Started as an internal network and has slowly expanded since 1960 internet has taken over the world. In the beginning, it was a means of information change but in the modern age you can run applications and virtual machines over the internet, you can stream video and audio, and you can communicate in real-time with someone on the other side of Earth.
With the internet growing so fast in such a small amount of time it is only logical and wise to take a step back and take a good look at what it offers now, what are great things about it and what are some of the worst.
Good sides of the internet
Information
There are a lot of advantages of the internet, first and foremost is information. Internet was made as an information exchange service and even today you can find a lot of various information about various topics that interest you. A site like Wikipedia is a completely free online encyclopedia and a lot of news companies have their own internet sites where you can find free information and news.
On the other hand, there are also websites like udemy, edx, Coursera, and many others that will offer you the education, some for free, some for money but you can get a glimpse and part of university quality education for just a fraction of price.
Online shopping
Sites like Amazon have used the internet and launched themselves as today's multi-billion companies. In today's world, there is not a single thing you can not buy online. Many sites today are going from the large online marketplace where you can find everything to small niche specialized ones. Also every major brand in the world today has its own online store.
Other shops will offer you music, movies, games, etc. Services like steam, xbox pass, sony pass etc, will let you buy games online, other music, movies, and many more.
Streaming services
Days, when you had to buy movies in order to watch them at home, are gone, thanks to the internet we have plenty of streaming services for movies and tv shows as well as ones for music. If you do not want to spend money on actually purchasing things then a good idea is to have a streaming plan set up when you want it.
Email and messaging
Communication is a great thing and since the dawn of mankind people have been talking and sharing with each other, the internet has made it possible to send mail electronically and instantly and modern chat communication is everywhere. We can not just talk with our friends and family that can be on the other side of the world, we can also talk in real-time with the sales representative, with technical service, or attend online classes with a group of people.
Cloud storage services
Saving your pictures in this digital media age on the hard drive can be risky but thanks to modern technologies you can save most of your precious files on cloud servers for safekeeping. From pictures to documents and even other files that you need and want to save. There are some of them that will offer you a free amount and some basic free plans as well.
Bad sides of the internet
Malware, viruses, and phishing
We could not talk about the bad side of the internet if we do not mention its greatest threat. Bad sites, infected software, phishing emails, and many more malicious threats. Problem is that these kinds of tricks and attacks have become more and more sophisticated and harder to detect and avoid.
Pornography
Pornography is bad, having it freely available to children is even worse. Sadly the only way to regulate this is on a computer-by-computer basis by turning on parent control on each one. There are many studies that go into detail about why this is bad, sadly currently there are no effective ways to isolate this content.
No privacy
When we say there is no privacy we do not mean by using social media and not setting your privacy settings altho that also fits in this point, what we are talking about is data mining of your habits and things you do. It is well known that today lot of websites are using some form of AI recommender system in order to tailor your internet experience to suit your needs better. Most of these AI systems are trained by mining your data and analyzing your habits.
If you have 2 google accounts there is a high probability chance that for the same query you will get different results, depending on your so far browsing habits. The same goes for other services as well.
Dark webshops
There are some great things in dark and deep WEB-like sites with true news and information. Even some legit libraries where you can find and download rare books. Sadly as goes with the internet dark and deep WEB also has its well, dark sides, from disturbing content to shops that sell stolen items to straight stealing your money by parading as legit shops but only to steal your money.
Dating sites
We all try to find someone that is perfectly matched with us but using the online dating site has many proven bad effects on psychology. It also devaluates interaction between people and can lower self-esteem.
Bad habits
Since the internet has become wildly available and popular on various devices like tablets and mobile phones more and more people are spending an unhealthy amount of time on it. Harvesting the benefits of the internet is great but find some time for other people as well.
 It is not a secret that Windows 11 is the most secure Windows ever created, well at least up until now. It is packed with advanced security features like S-mode, Secure Boot, and Trusted Platform Module (TMP 2.0). All these new security features that Microsoft has advertised made people question are enough for security or do you still need third-party Antivirus software.
In order to get an answer to this question, let us first take a detailed look at what each one of them does, and then we will give you our opinion on a given subject.
It is not a secret that Windows 11 is the most secure Windows ever created, well at least up until now. It is packed with advanced security features like S-mode, Secure Boot, and Trusted Platform Module (TMP 2.0). All these new security features that Microsoft has advertised made people question are enough for security or do you still need third-party Antivirus software.
In order to get an answer to this question, let us first take a detailed look at what each one of them does, and then we will give you our opinion on a given subject.


 When Task Manager opens, click on the startup tab on top.
When Task Manager opens, click on the startup tab on top.
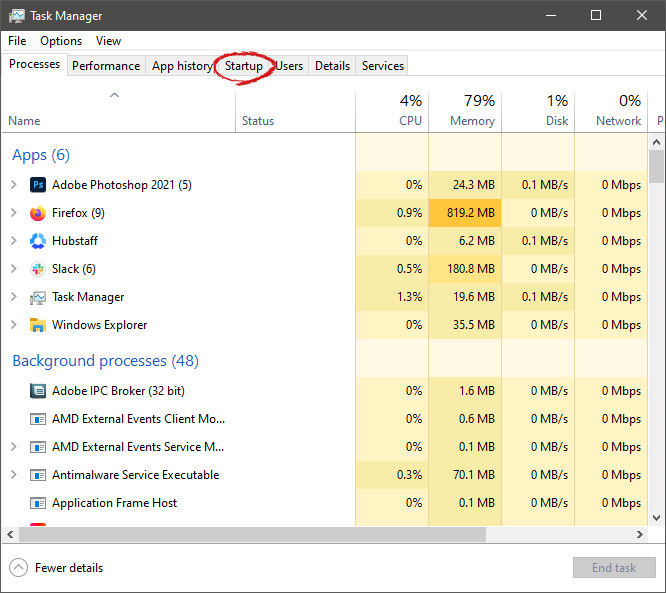 Once you click on startup you will get a list of applications that are set to be started when Windows is booted.
Once you click on startup you will get a list of applications that are set to be started when Windows is booted.
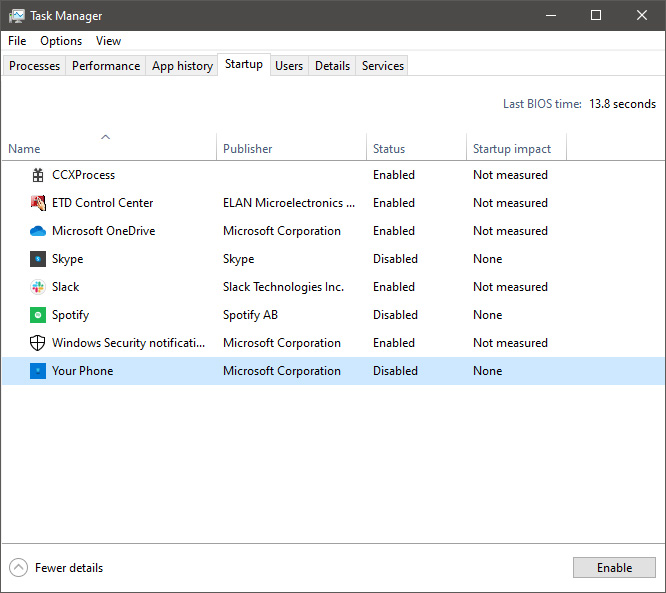 You can now click on the application and then click on disable on the bottom button, the application status will update in task manager to disabled and it will not be booted anymore when Windows starts. In this same manner, you can enable back some applications if you changed your mind about them.
Please note that some applications are using some services and must have them running or they will not work properly. The best practice is to disable applications you are positive you will not use or use rarely so you do not want them to slow down Windows.
You can now click on the application and then click on disable on the bottom button, the application status will update in task manager to disabled and it will not be booted anymore when Windows starts. In this same manner, you can enable back some applications if you changed your mind about them.
Please note that some applications are using some services and must have them running or they will not work properly. The best practice is to disable applications you are positive you will not use or use rarely so you do not want them to slow down Windows. 

