Error Code 0x8024001b- What is it?
At its most basic level, Error Code 0x8024001b is an error that can cause problems with the installation and updates of software and operating system updates. The most common version of this error appears in Windows 10, but a similar error with a matching code number has been present in previous versions of the operating system, back through Windows 7.
Common symptoms include:
- Programs freezing or locking up during use
- The appearance of an error message regarding installation difficulties
- Computer shutting down or freezing during operation
- Difficulty in running multiple programs at the same time
Solution
 Error Causes
Error Causes
There are two main causes for Error Code 0x8024001b, both of which are fairly simple: Updates needed for the Windows Update tool itself and software that causes Windows Update to fail during installations through conflicts in system files. While these may seem like technical issues, these problems are actually easily resolved with a few simple steps. The average user can use the methods listed below to fix the problems on their own.
Further Information and Manual Repair
For users who want to address Error Code 0x8024001b for themselves, the steps below can be followed to address the two primary causes for the error. If you have difficulty in completing these steps or are not confident in your computing skills and ability to follow the listed steps, contact a Windows repair technician.
Here are the top methods to resolve Error Code 0x8024001b on your own:
Method One: Check for Updates to Windows Update
In some cases, the Windows Update tool may need an update for itself. When you attempt to run updates or install wizards for other software, it can cause conflicts with the Windows Update process, slowing down your computer or causing it to freeze.
If you are attempting to run multiple installations or updates at the same time, it may also cause Error Code 0x8024001b to arise on your computer.
To resolve this issue, close out all programs, with the exception of the Windows Update tool. Within the tool, select “Check for Updates” and install any updates that are needed. When finished, you should restart your computer to ensure that all updates have been fully applied before attempting any other installations or updates.
Method Two: Uninstall Conflicting Software
Another problem that can cause Error Code 0x8024001b is the presence of conflicting software. If Error Code 0x8024001b has only recently appeared on your computer, consider removing any software that has been added to your computer, running the Windows Update process, and restarting your computer before attempting to reinstall the problem software.
With any method that you use, it is important to remember to keep your Windows Updates current at all times. This is the best way to avoid the appearance of Error Code 0x8024001b and similar errors in the future, as stacked up updates are more likely to cause issues and conflicts with your other installed software and operating system.
While there are some tools out there that claim to be able to fix Error Code 0x8024001b for you, it is important to always thoroughly investigate the publisher and distributor of such software, as some of the tools available on the Internet will actually introduce malware and adware on your computer in the name of “protecting” your computer or resolving an error.
If you have tried to use both methods above and have not fully resolved Error Code 0x8024001b, get in touch with someone who is a qualified computer repair professional and is familiar with your particular version of the Windows operating system to assist you in finalizing your resolution.
Method Three: Use An Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise, download and install a powerful automated tool.
 So far I believe each person on this planet has at least heard of Marvel superhero movies, perhaps even watched a few of them, and no wonder. Movies are spawning now over 20 titles and they are not really released as events described in them.
So far I believe each person on this planet has at least heard of Marvel superhero movies, perhaps even watched a few of them, and no wonder. Movies are spawning now over 20 titles and they are not really released as events described in them.
 Option to right-click on the taskbar and launch task manager is gone but do not worry there are other same and simple ways you can launch it.
Option to right-click on the taskbar and launch task manager is gone but do not worry there are other same and simple ways you can launch it.

 In the run box type in Control Panel and press ENTER
In the run box type in Control Panel and press ENTER
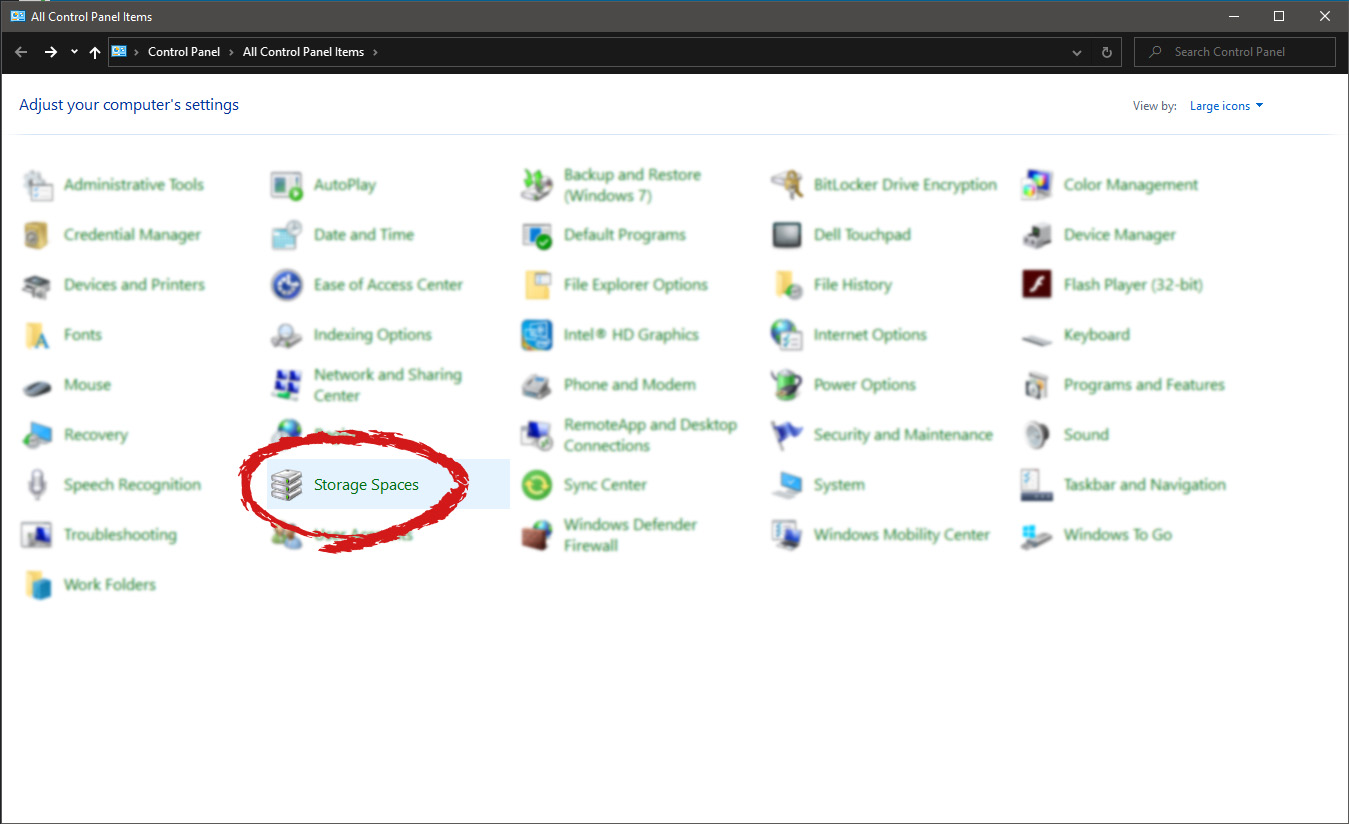
 In Control Panel find Storage Spaces and left-click on it.
In Control Panel find Storage Spaces and left-click on it.
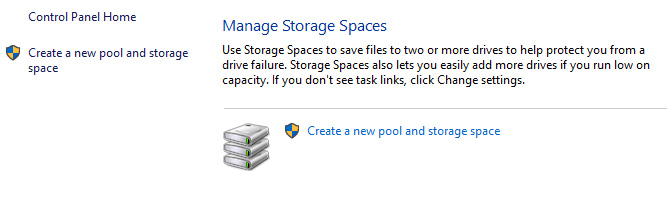
 Once storage spaces open, left-click on Create a new pool and storage space
Once storage spaces open, left-click on Create a new pool and storage space
 Once you click on create new, you will be greeted with a list of hard drives you can use for this operation.
Once you click on create new, you will be greeted with a list of hard drives you can use for this operation.
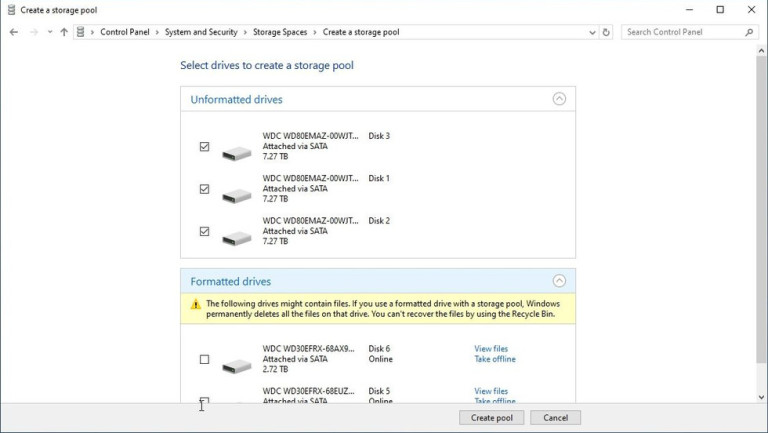 Please note that all hard drives you choose will be completely erased and formatted and then assign a single drive letter. Click on Create pool.
Please note that all hard drives you choose will be completely erased and formatted and then assign a single drive letter. Click on Create pool.
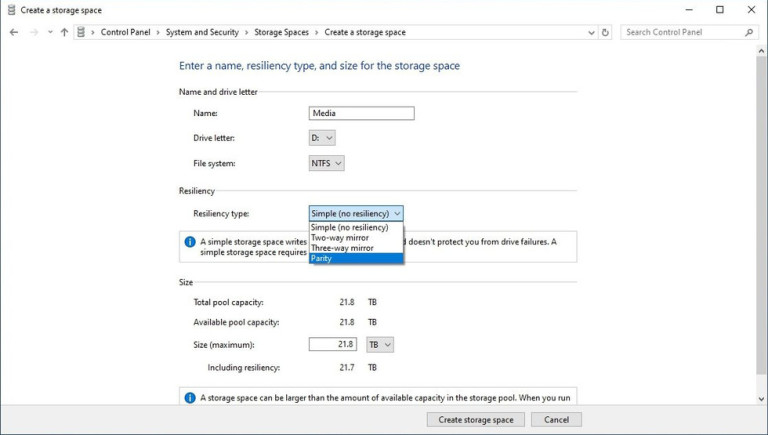 You will find yourself in new storage options where you can assign a drive letter, give storage space a name, etc.
You will find yourself in new storage options where you can assign a drive letter, give storage space a name, etc.
