AtoZManuals is a Browser Extension developed by MindSpark Inc. This extension offers users an easy way to search Customer Manuals for Products. This extension may seem handy at first, however, this extension hijacks your browser home page, and changes your default search engine to MyWay.
While browsing the internet with this extension you will see additional ads, sponsored links, and pop-up ads in your browser. Additionally, this extension monitors your browser activity, including search words, visited links, shopping information, and sometimes even personal information, which is later used to display better-targeted ads.
Multiple anti-virus scanners have marked this extension as a Browser Hijacker, and due to its rogue behavior, it is not recommended to keep it on your computer.
About Browser Hijackers
Browser hijacking means a malicious program code has control over and altered the settings of your browser, without your permission. They’re made to interfere with web browser functions for various reasons. Often, it’ll drive users to predetermined websites that are trying to boost their ad earnings. Although it may seem naive, these tools were created by vicious people who always look to take advantage of you, so that hackers could earn money from your naivety and distraction. When the program attacks your laptop or computer, it begins to mess things up a whole lot that slows your system down to a crawl. In the worst-case scenario, you may be forced to tackle serious malware threats as well.
How one can recognize a browser hijack
There are various signs that indicate the internet browser has been hijacked: your homepage is reset to some unfamiliar website; you observe new unwanted favorites or bookmarks added, typically directed to ad-filled or porn sites; default search engine is changed; you see many toolbars on the browser; your internet browser displays endless pop-up windows; your browser has become unstable or starts running sluggishly; you’re prohibited access to specific web pages, for example, the site of an antivirus software developer like SafeBytes.
How it infects your PC
A browser hijacker could be installed on your PC when you check out an infected website, click on an email attachment, or download something from a file-sharing website. They are generally included with toolbars, add-ons, BHO, plug-ins, or browser extensions. A browser hijacker could also be installed as a part of freeware, shareware, demoware, and fake programs. Examples of popular browser hijackers are Fireball, CoolWebSearch. GoSave, Ask Toolbar, RocketTab, and Babylon Toolbar.
Getting rid of browser hijackers
Some kinds of browser hijackers can be removed from the computer by deleting malicious software or any other recently added freeware. However, many hijackers are much more difficult to discover or remove since they could get themselves connected with some important computer files that enable it to operate as a necessary operating-system process. Furthermore, manual removals demand in-depth system knowledge and thus could be a very difficult task for novice computer users.
Learn How To Install Safebytes Anti-Malware On An Infected Computer system
Malware may cause several kinds of damage to computing devices, networks, and data. Some malware is meant to restrict or block things that you wish to do on your computer system. It may well not allow you to download anything from the web or it will stop you from accessing a few or all internet sites, particularly the anti-virus sites. If you’re reading this right now, you might have perhaps recognized that virus infection is the cause of your blocked internet connectivity. So what to do when you want to download and install anti-malware software like Safebytes? Although this sort of issue will be difficult to get around, there are some actions you can take.
Install the anti-malware in Safe Mode
If any virus is set to load automatically when Microsoft Windows starts, getting into safe mode could block this attempt. Since just the minimum programs and services launch in “Safe Mode”, there are seldom any reasons for conflicts to happen. To start your Windows XP, Vista, or 7 computers in Safe Mode with Networking, follow the instructions below.
1) At power-on/startup, hit the F8 key in 1-second intervals. This would conjure up the Advanced Boot Options menu.
2) Make use of the arrow keys to select Safe Mode with Networking and press ENTER.
3) When you are into this mode, you should have an internet connection once again. Now, make use of your browser to download and install Safebytes Anti-malware.
4) Following installation, run a full scan and let the software program remove the threats it finds.
Obtain the security program in a different browser
Some malware might target vulnerabilities of a particular web browser that obstruct the downloading process. The best way to overcome this issue is to go with an internet browser that is well known for its security measures. Firefox contains built-in Malware and Phishing Protection to keep you secure online.
Install and run antivirus from your USB drive
Here’s another solution which is utilizing a portable USB anti-virus software package that can scan your system for viruses without the need for installation. To run anti-virus from a USB pen drive, follow these simple measures:
1) On a clean computer, download and install Safebytes Anti-Malware.
2) Mount the pen-drive onto the same computer.
3) Double-click the Setup icon of the antivirus software package to run the Installation Wizard.
4) Select the USB flash drive as the location when the wizard asks you exactly where you wish to install the application. Follow activation instructions.
5) Now, transfer the thumb drive to the infected PC.
6) Run the Safebytes Anti-malware directly from the USB drive by double-clicking the icon.
7) Click the “Scan” button to run a full system scan and remove viruses automatically.
How SafeBytes Anti-Malware Keep your Computer Malware Free
These days, an anti-malware tool can protect your computer or laptop from different kinds of internet threats. But exactly how to choose the right one amongst numerous malware protection software that is available in the market? As you might be aware, there are lots of anti-malware companies and tools for you to consider. Some of them are great, some are ok types, while some will affect your computer themselves! You have to select one that is reliable, practical, and has a good reputation for its malware source protection. When it comes to commercial application options, the majority of people go with well-known brands, such as SafeBytes, and are very happy with it.
SafeBytes is a powerful, real-time antivirus application that is made to assist the typical computer user in safeguarding their computer from malicious internet threats. With its outstanding protection system, this utility will instantly detect and remove most of the security threats, including viruses, adware, browser hijackers, ransomware, PUPs, and trojans.
SafeBytes carries a variety of great features that can help you protect your laptop or computer from malware attack and damage. Below are some of the great ones:
Robust Anti-malware Protection: Using its advanced and sophisticated algorithm, this malware elimination tool can find and get rid of the malware threats hiding in the computer system effectively.
Real-time Threat Response: SafeBytes delivers complete and real-time security for your computer system. It’ll inspect your computer for suspicious activity regularly and its unparalleled firewall guards your computer against unauthorized entry by the outside world.
Quick Multithreaded Scanning: This software has one of the fastest and most efficient virus scanning engines in the industry. The scans are very accurate and take a little time to complete.
Web Protection: Through its unique safety ranking, SafeBytes informs you whether a website is safe or not to access. This will ensure that you’re always certain of your online safety when browsing the world wide web.
Light-weight: SafeBytes is a lightweight and simple to use antivirus and antimalware solution. Since it utilizes minimal computer resources, this program leaves the computer’s power exactly where it belongs to: with you actually.
24/7 Online Technical Support: Support service is readily available for 24 x 7 x 365 days through email and chats to answer your queries.
Technical Details and Manual Removal (Advanced Users)
If you’d like to manually get rid of AtoZManuals without the use of an automated tool, it may be possible to do so by deleting the program from the Microsoft Windows Add/Remove Programs menu, or in cases of web browser extensions, going to the browsers AddOn/Extension manager and uninstalling it. You will likely also want to reset your web browser.
Lastly, examine your hard drive for all of the following and clean your Windows registry manually to remove leftover application entries after uninstalls. Please note that only experienced computer users should try to manually edit the system files simply because deleting any single critical registry entry leads to a serious issue or even a system crash. In addition, certain malware is capable of replicating itself or preventing its deletion. Completing this task in Safe Mode is suggested.
Folder:
C:Users%UserName%AppDataLocalTemp
Registry:
HKLMSOFTWAREClassesAppIDAtoZManuals.exe
HKEY_LOCAL_MACHINESOFTWAREMicrosoftInternet ExplorerExtensions
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects
HKEY_LOCAL_MACHINESoftwareMicrosoftInternet ExplorerToolbar
HKEY_LOCAL_MACHINESOFTWAREGoogleChromeExtensions
HKEY_LOCAL_MACHINESOFTWAREMozillaFirefoxExtensions
HKEY_CURRENT_USERSoftwareOpera Software
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionvirus name
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionWinlogon Shell = %AppData%IDP.ARES.Generic.exe
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun Random
HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionRandom
 Error Causes
Error Causes
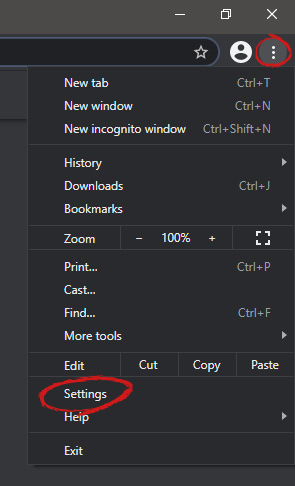 When you are in settings, on the left side move toward the bottom until you run into a tab that says On Startup and click on it. On right, a new section will open, click on Open a specific page or set of pages.
When you are in settings, on the left side move toward the bottom until you run into a tab that says On Startup and click on it. On right, a new section will open, click on Open a specific page or set of pages.
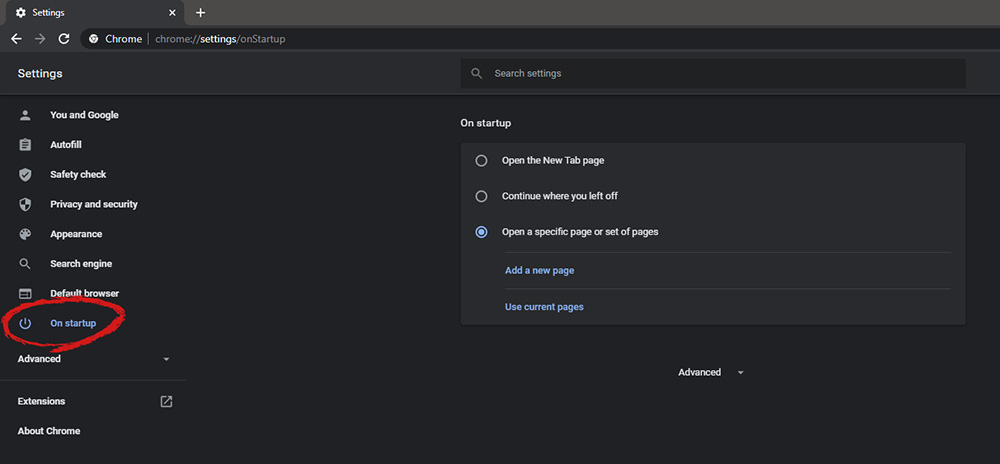 You will be presented with the option to add a new page by typing its URL or getting it from bookmarks or using a specific opened one. You can repeat this process until you have added all pages that you wish to be automatically opened once Chrome is opened for the first time.
You will be presented with the option to add a new page by typing its URL or getting it from bookmarks or using a specific opened one. You can repeat this process until you have added all pages that you wish to be automatically opened once Chrome is opened for the first time.