PrivacyAssistant is a browser extension developed by SearchAssistant.net. These extensions allegedly offer users a safer way to browse the internet and some other tools to customize the home page with background wallpapers and one-click links that can be added. While all this may sound appealing, PrivacyAssistant also monitors your browser activity, search quarries, clicks, visits, and possibly personal information.
This extension changes your default home page to SearchAssistant.com and rerouting all searches through its search portal, displaying sponsored links instead of your typical search results. While active you may see unwanted ads and even pop-up ads appearing while browsing the internet.
Several anti-virus programs have classified this extension as a Browser Hijacker, and are, therefore, for security reasons, not recommended to keep on your computer.
About Browser Hijackers
Browser hijacking is amongst the web’s constant risks that target internet browsers. It’s a kind of malicious software that alters your internet browser’s configuration settings and redirects you to websites or pages that you had no intention of checking out. They are created to disrupt browser functions for many different reasons. Usually, hijackers will force hits to internet sites of their choice either to increase traffic producing higher advertisement earnings, or to gain a commission for each and every user visiting there. Most people believe that these kinds of websites are legitimate and harmless but that is not the case. Almost every browser hijacker poses an existent threat to your online safety and it’s important to categorize them under privacy dangers. When the program attacks your PC, it starts to mess things up a whole that slows your computer down to a crawl. In the worst-case scenario, you might be forced to deal with serious malware threats as well.
How one can recognize a browser hijack
There are numerous symptoms that point to a browser hijacking: your browser’s home page is suddenly different; you get re-directed to sites you never meant to visit; the default web engine has been changed and your web browser security settings have been lowered without your knowledge; find new toolbars that you simply did not add; you might find many pop-up ads on your computer screen; your web browser starts running slowly or displays frequent errors; you have prohibited entry to certain web pages, for example, the website of an antivirus software developer like SafeBytes.
So how exactly does a browser hijacker infect a PC
Browser hijackers may use drive-by downloads or file-sharing websites or perhaps an email attachment in order to reach a targeted computer system. They can also originate from any BHO, extension, toolbar, add-on, or plug-in with malicious intent. Other times you might have unintentionally accepted a browser hijacker as part of a software program bundle (generally freeware or shareware). A good example of some popular browser hijackers includes Conduit, Anyprotect, Babylon, DefaultTab, SweetPage, Delta Search, and RocketTab, however, the names are constantly changing.
Browser hijacking can lead to serious privacy problems and even identity theft, disrupt your browsing experience by taking control over outgoing traffic, considerably slows down your personal computer by consuming lots of system resources, and result in system instability at the same time.
How to repair a browser hijack
Some hijackers can be removed by uninstalling the free software they were included with or by deleting any extension you’ve recently added to your browser. But, the majority of hijackers are extremely tenacious and require specialized applications to eradicate them. Furthermore, manual removal requires you to execute many time-consuming and tricky procedures which are hard to carry out for inexperienced computer users.
How To Get Rid Of Virus That Is Preventing Antivirus Installation?
Viruses can cause a great deal of damage to your computer system. Some malware sits in between the computer and your net connection and blocks some or all sites that you really want to visit. It will also prevent you from installing anything on your computer, especially anti-malware software. So what to do if malicious software keeps you from downloading or installing Safebytes Anti-Malware? Although this sort of problem can be difficult to circumvent, there are some actions you can take.
Make use of Safe Mode to resolve the problem
In Safe Mode, you can actually change Windows settings, un-install or install some software, and eliminate hard-to-delete malware. In case the malware is set to load immediately when PC boots, switching into this mode may well prevent it from doing so. To enter into Safe Mode or Safe Mode with Networking, press F8 while the system is starting up or run MSCONFIG and look for the “Safe Boot” options in the “Boot” tab. Once you’re in safe mode, you can try to install your anti-malware program without the hindrance of the malicious software. Following installation, run the malware scanner to remove most standard infections.
Switch over to some other web browser
Some malware mainly targets specific browsers. If this is your situation, use another internet browser as it can circumvent the malware. In the event you suspect that your Internet Explorer has been hijacked by a computer virus or otherwise compromised by cybercriminals, the best approach is to switch over to a different internet browser like Mozilla Firefox, Google Chrome, or Apple Safari to download your favorite computer security program – Safebytes Anti-Malware.
Run anti-virus from a USB drive
Another solution is to create a portable anti-malware program on your USB thumb drive. Try these simple actions to clean up your affected PC using a portable antivirus.
1) Download Safebytes Anti-Malware or Microsoft Windows Defender Offline onto a clean computer system.
2) Plug the pen drive into the uninfected PC.
3) Run the setup program by double-clicking the executable file of the downloaded application, which has a .exe file format.
4) Choose the flash drive as the location for saving the file. Follow the on-screen instructions to complete the installation process.
5) Transfer the pen drive from the uninfected computer to the infected computer.
6) Double-click the EXE file to open the Safebytes tool from the pen drive.
7) Click “Scan Now” to run a scan on the infected computer for viruses.
A Look at the Best AntiMalware Program
If you are looking to download an anti-malware application for your computer, there are several tools out there to consider nonetheless, you cannot trust blindly anyone, no matter whether it is paid or free software. Some are really worth your money, but many aren’t. While looking for an anti-malware program, choose one that offers solid, efficient, and complete protection against all known computer viruses and malware. One of the highly recommended software is SafeBytes AntiMalware. SafeBytes carries a very good track record of quality service, and customers appear to be happy with it.
SafeBytes anti-malware is really a powerful, very effective protection tool created to assist users of all levels of IT literacy in finding and eliminating malicious threats out of their PC. Once you’ve got installed this software, SafeByte's state-of-the-art protection system will make sure that no viruses or malicious software can seep through your PC.
SafeBytes anti-malware comes with a plethora of enhanced features which sets it aside from all others. Listed below are some of the highlighted features included in the tool.
Robust Anti-malware Protection: This deep-cleaning anti-malware software goes much deeper than most anti-virus tools to clean your computer. Its critically acclaimed virus engine finds and disables hard to remove malware that conceals deep inside your personal computer.
Active Protection: SafeBytes gives round-the-clock protection for your PC limiting malware attacks in real-time. They’re extremely effective in screening and removing various threats since they’re constantly improved with the latest updates and alerts.
Web protection: SafeBytes checks the links present on a web page for possible threats and alerts you whether the website is safe to explore or not, through its unique safety ranking system.
Light-weight: The program is lightweight and will work quietly in the background, and that does not impact your computer efficiency.
24/7 Premium Support: Support service is readily available for 24 x 7 x 365 days through email and chats to answer your queries.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove PrivacyAssistant without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by PrivacyAssistant
Registry:
HKLMSOFTWAREClassesAppID.exe
HKEY_CURRENT_USERsoftwareMicrosoftInternet ExplorerMainStart Page Redirect=http://.com
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionvirus name
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionWinlogon Shell = %AppData%.exe
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun Random HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionRandom
HKEY_LOCAL_MACHINESOFTWAREsupWPM
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesWpm
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionUninstallPrivacyAssist
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmsseces.exe
HKLMSOFTWAREClassesAppIDrandom.exe
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain Default_Page_URL
 Error Causes
Error Causes
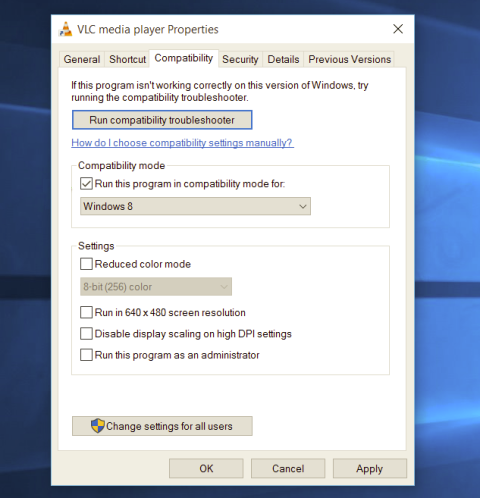 Most of the time running applications with typical settings is fine but from time to time we might have some applications that will require running with administrator privilege in order to work properly. In this case, it is very easy to do it, you just right-click and choose run as administrator.
Although a very easy solution, it can be quite annoying if running the app is on a daily basis or even more times per day. If this is the case then right-clicking and choosing to run as administrator can be a daunting task, sometimes you can even forget to run it like this in heat of work and some unforeseen consequences might occur.
Luckily there is an easy hack so you can open the chosen application each time as an administrator with a simple double click each time.
Most of the time running applications with typical settings is fine but from time to time we might have some applications that will require running with administrator privilege in order to work properly. In this case, it is very easy to do it, you just right-click and choose run as administrator.
Although a very easy solution, it can be quite annoying if running the app is on a daily basis or even more times per day. If this is the case then right-clicking and choosing to run as administrator can be a daunting task, sometimes you can even forget to run it like this in heat of work and some unforeseen consequences might occur.
Luckily there is an easy hack so you can open the chosen application each time as an administrator with a simple double click each time.


 Razer had some strange dives into stuff not really aimed at gamers and the gaming community overall like its Zephir smart mask and now it is venturing into the area of smartwatches teaming up with Fossil. I am not clear if this initiative was set in motion by Razer or Fossil and I really do not know why limited production numbers. Officially named RAZER X FOSSIL GEN 6 SMARTWATCH, this watch comes with the official following text on Razer's page:
Razer had some strange dives into stuff not really aimed at gamers and the gaming community overall like its Zephir smart mask and now it is venturing into the area of smartwatches teaming up with Fossil. I am not clear if this initiative was set in motion by Razer or Fossil and I really do not know why limited production numbers. Officially named RAZER X FOSSIL GEN 6 SMARTWATCH, this watch comes with the official following text on Razer's page:
