boot screen comes up; Or after normal Windows boot up, run MSCONFIG, check “Safe Boot” under Boot tab, and click Apply. As soon as you restart into Safe Mode with Networking, you could download, install, as well as update the anti-malware program from there. At this point, you could run the antivirus scan to remove viruses and malware without hindrance from another malicious application.
Switch to an alternate browser
Some malware only targets certain internet browsers. If this sounds like your situation, utilize another browser as it might circumvent the virus. The best solution to avoid this problem is to select a web browser that is well known for its security measures. Firefox contains built-in Malware and Phishing Protection to help keep you secure online.
Install and run anti-malware from your flash drive
To effectively remove the malware, you might want to approach the issue of running anti-virus software on the affected computer system from a different perspective. Adopt these measures to run the antivirus on the affected PC.
1) Download the anti-malware program on a virus-free PC.
2) Mount the USB drive onto the same computer.
3) Run the setup program by double-clicking the executable file of the downloaded application, which has a .exe file extension.
4) Pick a thumb drive as the place when the wizard asks you exactly where you want to install the program. Follow the on-screen instructions to complete the installation.
5) Disconnect the pen drive. You can now use this portable anti-malware on the infected computer.
6) Double-click the anti-malware program EXE file on the flash drive.
7) Run Full System Scan to detect and get rid of all types of malware.
Features of SafeBytes Anti-Malware
Want to install the best anti-malware software for your computer system? You can find many applications available that come in paid and free versions for Windows systems. Some of them do a great job in getting rid of threats while some will affect your PC themselves. You must be careful not to choose the wrong application, especially if you purchase a paid software. Among few good programs, SafeBytes Anti-Malware is the strongly recommended software for the security-conscious individual.
SafeBytes anti-malware is really a powerful, highly effective protection application made to assist users of all levels of IT literacy in identifying and eliminating harmful threats from their computers. Through its cutting-edge technology, this software protects your PC against infections brought on by different types of malware and similar threats, including spyware, adware, computer viruses, worms, trojan horses, keyloggers, ransomware, and potentially unwanted program (PUPs).
SafeBytes possesses a plethora of great features that can help you protect your laptop or computer from malware attack and damage. The following are some of the best ones:
Real-time Active Protection: SafeBytes delivers complete and real-time security for your laptop or computer. They are very efficient in screening and getting rid of different threats because they are constantly revised with new updates and safety measures.
Best AntiMalware Protection: This deep-cleaning anti-malware application goes much deeper than most antivirus tools to clean your personal computer. Its critically acclaimed virus engine finds and disables hard to remove malware that conceals deep inside your computer.
Safe Browsing: SafeBytes gives an instant safety rating about the web pages you’re about to check out, automatically blocking unsafe sites and make sure that you’re certain of your online safety while browsing the net.
Lightweight Tool: SafeBytes is a lightweight and easy-to-use antivirus and antimalware solution. As it uses minimal computer resources, this application leaves the computer’s power exactly where it belongs: with you actually.
Premium Support: You may get absolutely free 24/7 technical support from their computer experts on any product queries or computer security issues.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove SoftwareUpdater without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by SoftwareUpdater

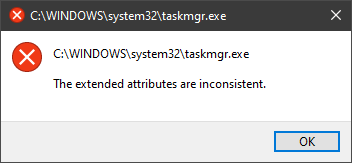 In this guide, we will show you common ways in fixing Extended Attributes are inconsistent errors inside your Windows that are easy to do and less time-consuming than complete reinstallation of the system.
In this guide, we will show you common ways in fixing Extended Attributes are inconsistent errors inside your Windows that are easy to do and less time-consuming than complete reinstallation of the system.
 Windows 11 provides several different ways to make your cursor stand out and be easier to spot inside it. You can make the mouse pointer larger, invert it, or change its color.
Windows 11 provides several different ways to make your cursor stand out and be easier to spot inside it. You can make the mouse pointer larger, invert it, or change its color.


