What is Error 0xe06d7363?
Error 0xe06d7363 is displayed when a process or an operation is not launched, or completed by an application.
This error can prevent the user from performing some operations. It might close the application unconditionally. Sometimes a ‘GetLastError()’, a ‘GetExceptionCode()’, or a ‘GetExceptionInformation()’ is displayed with this error.
Error Causes
Error 0xe06d7363 can occur for a number of reasons. Damaged, corrupted, or missing files in the registry database are the main reasons why the error might occur. Another reason is when the system files are not configured correctly, thus they corrupt system files in applications. They can also affect the hardware devices.
All code-generated exceptions in the Microsoft Visual C + + compiler will contain this error. As this error is compiler-generated, the code will not be listed in Win32 API header files. This code is a cryptic device, with ‘e’ for exception while the final 3 bytes represent ‘msc’ ASCII values.
Further Information and Manual Repair
To resolve this error, you will have to debug an application. While using Microsoft Visual Studio, you can stop the program when the error 0xe06d7363 occurs. To start debugging, follow these steps:
- Start debugging application
- From Debug menu, click on Exceptions
- In the Exceptions window, select error 0xe06d7363
- In Action, Change to Stop always from Stop if not handled
Another fix for this issue is reverting back to an earlier copy or the last update of the same Windows. Error 0xe06d7363 can occur is when you try running a client application using Microsoft.SqlServer.Types.dll component on your computer that has Microsoft SQL Server 2008 Server Pack 2 installed. With the error, the following text can be seen:
“unable to load DLL ‘SqlServerSpatial.dll’ Exception from HRESULT 0xe06d7363".
A Cumulative Update 7 was initially released for SQL Server 2008 Service Pack 2 in order to fix this issue. Since the builds are cumulative, every new fix released contains hotfixes and all security fixes which were also included in the previous SQL Server 2008 fix release. This error can be found in all Microsoft products that are listed in the Applies to Category.
Microsoft SQL Server 2008 hotfixes are created to resolve errors like 0xe06d7363 on specific SQL Server service packs. This error is by design and has commonly occurred in the previous versions of Windows before Windows 7.
Congratulations, you have just fixed Error 0xe06d7363 in Windows 10 all by yourself. If you would like to read more helpful articles and tips about various software and hardware visit errortools.com daily. Now that’s how you fix Error 0xe06d7363 in Windows 10 on a computer. On the other hand, if your computer is going through some system-related issues that have to get fixed, there is a one-click solution known as Restoro you could check out to resolve them. This program is a useful tool that could repair corrupted registries and optimize your PC’s overall performance. Aside from that, it also cleans out your computer for any junk or corrupted files that help you eliminate any unwanted files from your system. This is basically a solution that’s within your grasp with just a click. It’s easy to use as it is user-friendly. For a complete set of instructions in downloading and using it, refer to the steps below Perform a full system scan using Restoro. To do so, follow the instructions below.-
-
- Download and install Restoro from the official site.
- Once the installation process is completed, run Restoro to perform a full system scan.
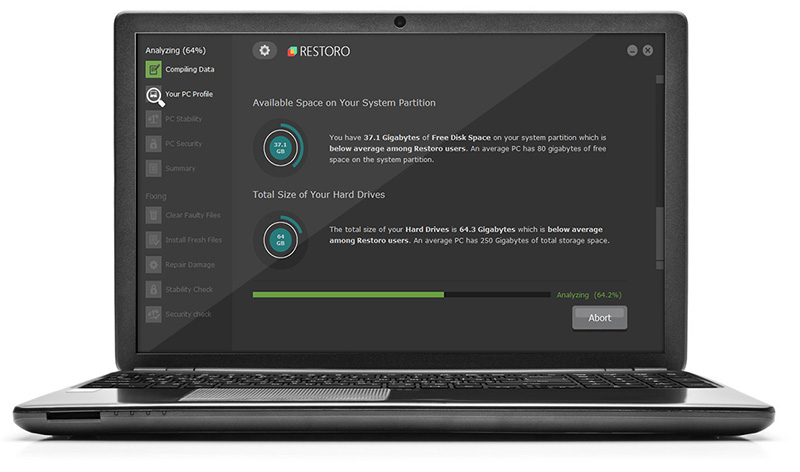
- After the scan is completed click the “Start Repair” button.
-


 Storage management Page update
Storage management Page update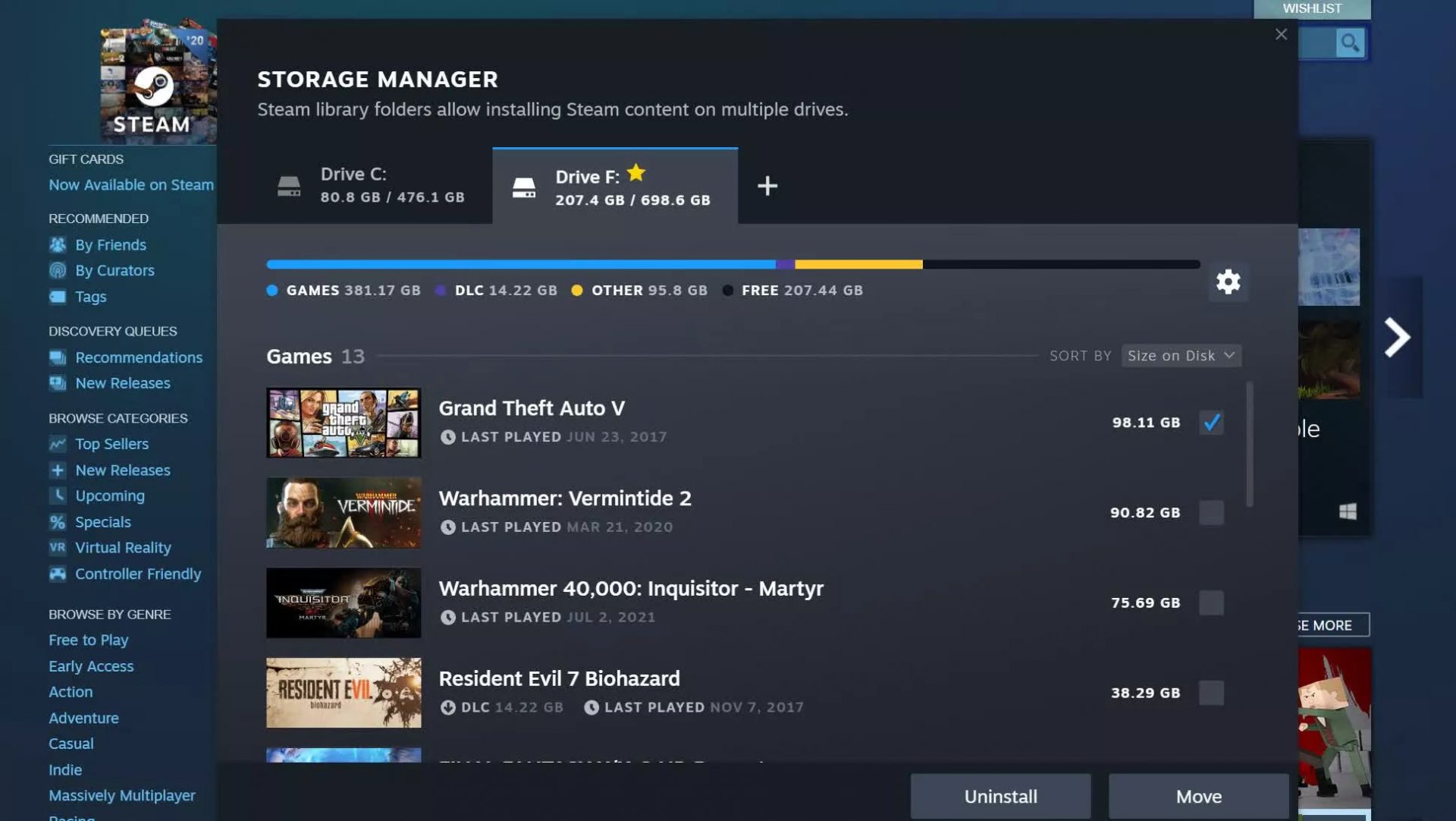 Another thing with the Steam store management page is the ability to move installation files from one location to another. Let’s say that you have two or more hard disk drivers in your machine and that you have SSD that you use for running stuff since it is fast and larger and slower one for storage. Now you can easily and quickly move one installation from one to another in order to take advantage of your faster SSD for quicker LOAD game times without making a new installation.
Another thing with the Steam store management page is the ability to move installation files from one location to another. Let’s say that you have two or more hard disk drivers in your machine and that you have SSD that you use for running stuff since it is fast and larger and slower one for storage. Now you can easily and quickly move one installation from one to another in order to take advantage of your faster SSD for quicker LOAD game times without making a new installation.
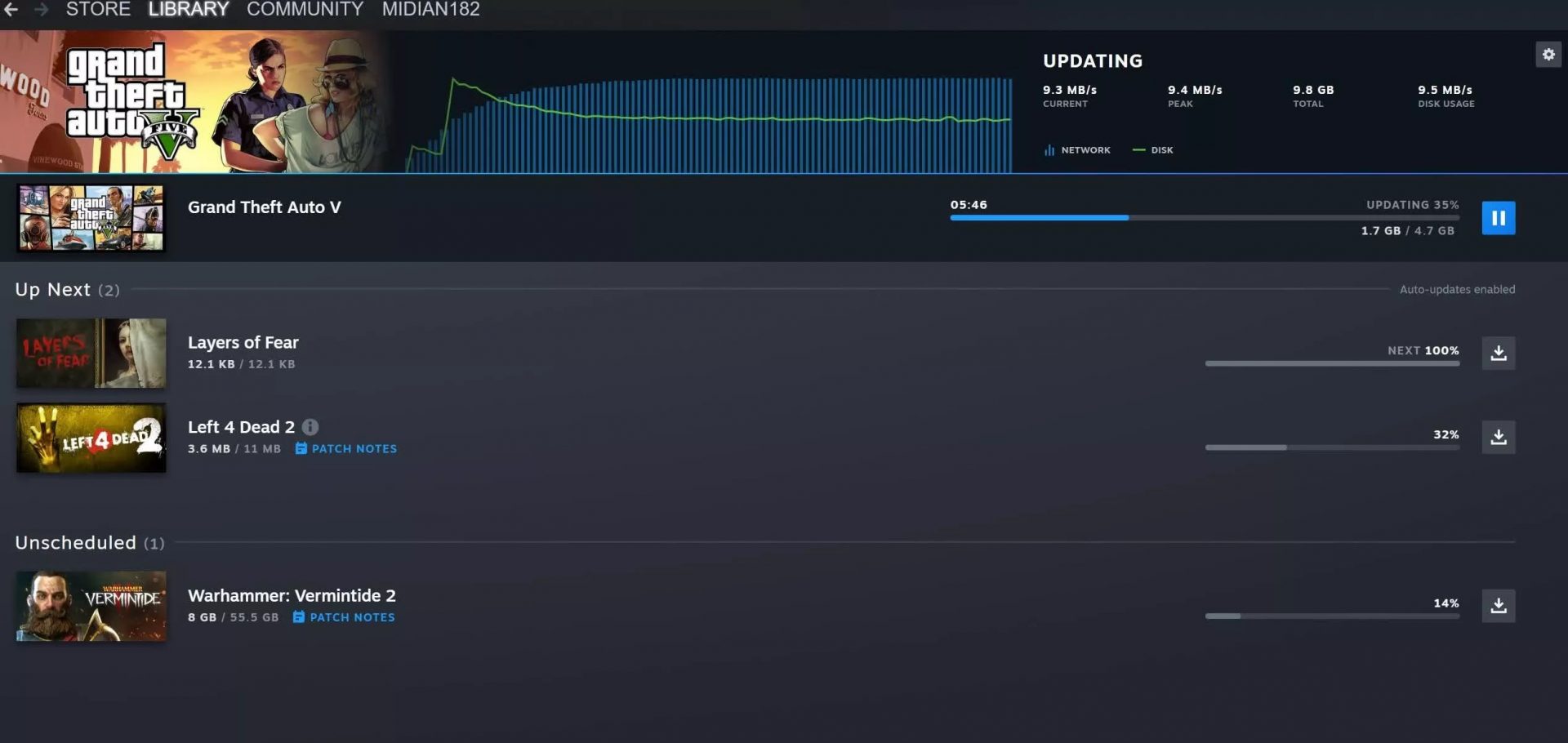 Also, you can now drag and drop items in the download bracket to reorder download orders or place them as active downloads to start downloading right away.
Also, you can now drag and drop items in the download bracket to reorder download orders or place them as active downloads to start downloading right away. 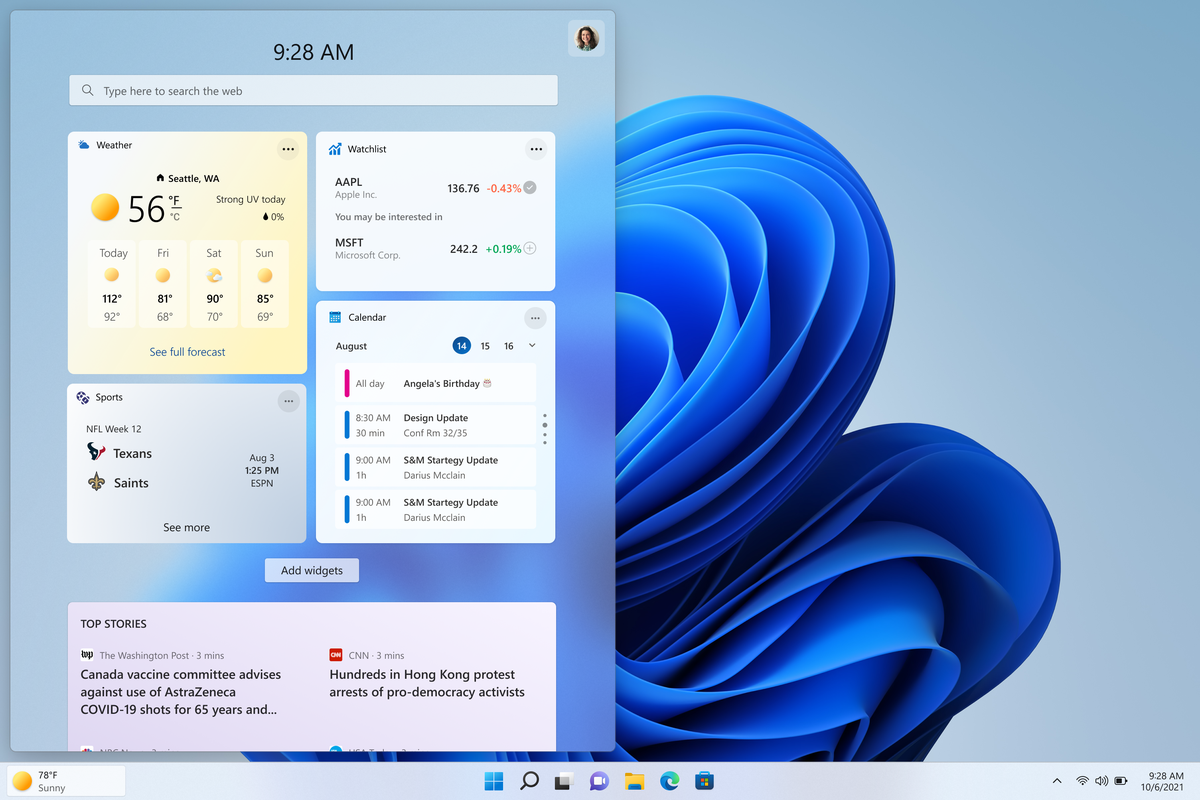 The first step is to right-click anywhere on the taskbar (in empty space) and choose Taskbar settings
Once the taskbar settings are opened, find Widgets and click on the switch on the far right to turn it off, immediately no more information will be shown on the taskbar and it will be free again. And that is all there is to it.
The first step is to right-click anywhere on the taskbar (in empty space) and choose Taskbar settings
Once the taskbar settings are opened, find Widgets and click on the switch on the far right to turn it off, immediately no more information will be shown on the taskbar and it will be free again. And that is all there is to it. 