Error Code0x80070426 - What is it?
When Windows evolved into Windows 10, the program known as Windows Security Essentials is no longer. It is now the program known as Windows Defender. When a computer is upgraded from a previous version of Windows up to Windows 10, the Windows Defender takes over and will replace the Security Essentials. In a small percentage of Windows 10 upgrades, something will go wrong and the new program will fail to replace Security Essentials. The result will be that the operating system has both of the programs installed. In this case, Windows Defender will not offer any protection and Security Essentials will not be able to defend either. This error code will also present itself when the Windows Mail App in Windows 10 fail to retrieve and sync email from the user's account.
Common symptoms include:
- There will be an error message that says: “An error has occurred in the program initialization. If this problem does continue, contact your System Admin. Error code 0x80070426.”
- The computer will be left completely vulnerable to spyware and viruses.
- The Windows Mail App will not be able to retrieve mail and will not sync with the PC user's mail.
- The user can be doing anything on their computer and the error code will show up unprompted.
- The computer will lock up, become slow, crash, or even freeze when dealing with error code 0x80070426.
- The programs from an older version of Windows do not replace the newer version from Windows 10.
Solution
 Error Causes
Error Causes
Error code 0x80070426 will present itself when a PC user has upgraded their OS from a previous version of Windows to the new Windows 10 version. When this happens, a small portion of users will experience the disconnect between older versions of specific programs, namely the virus protection. When the previous version of the program under a different name is not completely removed and the new virus protection program is installed, the programs will cancel each other out and collectively offer no protection.
This error code may also be found when Windows 10 tries to sync the user's email with the Windows Mail App.
Further Information and Manual Repair
There are a few methods to repair this problem. It should be noted that should anyone feel that the instructions are too complicated, they should contact a Windows repair technician to ensure that the error is fixed properly.
Method One: Uninstall Microsoft Essentials
Hold down the Windows Key and press R. Type in taskmgr into the run dialogue. You should locate the Windows Defender Service (this may show up as Windefend). Right-click on it and then choose Stop.
This will stop the program, but the program will start back up automatically when the computer restarts. While this program is stopped, uninstall Essentials.
To do this: go to Control Panel, Programs, and Features, Uninstall a Program. Alternately, you may hold down the Windows Key and press R, type in appwiz.cpl, click OK, and then locate Microsoft Essentials. Uninstall it, and then restart your computer.
After this is done, go to Settings, Update, and Security. Choose Windows Defender and ensure that Real-time protection is on. Refer back to the Task Manager, Services. Make sure that Defender service is on and running.
Method Two: If the problem occurs in the Windows Mail App
When error code 0x80070426 presents itself in the form of an error with the Mail app, it may be necessary to run an SFC scan.
Right-click on the Start menu or Windows icon, and select Command prompt. The command prompt may be navigated by using shortcut keys Win and X and then select it.
Run the command prompt and then type in sfc /scannow and then press enter. The SFC scan will be run, and be careful not to abort the process before it has finished. This will scan for any files that are lost or corrupt on the PC.
If the scan has found any corrupt files, type in this code and then hit Enter: findstr /c:”[SR]” %windir%LogsCBSCBS.log >”%userprofile%Desktopsfcdetails.txt.
To skip the repair of corrupt or missing files, type in: Dism /Online /Cleanup-Image /RestoreHealth. The details of the scan can be found on the sfcdetails.txt file that will be on the desktop.
Method Three: Use An Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise,
download and install a powerful automated tool.

 What exactly is TPM?
What exactly is TPM?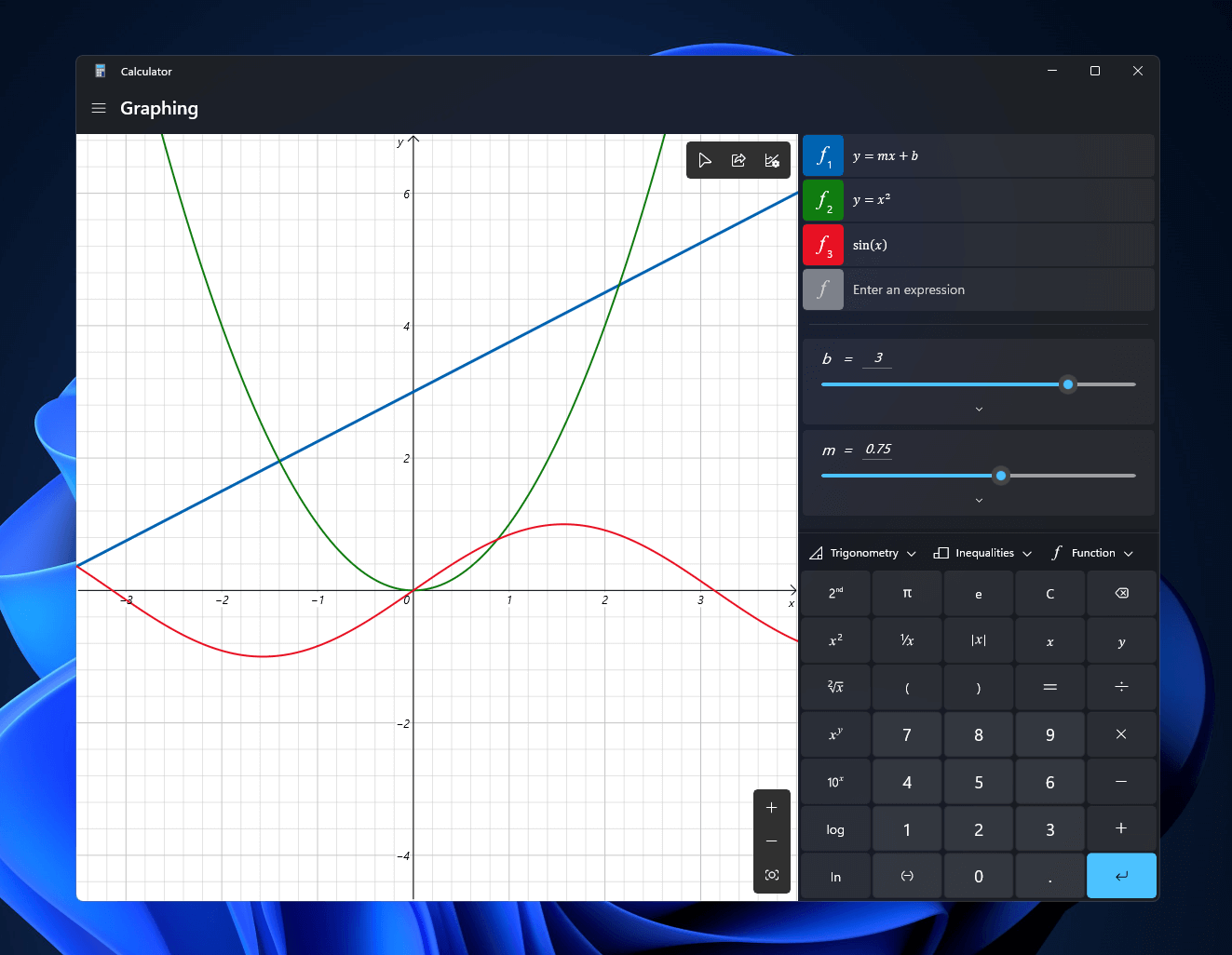 Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
 Error Causes
Error Causes